Hidden Tear is the first well-known open-source ransomware published on GitHub in August 2015. Security researcher Utku Sen created it for educational purposes but quickly became uncontrollable. He created Hidden Tear and its successor, EDA2, but, by his admission, was being used by threat actors who had tweaked the source code not to include a backdoor to decrypt files. Unfortunately, the repository got cloned and has been hosted on various other repositories for anyone to use and edit. Therefore, threat actors still use variants of this ransomware to attack victims.
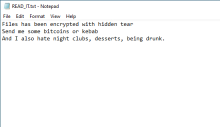
Since this is open source and configurable, there's no specific sample or hash. Although you could build the program as-is and create an executable if you wanted, as is the sample hash shown in the details below. The default ransom note name is READ_IT.txt, and the encryption type is AES-256-CBC. The repository included a solution for a decryptor tool, but that's only if the initial configuration remains relatively unchanged. If a threat actor were to pull the repository and tweak the encryption algorithm, the decryptor likely wouldn't work. Please see the References & Publications section at the bottom of this page for more information on this ransomware.