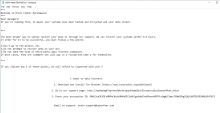
Brain Cipher is a ransomware operation utilizing the leaked LockBit 3.0 (Black) builder for its encryptor. This encryptor hasn't been tweaked much and uses the same encryption type - Salsa20 to encrypt files and RSA-1024 to encrypt the Salsa20 key. Additionally, the encrypted files follow the same format as LockBit 3.0 too, changing encrypted file's names to a seven alphanumeric character sequence followed by a nine alphanumeric character file extension.
They first came known after extorting the Indonesian government in mid-June 2024 and demanded an $8 million ransom. Although, we've observed extortions in the lower six figures. This suggests they aren't consistently demanding exorbitant ransom demands. Although, the subset of evidence for this claim is still small. We managed to get one of the BTC wallet addresses from the operators and it never had any transactions, which means it's possible the group isn't receiving as many funds as they would like. It's not uncommon for these threat actors to use several different wallets in these types of attacks.
Known Victims(13)
| Industry Sector | Pays | Extortion Date | Amount (USD) |
|---|---|---|---|
| Government | Indonesia | 131000000000 IDR($8,000,000) | |
| Manufacturing | United States | ||
| Consulting | United States | ||
| Professional Services | United States | ||
| Banking & Finance | Israel | ||
| Engineering Services | United States | ||
| Healthcare & Medicine | France | ||
| Information Technology | Portugal | ||
| Retail & Wholesale | Venezuela | ||
| Legal | Israel | ||
| Insurance | Ghana | ||
| Hospitality & Leisure | France | ||
| Conglomerate | Thailand |