For a more extensive analysis, see our publication on Secplicity: Dr. Joseph L. Popp Jr. and The First-Ever Ransomware – The AIDS Trojan
The AIDS Trojan, or PC Cyborg, is commonly referred to as the first-ever ransomware. Because of this, Dr. Joseph Popp, the author of the AIDS Trojan, is known as "the father of ransomware." Appearing in December of 1989, Popp's ransomware differed from modern ransomware in many ways. Most obviously, it was "deployed" as a floppy disk and sent by postal mail from a London location. Once inserted into a system, the floppy disk hijacks AUTOEXE.BAT and alters it to count the number of reboots of the system. Once the counter reached 90, the program would prompt the user to renew a license to continue using the system. A technical analysis by Jim Bates in the 1990 January issue of Virus Bulletin revealed that the program, written in QUICKBASIC 3.0, also encrypted file names (not the files themselves), hid directories, and dropped a ransom note (the license renewal). Bates quickly created a removal tool to remove the AIDS Trojan called AIDSOUT and a program that allowed victims to retrieve hidden directories called AIDSCLEAR. With the help of his colleague, John Sutcliffe, they deciphered the encryption algorithm (a simple, symmetric substitution cipher) and created the first-ever ransomware decryptor called CLEARAID.
Dr. Joseph Popp was born in Ohio and was a Harvard-educated biologist who did much work in Kenya. This is where part of the program - a survey on the susceptibility to contracting the AIDS virus - is believed to have been developed. Further tests of the AIDS Trojan were discovered in Geneva at the World Health Organization (WHO) headquarters. The floppy disks themselves, around 26,000 in total, were sent out to a reported 90 countries by postal mail from London to people who were subscribed to the same science-related magazines and members of the WHO. The ransom note demanded victims send $189 for one year of the license, or $378 for lifetime access, to a P.O. Box in Panama. This amounts to around $400 and $800, respectively, today. No one is reported to have ever paid the extortion except for investigators to see what would happen. Popp was quickly arrested for his crime, although he never faced prison. It is believed that Popp sent out floppy disks in the United Kingdom because they didn't have computer misuse laws, and this was noticed quickly because Popp's actions were the impetus for the Computer Misuse Act of 1990. Based on the known knowledge of the incident, it could be said that the first ransomware had connections to the United States, Kenya, Switzerland, Panama, and the United Kingdom.
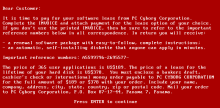
Ransom note picture derived from G DATA.
Known Victims(9)
| Industry Sector | País | Extortion Date | Amount (USD) |
|---|---|---|---|
| Insurance | Belgium | $189 | |
| Education | Italy | $189 | |
| Healthcare & Medicine | Italy | $189 | |
| Healthcare & Medicine | Sweden | $189 | |
| Banking & Finance | United Kingdom | $189 | |
| Education | United Kingdom | $189 | |
| Government | United Kingdom | $189 | |
| Electronics | Zimbabwe | $189 | |
| Healthcare & Medicine | United Kingdom | $189 |