$$$
Aliases
LokerAdmin
Triple Dollar Signs
Description
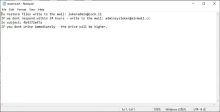
The $$$ Crypto-Ransomware, or LokerAdmin, was discovered at the beginning of 2020 and is known to have used the .$$$, .texyz, and .8NWm8Y file extensions when encrypting files using the Salsa20 stream cipher. The ransom note dropped asks victims to email the ransomware operators directly with a unique code based on the victim's machine. Because the operators request direct communication, their method of payment is unknown. Although it is believed to be in a form of cryptocurrency.
Ransomware Type
Crypto-Ransomware
First Seen
Last Seen
Extortion Types
Direct Extortion
Extortion Price Increases
Communication(6)
Mittel
Bezeichner
Email
adminsysloker@airmail.cc
Email
behappywithyourdata@airmail.cc
Email
happydataowner@firemail.cc
Email
LeJetepreY0@cock.li
Email
lokeradmin@cock.li
Email
UneGarc0n1@cock.li
Encryption
Type
Symmetric
Files
AES-256
File Extension
<file name>.$$$
<file name>.<5 character alphanumeric string>
<file name>.<6 character alphanumeric string>
Ransom Note Name
readme.txt
Ransom Note Image
Samples (SHA-256)
d44df8fc28ccfa08c75e9965b3cc145d82111137e70b96946331e113ec6dd0b9
References & Publications
BleepingComputer Forums: $$$ LokerAdmin Ransomware (.$$$, random 5-6 char ext) Support Topic
PCrisk: $$$ Ransomware
The Crypto-Ransomware Digest: $$$, LokerAdmin