
Related Topics
Use Authentication to Restrict Incoming Connections
One function of the authentication settings on your Firebox is to restrict outgoing connections. You can also use authentication to restrict incoming network connections. When you have a user account on the Firebox, and the Firebox has a public external IP address, you can authenticate to the Firebox from a computer external to the Firebox network. For example, you can type this address in your web browser to authenticate: https://<IP address of the Firebox external interface>:4100/.
For greater security, we recommend these settings in the WatchGuard Authentication policy:
- In the From list, specify which IP addresses, ranges, or networks your users connect from. Keep the default aliases Any-Trusted and Any-Optional.
- In the To list, specify the IP addresses for user authentication connections. Tip!You can specify the Firebox alias in the To list. However, keep in mind that this option allows authentication connections to all public and private IP addresses on the Firebox.
After you authenticate, you can connect to the network behind the Firebox, based on the access rules defined in the policies that are configured on the Firebox. For more information about authenticated access, see the Use Authentication for Connections to Internal Resources section.
- Select Firewall > Firewall Policies.
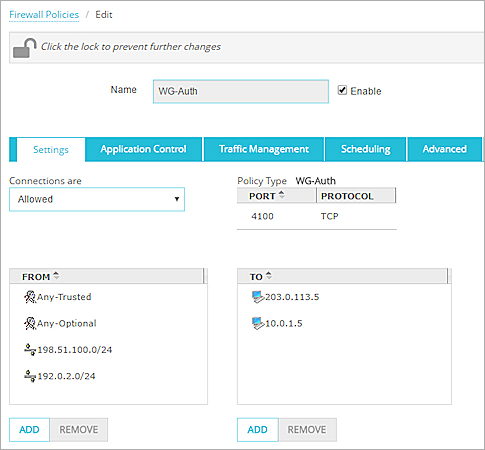
The Firewall Polices Page appears. - Click the WatchGuard Authentication policy (WG-Auth) to edit it.
This policy appears after you add a user or group to a policy configuration.
The Edit page appears. - From the Connections are drop-down list, make sure Allowed is selected.
- In the From section, click Add.
The Add Member dialog box appears. - From the Member type drop-down list, select Alias.
- From the list of members, select Any-Trusted
- Click OK.
- Repeat Steps 4–5. From the list of members, select Any-Optional.
- Repeat Steps 4–5. From the list of members, select an option for external connections.
For example, you can select Network IPv4 and type a network IP address. - In the To section, click Add.
- From the Member type drop-down list, select Alias.
- From the list of members, select an option.
For example, to restrict authentication attempts to a certain IP address, select Host IPv4 and type the IP address. In our example, we allow authentication attempts to an external IP address and an internal IP address. Tip!If you have single sign-on (SSO) configured on your network, you can use the WG-Auth policy as a backup authentication method. In the To list, specify the IP address of your Trusted interface. - Click OK.
- Click Save.
- Open Policy Manager for your device.
- Double-click the WatchGuard Authentication policy. This policy appears after you add a user or group to a policy configuration.
The Edit Policy Properties dialog box appears. - From the WG-Auth connections are drop-down list, make sure Allowed is selected.
- In the From section, click Add.
The Add Address dialog box appears. - From the Available Members list, select Any-Trustedand Any-Optional and click Add.
- Click Add Other.
- From the Choose Type drop-down list, select an option for external connections and click OK.
For example, you can select Network IPv4 and type a network IP address. In our example, we allow authentication attempts from the local network and specified external networks. - Click OK.
- In the To section, click Add.
- From the Available Members list, select Add Other.
- From the Choose Type drop-down list, select an option for external connections and click OK.
For example, you can select Host IPv4 and type an IP address. In our example, we allow authentication attempts to an external IP address and an internal IP address. Tip!If you have single sign-on (SSO) configured on your network, you can use the WG-Auth policy as a backup authentication method. In the To list, specify the IP address of your Trusted interface. - Click OK.

- Click OK to close the Edit Policy Properties dialog box.
Use Authentication for Connections to Internal Resources
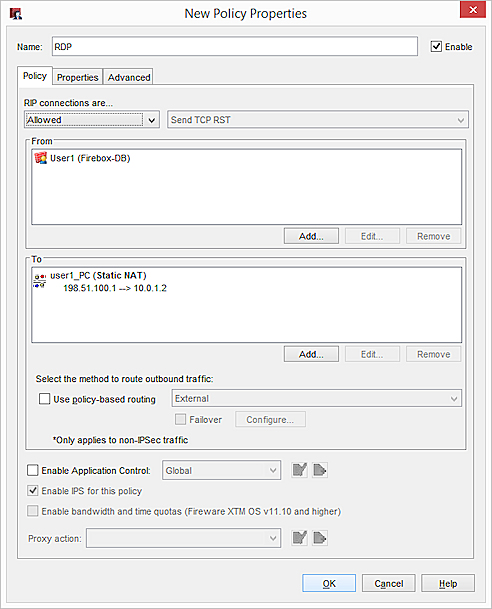
A VPN is the most secure way for users to connect to internal resources. If you cannot connect with a VPN, you can provide authenticated access to internal resources. For example, you can configure an RDP policy that applies only to authenticated users.
Before you begin, make sure the WatchGuard Authentication (WG-Auth) policy allows incoming connections from external users. To enable a remote user to authenticate from an external network, see the previous section.
- Follow the instructions in Configure Static NAT to define a static NAT action.
In our example, the IP addresses are 198.51.100.1 and 10.0.1.2.

- Select Firewall > Firewall Policies.
- Click Add Policy.
- From the Packet Filter drop-down list, select RDP.
- Click Add Policy.
- From the From list, select Any-Trusted and click Remove.
- Click Add.
- From the Member Type drop-down list, click Firewall User.
- Select a user name and click OK.
- From the To list, select Any-External and click Remove.
- Click Add.
- From the Member Type drop-down list, select Static NAT.
- From the adjacent list, select the SNAT that you created.

- Click OK.
- Select Edit>Add Policy.
- Click Packet Filters.
- Select RDP.
- Click Add.
- From the From list, select Any-Trusted and click Remove.
- Click Add User.
- Select a user and click Select.

- From the To list, select Any-External and click Remove.
- Click Add>Add SNAT.
- Follow the instructions in Configure Static NAT to define a static NAT action.
In our example, the IP addresses are 198.51.100.1 and 10.0.1.2.
You now have two polices:
- A WatchGuard Authentication (WG-Auth) policy that allows users to authenticate to the Firebox at https://[external IP address or domain name]:4100
- An RDP policy that allows only User1 to get access the computer at 10.0.1.2 with RDP.
This is just one example of authenticated access. You can add more users, configure policies for different services, and configure access to different networks.
Use Authentication Through a Gateway Firebox
The gateway Firebox is the WatchGuard Firebox that you place in your network to protect your Management Server from the Internet.
For more information, see About the Gateway Firebox.
To send an authentication request through a gateway Firebox to a different device, you must have a policy that allows the authentication connections on the gateway device. If authentication connections are denied on the gateway device, you can add the WG-Auth policy. This policy controls connections on TCP port 4100. You must configure the policy to allow connections to the IP address of the destination device.