
Related Topics
Virtual Interface IP Addresses for a VPN to a Third-Party Endpoint
If your Firebox runs Fireware OS v11.11 or higher, you can configure a BOVPN virtual interface between your Firebox and a third-party VPN endpoint. Fireware supports two types of BOVPN virtual interface connections to third-party VPN endpoints:
Third-party gateway that supports GRE over IPSec (Fireware v11.11 and higher)
For a Firebox that runs Fireware v11.11 or higher, you can configure a BOVPN virtual interface between your Firebox and a third-party VPN endpoint that supports GRE over IPSec, for example, Cisco, Fortinet, Juniper, or Checkpoint endpoints. The third-party endpoint must terminate the GRE tunnel, not pass the GRE traffic through the IPSec tunnel.
To configure this type of BOVPN virtual interface in Fireware v11.12, set the Remote Endpoint Type to Firebox.
Cloud VPN or third-party gateway without GRE (Fireware v11.12 and higher)
For a Firebox that runs Fireware v11.12 or higher, you can also configure a BOVPN virtual interface between your Firebox and a Cloud VPN or third-party VPN gateway that does not use GRE. Fireware supports connections to cloud-based endpoints that support wildcard traffic selectors, for example, Microsoft Azure.
To configure this type of BOVPN virtual interface in Fireware v11.12 or higher, set the Remote Endpoint Type to Cloud or Third-Party Gateway.
You configure virtual interface IP addresses the same way for either type of BOVPN virtual interface.
Static Routing
In Fireware v11.11.x, to create static BOVPN virtual interface routes between a Firebox and a third-party device, configure the BOVPN virtual interface and add static routes as you would for a BOVPN virtual interface between two Firebox VPN endpoints.
In Fireware v11.12 and higher, to create static BOVPN virtual interface routes between a Firebox and a third-party device:
- Select the Firebox endpoint type to create an IPSec tunnel that uses GRE.
- Select Cloud or Third-Party Endpoint to create an IPSec tunnel without GRE.
For configuration examples, see BOVPN Virtual Interface for Static Routing to Microsoft Azure and BOVPN Virtual Interface for Static Routing to Amazon Web Services (AWS).
Dynamic Routing
To use the BOVPN virtual interface for dynamic routing to a third-party VPN endpoint, you must configure the virtual interface IP address differently than for dynamic routing between two Fireboxes. For configuration examples, see:
- BOVPN Virtual Interface for Dynamic Routing to Cisco
- BOVPN Virtual Interface for Dynamic Routing to Microsoft Azure
- BOVPN Virtual Interface for Dynamic Routing to Amazon Web Services (AWS)
For a BOVPN virtual interface to a third-party device, you specify a local IP address and a subnet mask:
- Local IP address — The IP address to use for the local end of the tunnel. It must be on the same subnet as the local IP address configured for this VPN on the third-party VPN endpoint.
- Peer IP address or netmask — The subnet mask for the local IP address. It must be the same as the netmask configured for this VPN on the third-party endpoint. For dynamic routing to a Microsoft Azure network, specify the Azure virtual interface IP address instead of a netmask. The Azure virtual interface IP address is defined by Azure.
To configure a netmask for dynamic routing to a third-party VPN endpoint, your Firebox must run Fireware OS v11.11 or higher.
To make sure that the addresses you specify do not conflict with any other devices, we recommend that you select a local IP address and netmask in a private network IP address range that is not used by any local network or by any remote network connected through a VPN.
If you enable a BOVPN virtual interface for a FireCluster, make sure that the Local IP address does not conflict with the cluster interface IP addresses or the cluster management IP addresses. The WatchGuard BOVPN virtual interface supports BGP and OSPF. However, dynamic routing with OSPF to Microsoft Azure and Amazon AWS is not currently supported.
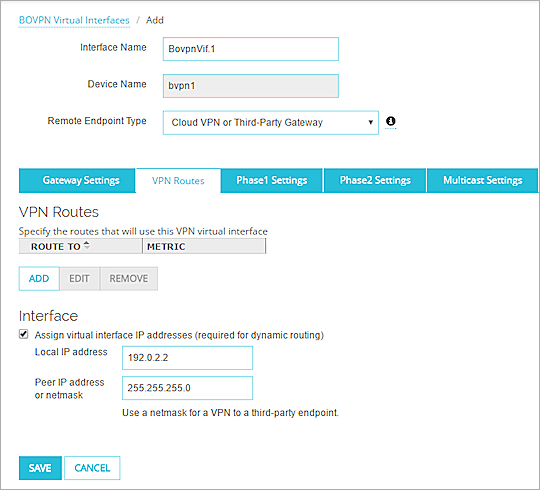
- Add or edit a BOVPN virtual interface.
For more information, see Configure a BOVPN Virtual Interface. - Select the VPN Routes tab.
- In the Interface section, select the Assign virtual interface IP addresses check box.
- In the Local IP address text box, type the IP address for the local end of the tunnel. This address must be on the same subnet as the IP address configured for this VPN tunnel on the third-party endpoint (the peer).
- In the Peer IP address or netmask text box, type the netmask.
The netmask must be the same as the netmask configured for this VPN tunnel on the third-party endpoint.
- Add or edit a BOVPN virtual interface.
For more information, see Configure a BOVPN Virtual Interface. - Select the VPN Routes tab.
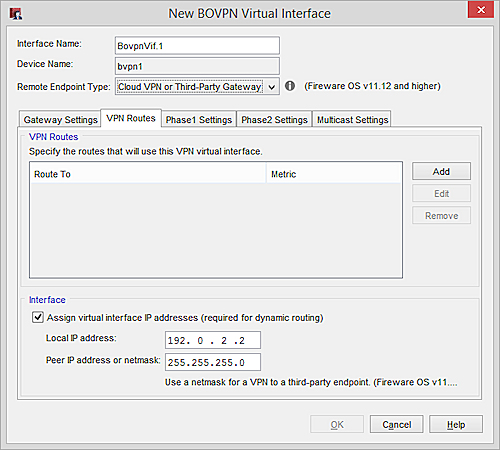
- In the Interface section, select the Assign virtual interface IP addresses check box.
- In the Local IP address text box, type the IP address for the local end of the tunnel.
This address must be on the same subnet as the IP address configured for this VPN tunnel on the third-party endpoint (the peer). - In the Peer IP address or netmask text box, type the netmask.
The netmask must be the same as the netmask configured for this VPN tunnel on the third-party endpoint.
When you configure dynamic routing through the BOVPN virtual interface, use the virtual interface network IP address, not the device name in the dynamic routing configuration. For example, if the BOVPN virtual interface local IP address is 10.10.11.0 and the netmask is 255.255.255.0, specify the 10.10.11.0/24 address in the dynamic routing configuration.