
Related Topics
Manage Device Certificates (Web UI)
You can use Fireware Web UI to see and manage your Firebox certificates. This includes:
- See a list of the current device certificates and their properties
- Update Trusted CA certificates
- Remove a certificate from the device
- Import a certificate or CRL
- Export a certificate for re-signing or distribution
- Create a certificate signing request (CSR)
- Select a web server certificate for Firebox authentication
- Select a certificate to use with a Branch Office VPN or Mobile User VPN
When you import, update, or delete a certificate on a FireCluster member, the change automatically synchronizes to the other FireCluster member. You do not need to import separate certificates for FireCluster members.
See Current Certificates
To see the current list of certificates:
- Select System > Certificates.
The Certificates list appears, with all the certificates and certificate signing requests (CSRs).
The Certificates list includes:
- The status and type of the certificate.
- The algorithm used by the certificate.
- The subject name or identifier of the certificate.
To view a certificate, select the certificate, then click Details.
By default, trusted CA certificates are not included in this list.
- To show all of the certificates from trusted CAs, select the Show Trusted CAs for Proxies check box.
- To hide the trusted CA certificates, clear the Show Trusted CAs for Proxies check box.
Remove a Certificate
When you remove a certificate, it can no longer be used for authentication. If you remove one of the automatically generated certificates, such as the self-signed certificate used by default for the proxy, your Firebox creates a new self-signed certificate for this purpose the next time it reboots. The device does not create a new self-signed certificate automatically if you have imported a different certificate.
The Proxy Authority certificate must not be removed and left with no certificate. The Firebox automatically replaces the missing certificate with a default certificate if the device restarts.
To remove a certificate from the device:
- Select the certificate in the Certificates dialog box.
- Click Remove.
The Remove Certificate dialog box appears. - Click OK.
The Certificate is deleted.
Update Trusted CA Certificates
Your Firebox can automatically get new versions of the trusted CA certificates stored on the device and automatically install the new certificates. This update makes sure that all the trusted CA certificates on your device are the latest version. Any expired certificates are updated, and new trusted CA certificates are added to your device. The updated certificates are downloaded from a secure WatchGuard server. The device checks for updates every 48 hours.
To enable automatic updates, select the Enable automatic updates of CA certificates check box.
Click Update Now to update your trusted CA certificates immediately.
Import a Certificate from a File
You can import a certificate from the Windows clipboard or from a file on your local computer. Certificates must be in Base64 PEM encoded format or PFX file format.
Before you import a certificate to use with the proxy content inspection feature, you must import each previous certificate in the chain of trust of the type Other. Start with the root CA certificate and proceed to the end entity certificate, in that order.
To import a CA certificate for your Firebox to use to validate other certificates when they are imported and create a chain of trust, make sure to select the IPSec, Web Server, Other category when you import the CA certificate and do not include the private key.
About PFX Files
A PFX certificate bundle contains all the required certificates and private key, and is uploaded as a single file.
To use a PFX bundle for HTTPS content inspection, you must have two PFX files:
- The first proxy authority PFX file must have the root CA certificate that issued the proxy authority certificate, and the proxy authority certificate with its private key.
- The second proxy server PFX file must have the proxy authority certificate, and the proxy server certificate with its private key.
For more information, see About Certificates, Use Certificates with HTTPS Proxy Content Inspection, and SMTP-Proxy: TLS Encryption.
Import Certificate
To import a certificate file:
- Select System > Certificates.
The Certificates page appears. - Click Import Certificate/CRL.
- Select the Import a Certificate tab.
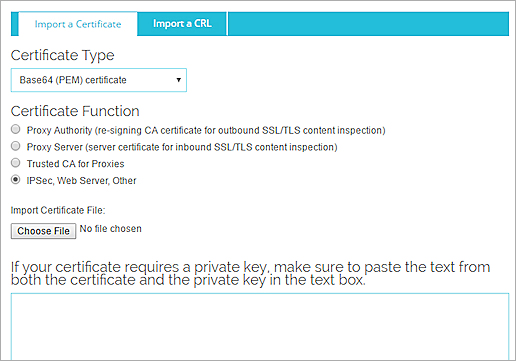
- From the Certificate Type drop-down list, select the Base64 (PEM) certificate or PFX file type.
- Select the option that matches the function of the certificate:
- Proxy Authority (re-signing CA certificate for outbound SSL/TLS content inspection) — Select this option if the certificate is for a proxy policy that manages web traffic requested by users on trusted or optional networks from a web server on an external network. A certificate you import for this purpose must be a CA certificate. Before you import the CA certificate used to re-encrypt traffic with a proxy, make sure the CA certificate used to sign this certificate was imported with the Other category.
- Proxy Server (server certificate for inbound SSL/TLS content inspection) — Select this option if the certificate is for a proxy policy that manages web traffic requested by users on an external network from a web server protected by the Firebox. Before you import the CA certificate used to re-encrypt traffic from a web server, make sure the CA certificate used to sign this certificate was imported with the Other category .
- Trusted CA for Proxies — Select this option for a certificate used to trust traffic that is not re-encrypted by a proxy. For example, a root certificate or intermediate CA certificate used to sign the certificate of an external web server.
- IPSec, Web Server, Other — Select this option if:
- The certificate is for authentication, is a device IPSec certificate, or is a CA certificate.
- You want to import a CA certificate for your Firebox to use to validate other certificates when they are imported and create a chain of trust. Make sure you do not include the private key when you import the CA certificate.
- If you selected Base64 (PEM) certificate as the Certificate Type, you can load the certificate from a file, or copy and paste the PEM certificate contents in the text box. If the certificate includes a private key, type the password to decrypt the key.
If you selected PFX file as the Certificate Type, type the PFX File Password, and click Browse to select the PFX file to upload.
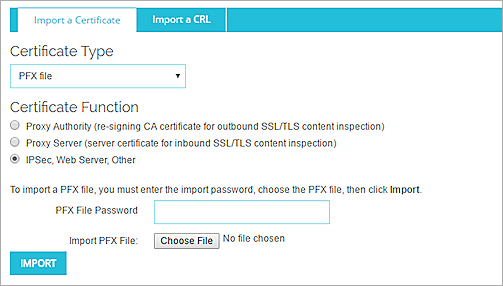
- Click Save.
The certificate is added to the Firebox.
Import a CRL from a File
You can import a certificate revocation list (CRL) that you have previously downloaded from your local computer. CRLs are used only to verify the status of certificates used for VPN authentication. Certificates must be in PEM (base64) encoded format.
- Click Import Certificate/CRL.
- Select the Import a CRL tab.
- Click Browse and find the file.
- Click Import.
The Import CRL dialog box appears. - Click OK.
The CRL you specified is appended to the CRL on your device.
Export a Certificate
You can export a certificate for re-signing by a trusted CA, or for distribution to clients on your network. The certificate is saved in PEM format.
Select a certificate and click Export.
Create a Certificate Signing Request (CSR)
To create a certificate signing request:
- Click Create Request.
The Certificate Request Wizard starts. - Click Next.
- Select the purpose of the completed certificate.
- If the certificate is to be used to re-encrypt inspected content with an HTTPS proxy, select Proxy Authority (re-signing CA certificate for outbound SSL/TLS content inspection).
- If the certificate is to be used to re-encrypt content for a protected web server with an HTTPS proxy, select Proxy Server (server certificate for inbound SSL/TLS content inspection).
- For all other uses, including VPN, Firebox, or Management Server authentication, select IPSec, Web Server, Other.
- Click Next.
- Type the device name (the host and domain name such as host.example.com), the department the device belongs to, the name of the company the device belongs to, and the city, state or province, and country. These entries are used to create the subject name.
- Click Next.
The wizard creates a subject name based on what you entered in the previous screen. - Type the appropriate information in the DNS Name, IP Address, and User Domain Name text boxes.
- Click Next.
- By default, the certificate uses RSA encryption, 2048-bit key length, and both encryption and signatures for key usage. Click Next.
HTTPS proxy authority and HTTPS proxy server certificates do not have options for key usage. - The finished CSR is displayed.
You must send this CSR to a certificate authority for signing before you can use it with your Firebox. When you import the finished certificate, you must first import the CA certificate used to sign the new certificate with the Other category. - Click Finish and Import to import a certificate.
The Import Certificate/CRL dialog box appears. - Click Finish to close the wizard.
Use a Web Server Certificate for Authentication
To use a third-party certificate for authentication, you must first import that certificate. See the previous procedure for more information. If you use a custom certificate signed by the Firebox, we recommend that you export the certificate and then import it on each client device that connects to the Firebox.
- Select Authentication > Web Server Certificate.
The Authentication Web Server Certificate page appears. - To use a previously imported third-party certificate, select Third party certificates and select the certificate from the drop-down list.
Click Save and do not complete the other steps in this procedure. - To create a new certificate for Firebox authentication, select Custom certificate signed by Firebox.
- In the text box at the bottom of the dialog box, type the domain name or IP address of an interface on your Firebox. Click Add.
When you have added all the domain names, click OK. - Type the Common name for your organization. This is usually your domain name.
Or, you can also type an Organization name and an Organization unit name (both optional) to identify what part of your organization created the certificate. - Click Save.
See Also
Certificates for Mobile VPN With IPSec Tunnel Authentication
Certificates for Branch Office VPN (BOVPN) Tunnel Authentication