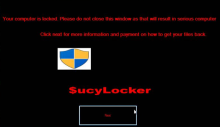
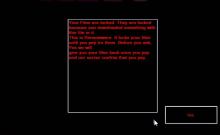
$ucyLocker is not a Locker, as the name would suggest. Instead, $ucyLocker is a crypto-ransomware derived from the Hidden Tear project. Hidden Tear is an open-source repository on GitHub of customizable ransomware someone can pull, customize, and deploy. The authors of $ucyLocker, or its known alias, VapeHacksLoader, did just that in June of 2017 when it was first discovered. The authors customized the ransomware to overlay a simple black screen with instructions for their victims in red. Like Hidden Tear, this ransomware uses AES-256-CBC encryption to encrypt the files, including a salt. The authors then demand .16 Bitcoin (BTC) in exchange for the decryption of files, which isn't guaranteed. Since the ransomware was deployed in June of 2017, the extortion price of .16 BTC amounts to roughly $400 at the time of $ucyLocker's creation.
Ransomware - $ucyLocker
$ucyLocker
Aliases
VapeHacksLoader
Description
Ransomware Type
Crypto-Ransomware
First Seen
Last Seen
Lineage
Extortion Types
Direct Extortion
Extortion Amounts
Amount
0.16BTC($384)
Encryption
Type
Symmetric
Files
AES-256-CBC
Crypto Wallets
Blockchain Type
Crypto Wallet
BTC
1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M
File Extension
<file name>.WINDOWS
Ransom Note Name
READ_IT.txt
Ransom Note Image
Samples (SHA-256)
86e0eac8c5ce70c4b839ef18af5231b5f92e292b81e440193cdbdc7ed108049f
References & Publications
MalwareTips: The $ucyLocker ransomware