
Related Topics
Set up a VPN from a Firebox to a SonicWALL Device
A branch office virtual private network (BOVPN) tunnel is a secure way for networks, or for a host and a network, to exchange data across the Internet. This topic tells you how to define a manual BOVPN tunnel between a Firebox and a SonicWALL Security Appliance (SonicOS Enhanced 6.2.4.0-14n). Before you create a BOVPN tunnel, you must collect the IP addresses from each endpoint and decide which common tunnel settings to use.
This topic does not give detailed information on what the different BOVPN settings mean, or the effects those settings can have on the tunnel that is built. If you want to know more about a particular setting, use these resources:
WatchGuard provides interoperability instructions to help our customers configure WatchGuard products to work with products created by other organizations. If you need more information or technical support about configuring a non-WatchGuard product, see the documentation and support resources for that product.
VPN Configuration Summary
For reference purposes, here is a summary of the VPN configuration defaults for the SonicWALL Network Security Appliance, with emphasis on any settings that do not match the default VPN configuration settings in Fireware v11.12.4.
In Fireware v12.0 and higher, the default BOVPN security settings are different. To determine whether those settings are compatible with your SonicWALL device, see the documentation for your SonicWALL device.
| VPN Settings | WatchGuard Device Default (v11.12.4) | SonicWALL Device Default | Matched? |
|---|---|---|---|
| Phase 1 Settings | |||
| IKE Exchange Mode | IKEv1, Main | IKEv2 | N |
| Authentication | SHA1 | SHA1 | Y |
| Encryption | 3DES | 3DES |
Y |
| Diffie-Hellman Group | 2 | 2 | Y |
| Phase 2 Settings | |||
| Perfect Forward Secrecy | No | No | Y |
| Protocol | ESP | ESP | Y |
| Authentication | SHA1 | SHA1 | Y |
| Encryption | AES (256-bit) | 3DES | N |
WatchGuard and SonicWALL devices have different default settings for the Phase 1 IKE exchange mode and Phase 2 encryption. For the VPN tunnel to build successfully, you must specify the same Phase 1 and 2 settings on your Firebox and SonicWALL devices.
For the strongest security, we recommend that you change the default settings on the Firebox and SonicWALL devices to specify an AES variant.
Collect IP Address and Tunnel Settings
Before you can configure a branch office VPN, you must collect the public IP addresses of each device, and the IP addresses of the private networks you want to connect. You must also decide which Phase 1 and Phase 2 settings to use for the VPN. This procedure describes how to configure a Firebox with the Phase 1 and Phase 2 settings that match the default settings on a SonicWALL device.
For example, the IP address settings you collect could look like this:
WatchGuard Firebox:
External interface IP address: 203.0.113.2
Trusted network IP address: 10.0.1.0/24
SonicWALL device:
External interface IP address: 198.51.100.2
Private network IP address: 10.50.1.0/24
Configure the Firebox
On the Firebox, add a VPN Gateway and a VPN tunnel that uses that gateway.
Add the VPN Gateway
- Select VPN > Branch Office VPN.
- Below the Gateways list, click Add.
The New Gateway page appears. - Select Use Pre-Shared Key. Type the shared key.
The shared key must use only standard ASCII characters. It must match the key used on the SonicWALL device. - Below the Gateway Endpoint list, click Add.
The Gateway Endpoint Settings dialog box appears.

- From the External Interface drop-down list, select the external interface has the public IP address.
- Select By IP Address. Type the external (public) IP address for the Firebox.
- Select the Remote Gateway tab.
- In the Specify the remote gateway IP address for a tunnel section, select Static IP Address. Type the external (public) IP address of the SonicWALL device.
- In the Specify the remote gateway ID for tunnel authentication section, select By IP Address. Type the public IP address of the SonicWALL device.
- Click OK to close the Gateway Endpoint Settings dialog box.
There is no need to change any of the Phase 1 settings on the Firebox. For this configuration, you change the Phase 1 settings on the SonicWALL device to match the Firebox device.
- In Policy Manager, select VPN > Branch Office Gateways. Click Add.
The New Gateway dialog box appears. - In the Gateway Name text box, type a name to identify this gateway in Policy Manager.
- Select Use Pre-Shared Key. Type the shared key.
The shared key must use only standard ASCII characters. It must match the key used on the SonicWALL device. - In the Gateway Endpoints section, click Add.
The New Gateway Endpoints settings dialog box appears.

- From the External Interface drop-down list, select the external interface that has the public IP address you typed.
- In the Local Gateway section, select By IP Address. Type the external (public) IP address for the Firebox.
- In the Specify the remote gateway IP address for a tunnel section, select Static IP Address. Type the external (public) IP address of the SonicWALL device.
- In the Specify the gateway ID for tunnel authentication section, select By IP Address. Type the public IP address of the SonicWALL device.
- Click OK.
The gateway endpoint pair you defined appears in the list of gateway endpoints. - Click OK again to add the configured gateway.
There is no need to change any of the Phase 1 settings on the Firebox. For this configuration, you change the Phase 1 settings on the SonicWALL device to match the Firebox device.
Add the VPN Tunnel
After you define the gateway, you can add tunnels. In this step, you will create a branch office tunnel configuration with the routes (local and remote endpoints for the tunnel)
- Select VPN > Branch Office VPN.
- In the Tunnels section, click Add.
- In the Name text box, type a meaningful name for this tunnel.
- From the Gateway drop-down list, select the gateway you configured to the SonicWALL device.
- Below the Addresses list, click Add.
The Tunnel Route Settings dialog box appears. - In the Local IP settings, from the Choose Type drop-down list, select Network IPv4. Type the network IP address for the local network that you want to use the VPN tunnel.
- In the Remote IP settings, from the from the Choose Type drop-down list, select Network IPv4. Type the network IP address for the private network on the SonicWALL device that you want to use the VPN tunnel.
- Click OK to add the tunnel route.

- Select the Phase 2 Settings tab.
- If the Enable Perfect Forward Secrecy check box is selected, clear it.
- In the IPSec Proposals list, verify that the default ESP-AES-SHA1 proposal appears.
- Click Save.
- Select VPN > Branch Office Tunnels.
- Click Add.
- In the Name text box, type a meaningful name for this tunnel.
- From the Gateway drop-down list, select the gateway you configured to the SonicWALL device.
- Click Add.
The Tunnel Route Settings dialog appears. - In the Local text box, type the network IP address for the local network that you want to use the VPN tunnel.
- In the Remote text box, Type the network IP address for the private network on the SonicWALL device that you want to use the VPN tunnel.
- Click OK to add the tunnel route.

- Select the Phase 2 Settings tab.
- If the Perfect Forward Secrecy check box is selected, clear it.
- In the IPSec Proposals list, verify that the default ESP-AES-SHA1 proposal appears.
- Click OK.
- Save this configuration to the Firebox.
Configure the SonicWALL Device
This procedure describes how to manually configure the VPN settings for the SonicWALL device.
In the SonicWALL web-based management interface:
- Select VPN > Settings.

- In the VPN Policies section, click Add.
The VPN Policy dialog box appears.
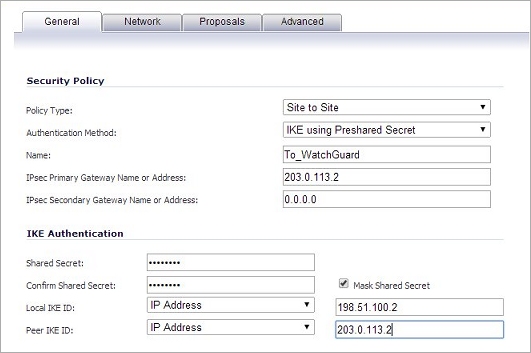
- From the Policy Type drop-down list, confirm that Site to Site is selected.
- In the Name text box, type a meaningful name for the connection.
- In the IPsec Primary Gateway Name or Address text box, type the external IP address for the Firebox.
- In the Shared Secret and Confirm Shared Secret text boxes, type the pre-shared key you used on the Firebox.
- In the Local IKE ID text box, type the external IP address for the SonicWALL device.
- In the Peer IKE ID text box, type the external IP address for the Firebox.
- Select the Network tab.

- From the Choose local network from list drop-down list, select Create new address object.
The Add Address Object dialog box appears.

- In the Name text box, type a meaningful name for this address object.
- From the Type drop-down list, select Network.
The IP Address text box is replaced by text boxes for Network and Netmask. - In the Network text box, type the subnet ID for the private network IP address of the SonicWALL device.
- In the Netmask text box, type the subnet mask for the private network IP address of the SonicWALL device.
- Click OK.
In our testing with the Chrome browser, the Add Address Object dialog box failed to close correctly at this point. We did not experience this problem with Internet Explorer.
- From the Choose remote network from list drop-down list, select Create new address object.
The Add Address Object dialog box appears. - In the Name text box, type a meaningful name for this address object.
- From the Type drop-down list, select Network.
The IP Address text box is replaced by text boxes for Network and Netmask. - In the Network text box, type the subnet ID for the private network IP address of the Firebox.
- In the Netmask text box, type the subnet mask for the private network IP address of the Firebox.
- Click OK.
- Select the Proposals tab.

- From the Exchange drop-down list, under IKE (Phase 1) Proposal, select Main.
- In the IPSec (Phase 2) Proposal section, in the Encryption drop-down list, select AES (256-bit).
- Click OK to complete the VPN configuration.
After you have configured the VPN on both devices, you can try to send traffic through the tunnel as a test of the VPN.