
Related Topics
Troubleshoot User Authentication
After you configure authentication for users and groups on your Firebox, you can follow the steps in this topic to troubleshoot authentication issues. These troubleshooting steps apply to any Firebox components that require user authentication, such as:
- Mobile VPN connections
- Policies that use group membership to define the source of traffic
- Dimension reports that include user names
- Single Sign-On (SSO). If SSO does not work for a user, it is important to verify whether manual authentication (a prompt for typed user credentials) works with Active Directory.
To test manual authentication, use a computer on the network protected by the Firebox .
To verify that your Firebox can connect to your Active Directory or LDAP authentication server for user authentication, you can use Fireware Web UI to test the connection between the Firebox and your authentication server. For more information, see Server Connection.
Before You Begin
Before you create a policy to test authentication, confirm that you can browse from the client computer to https://www.watchguard.com and https://www.watchguard.com. Make sure that the client computer uses the Firebox as its default gateway.
Create a Test Policy for Authentication
To test authentication and the ability to configure policies that affect authenticated users, you can configure a policy that denies traffic. Then, verify that the policy operates as expected for connections from authenticated users in a specific group.
For example, you can create an HTTPS policy that denies all connections from users in a specific group. Then, you can test HTTPS connections from an authenticated user in the group to verify that the policy applies to connections from that authenticated user.
Follow these steps to configure an HTTPS deny policy for connections from a user group.
- In Fireware Web UI, select Firewall > Firewall Policies.
The Policies page appears. - Click Add Policy.
The Add Firewall Policy page appears. - From the Packet Filter drop-down list, select HTTPS.
- Click Add Policy.
The Add page appears. The Policy Name field populates with HTTPS. - Change the Policy Name to a descriptive name, such as HTTPS – Test Deny.
- From the Connections are drop-down list, click Denied.
- In the From list, select Any-Trusted. Click Remove.
- Below the From list, click Add.
The Add Member dialog box appears. - From the Member type drop-down list, select Firewall Group.
Or, if you want to test for a specific user instead of a group, select Firewall User.
The list of configured groups or users appears.
If groups or users from your Active Directory server or other external authentication server do not appear, you must add the group name to the Firebox configuration. To do this, select Authentication > Users and Groups. This group name is case-sensitive and must exactly match the group name on your external authentication server.
- If you selected a group, select the group name.
- If you select a user, select the group that the user is a member of.
- Click OK.
The group or user name is added to the From list.
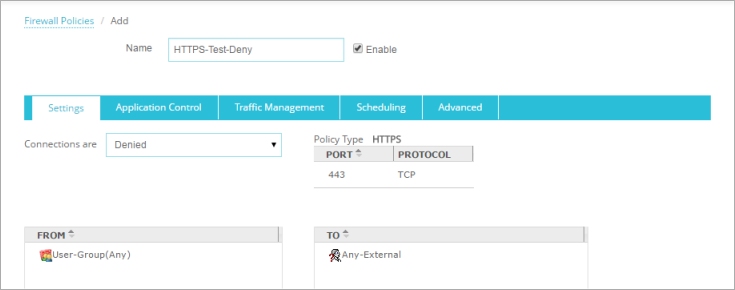
- Click Save to add the policy to your Firebox configuration.
The new policy appears in the Policies page. The WatchGuard Authentication policy is also added automatically if it did not previously exist. - Make sure that no other policy that allows HTTPS connections from this group to Any-External appears higher in the Policies list.
- Open the Firebox configuration in Policy Manager.
- Select Edit > Add Policy.
- From the list of packet filter policies, select HTTPS.
- Click Add.
- In the Name text box, type a descriptive name such as HTTPS-Test-Deny.
- From the HTTPS Connections are drop-down list, click Denied
- In the From list, select Any-Trusted. Click Remove.
- Below the From list, click Add.
The Add Address dialog box appears. - Click Add User.
The Add Member dialog box appears. - From the Type drop-down lists, select Firewall and Group.
Or, if you want to test for a specific user rather than a group, select Firewall and User.
The list of configured groups or users appears.
If groups or users from your Active Directory server or other external authentication server to not appear, you must add the group name to the Firebox configuration. To do this, select Setup > Authentication > Users and Groups. This group name is case-sensitive and must exactly match the group name on your external authentication server.
- Select the group that the user is a member of.
- Click OK.
The group name is added to the From list.
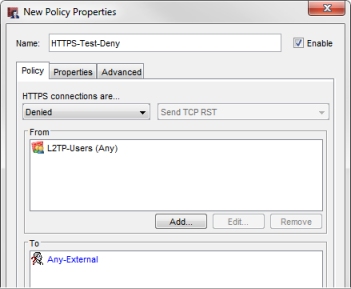
- Click Save to add the policy to your Firebox configuration.
The new policy appears in the Policies page. The WatchGuard Authentication policy is also added automatically if it did not previously exist. - Make sure that no other policy that allows HTTPS connections from this group to Any-External appears higher in the Policies list.
- Save the configuration to the Firebox.
Test User Authentication
Authenticate to the Firebox as a user who is a member of the group you specified in the HTTPS-Test-Deny policy.
- Browse from the client computer to the Firebox authentication portal web page at https://[Firebox interface IP address ]:4100
- If more than one type of authentication is enabled, select the authentication server or domain from the Domain drop-down list.
- Type the Username and Password for the user in the group.
If authentication failed, investigate whether the failure was caused by one of these issues:
Review the user name for the user in the Firebox local users and groups configuration and on the external authentication server. Check for the exact use of upper and lower case and for leading or trailing spaces.
In the authentication server, change the user passphrase to match the passphrase you specified in your test. If you use Firebox-DB for authentication, change this on the Firebox. If you use an external authentication server, change the user's passphrase on the external authentication server.
Review your authentication configuration carefully to match the IP address and other required settings for your authentication server.
- If you use Fireware Web UI to configure users for local Firebox authentication, review the users in Authentication > Servers, and not Authentication > Users and Groups.
- If you use Policy Manager to configure users for local Firebox authentication, review the users in Setup > Authentication Servers, and not Setup > Authentication > Users and Groups.
- If you use Active Directory, make sure you have correctly specified the Active Directory search base. For more information, see Find Your Active Directory Search Base.
After authentication is successful, you are ready to test the connections and policies for an authenticated user.
Log the User Off After Configuration Changes
If you make a change to a user account or group membership as part of troubleshooting, the changes do not affect users who are already authenticated. To test the change, you must log the user out of the Firebox before you log in again to test any configuration change. This makes sure that the Firebox correctly associates the group membership with the user.
- Select System Status > Authentication List.
The Authentication List page appears. - Select the check box next to the user name in the list.
- Click Log Off Users.
- Select the Authentication List tab.
- Right click the user name in the list and select Log Off User.
Test Connections from an Authenticated User
After you create the HTTPS-Test-Deny policy and successfully authenticate to the Firebox as a user who is a member of the group specified in the policy, you can test if the policy successfully denies traffic for the user. This confirms that the group membership operates as expected.
From a web browser on the client computer:
- To test HTTP connections, try to browse to https://www.watchguard.com.
This connection should be allowed, because the test HTTPS-Test-Deny policy does not apply to HTTP traffic. - To test HTTPS connections, try to browse to https://www.watchguard.com.
This should be denied by the HTTPS-Test-Deny policy if the client computer is authenticated as a user that is a member of the group specified in the policy.
If the test policy does not deny the HTTPS request from the authenticated user, investigate to see whether the behavior was caused by one of these issues:
To test whether the policy is correctly configured to deny HTTPS traffic, edit the HTTPS-Test-Deny policy and add the user name to the From list. Then, test the HTTPS connection again.
If the policy denies HTTPS traffic from this user after you add the user name to the policy, that means the policy is configured correctly and the problem is related to group membership. Remove the user name from the policy after this test so that you can use the policy to troubleshoot group membership.
If the policy does not deny HTTPS connections from this user after you add the user name to the policy, either the policy is not correctly configured to deny this traffic, or another policy with higher precedence allows HTTPS connections from this user. Make sure that the policy is set to deny connections, and that no other policies with higher precedence apply to HTTPS connections from this user or to a group this user is a member of.
If the search base specified in the LDAP or Active Directory authentication settings on the Firebox is too specific, it might not include the group name. You can check for the group on your authentication server to see if this is the case.
As a best practice, we recommend that you change the search base in the LDAP or Active Directory authentication settings on the Firebox to simplify the search base to the broadest possible base that works with your authentication server. For example, if your search base is ou=users,dc=example,dc=com, simplify it to dc=example,dc=com.
For more information about Active Directory authentication settings, see Configure Active Directory Authentication
For more information about LDAP authentication settings, see Configure LDAP Authentication.
The group name configured on the Firebox, and used in policies, must exactly match the group name on the external authentication server. Look at the group name on the Firebox and compare it to the group name on the external authentication server. Check the spelling and verify the exact use of upper and lower case and leading or trailing spaces.
If the user is not a member of the group, the policy does not apply to connections from that user. If you use an external authentication server, make sure the user account on the external authentication server is a member of that group. If you use Firebox authentication, make sure the user is a member of the group on the Firebox. The user account must be a member of the group with a group name that exactly matches the group name specified in the policy. Check the spelling and verify the exact use of upper and lower case and leading or trailing spaces.
For RADIUS authentication servers, such as RADIUS and SecurID, group membership is identified by the Filter-ID attribute.
For more information about how to use groups in policies, see Use Users and Groups in Policies.
To verify that the client computer is logged in with the user name you expect, you can search the log messages for requests from the client IP address. At the end of each log message for traffic from an authenticated user, you can see the user name associated with the IP addresses, for example src_user="TestUser@Firebox-DB".
If you find that the IP address is associated with a different user than you expect, investigate whether something else, such as the SSO Agent, SSO Client, or a mobile VPN client is configured to perform user authentication for that client computer.
For more information about Single Sign-On, see About Active Directory Single Sign-On (SSO).
For more information about routing Internet traffic through mobile VPN clients, see Internet Access Options for Mobile VPN Users.