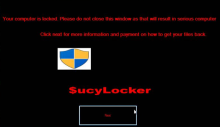
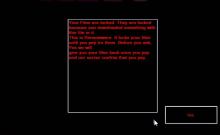
$ucyLocker is not a Locker, as the name would suggest. Instead, $ucyLocker is a crypto-ransomware derived from the Hidden Tear project. Hidden Tear is an open-source repository on GitHub of customizable ransomware someone can pull, customize, and deploy. The authors of $ucyLocker, or its known alias, VapeHacksLoader, did just that in June of 2017 when it was first discovered. The authors customized the ransomware to overlay a simple black screen with instructions for their victims in red. Like Hidden Tear, this ransomware uses AES-256-CBC encryption to encrypt the files, including a salt. The authors then demand .16 Bitcoin (BTC) in exchange for the decryption of files, which isn't guaranteed. Since the ransomware was deployed in June of 2017, the extortion price of .16 BTC amounts to roughly $400 at the time of $ucyLocker's creation.
Open main menu

-
Solutions
-
Products & Services
-
Resources
-
Help Me Research
-
Webinars
-
White Papers
-
Datasheets & Brochures
-
Case Studies
-
All Resources
›
-
Help Me Choose
-
UTM vs NGFW
-
WatchGuard Appliance Sizing Tool
-
Compare WatchGuard Appliances
- Find an Integration
-
-
Partners
-
Become a Partner
-
Channel Partner Program
-
Benefits for the MSP
-
Getting Started as a Partner
-
Join the WatchGuardONE Program
-
Partner Resources
-
WatchGuard Cloud for Partners
-
Unified Security Platform for Partners
-
Specializations & Certifications
-
Partner Tools
-
Partner Success Stories
-
Find A Partner
-
Find a Reseller
-
Find a Distributor
-
-
News
-
Support
-
Try Now