Related Topics
Policy Map
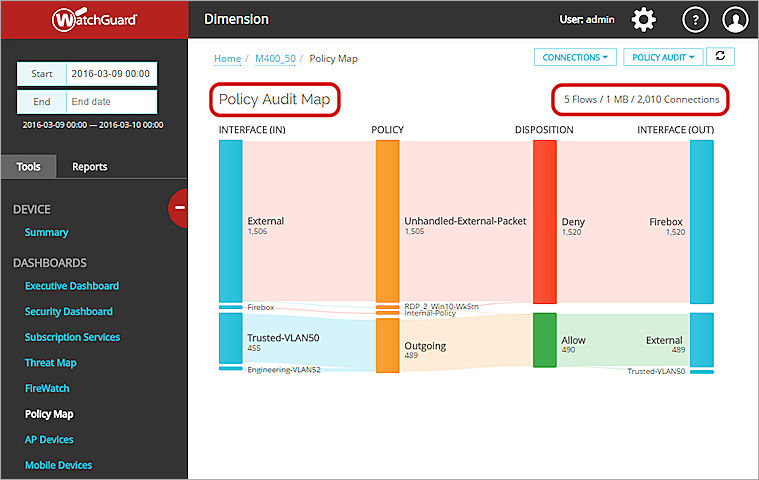
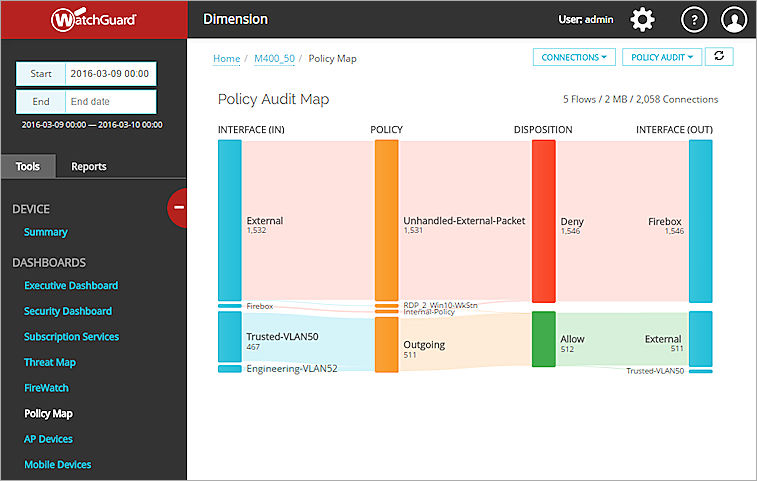
Policy Map is an interactive report tool that aggregates the allowed traffic through your Fireboxes and shows that allowed traffic in a visualization of the traffic flows. Each traffic flow is defined by the unique path a connection takes internally through the device as it is processed by policies and configuration settings on the device. The thickness of a traffic flow ribbon indicates how much traffic is included in that traffic flow: thicker ribbons have more bytes or connections. The color of the ribbons and nodes indicate the type and disposition of the traffic:
- Interfaces — Blue
- Policies — Orange
- Disposition — Green (Allow), Red (Deny)
- Applications and Application categories — Purple
- Web Audit categories — Purple
- Subscription Services — Yellow
- Viruses, DLP rules, APT Blocker — Yellow
Policy Map includes many options to filter and pivot on the data in the traffic flows, and to further explore the details of the traffic flows. You can see information for a single Firebox, FireCluster, or a group of devices in Policy Map for the date and time range you select.
From Policy Map, you can see:
- Subscription Services activity
- Application activity through policies
- Policies in use
- Policies that use the most bandwidth
- Interfaces in use
- Connections between active interfaces
The Policy Map diagrams show visualizations of multiple key concepts at the same time:
- Links between nodes show how the data flows
- Size of links and nodes show the number of bytes or connections
- Color of links show the disposition of the connections (Allowed or Denied)
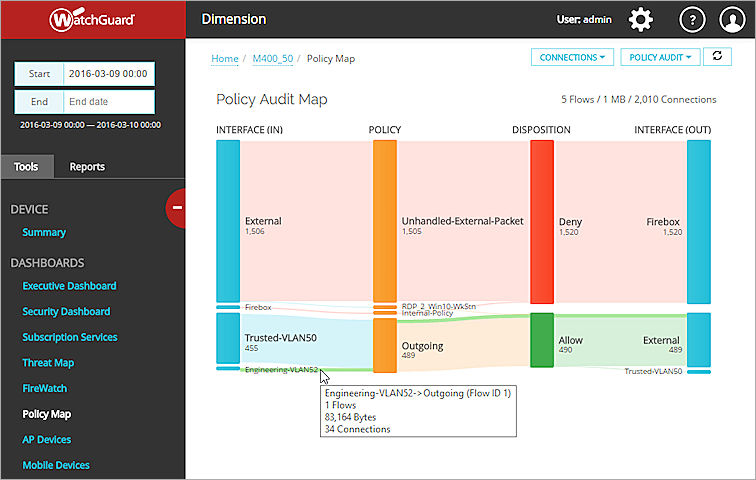
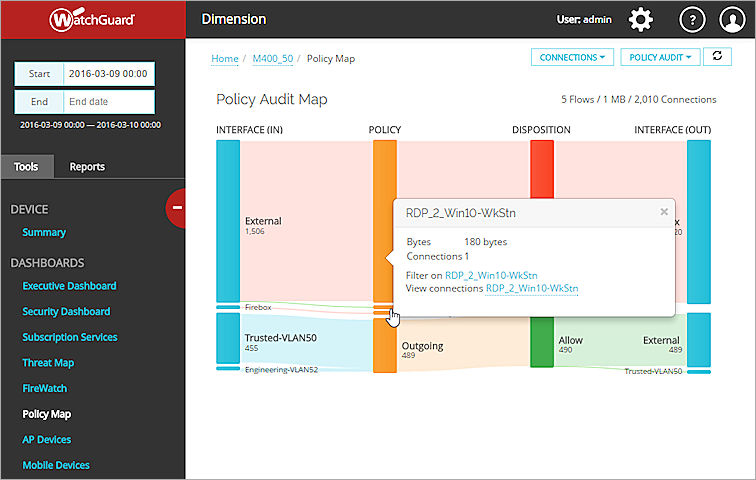
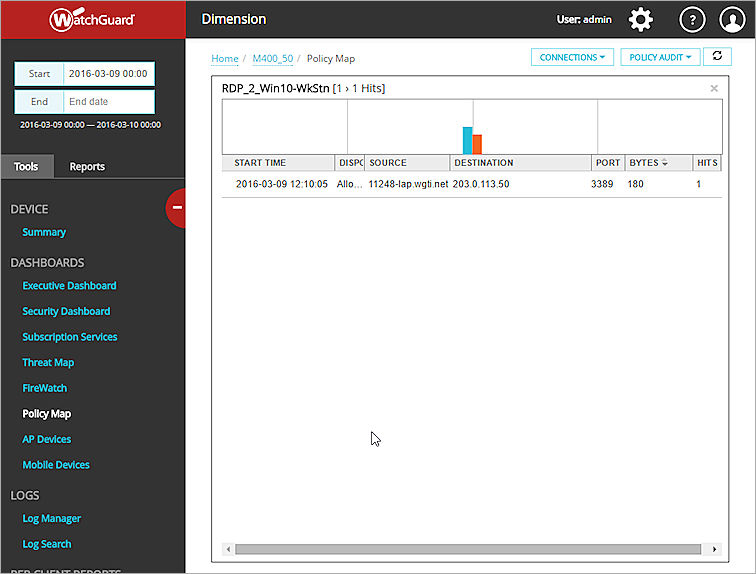
You can also see more detailed information about the data in the Policy Map in tool-tips and popup dialog boxes.
About Policy Map Types
From the Policy Map page, you can select one of the Policy Map types to specify the information that is included in the traffic flow. Each map type includes different data nodes. For each map type, you can pivot the data to further refine the details included in the Policy Map. Pivot options are only available if the log messages from your device, cluster, or group include data for that pivot option.
| Map Types |
Column Node Descriptions |
Pivots |
|---|---|---|
| Policy Audit | The default Policy Map type. Includes all connections aggregated by Source Interface, Firewall Policy, Disposition, and Destination Interface. | Bytes, Connections |
| Subscription Services | Includes all connections for the Subscription Services enabled on your devices or groups, aggregated by Source Interface, Firewall Policy, Subscription Service, Disposition, and Destination Interface. | Bytes*, Connections |
| Web Audit | Includes connections that are aggregated by Source Interface, Firewall Policy, WebBlocker Category, and Disposition. | Connections |
| Application Control | Includes connections that are aggregated by Source Interface, Firewall Policy, Application Category, Disposition, and Destination Interface. | Bytes*, Connections |
| Intrusions (IPS) | Includes connections that are aggregated by Source Interface, Firewall Policy, Severity Level, Disposition, and Destination Interface. | Connections |
| Advanced Malware (APT) | Includes connections that are aggregated by Source Interface, Firewall Policy, Threat Level, Disposition, and Destination Interface. | Connections |
| Data Loss Violations (DLP) | Includes connections that are aggregated by Source Interface, Firewall Policy, Rule Name, Disposition, and Destination Interface. | Connections |
| Virus (GAV) | Includes connections that are aggregated by Source Interface, Protocol, Virus Name, Disposition, and Firewall Policy. | Connections |
View Traffic Flows
To view the traffic flows on your Firebox, FireCluster, or group of devices:
- Select Home > Devices or Home > Groups.
The Devices or Groups page appears. - Select a device or group in the list.
If the Firebox or group has only a logging connection to Dimension, the Executive Dashboard page appears.
If the Firebox or group has a management connection to Dimension, the Device Summary page appears. - From the Start and End drop-down list calendars, select the start and end dates to include in the report data.
- On the Tools tab, select Policy Map.
The Policy Map page appears, with the Policy Audit map type selected by default. - To change the information in the map, from the map type drop-down list at the top-right of the page, select an option:
- Policy Audit
- Subscription Services
- Web Audit
- Application Control
- Intrusions (IPS)
- Advanced Malware (APT)
- Data Loss Violations (DLP)
- Virus (GAV)

- From the pivot drop-down list at the top right of the page, select an available pivot option:
- Bytes
- Connections
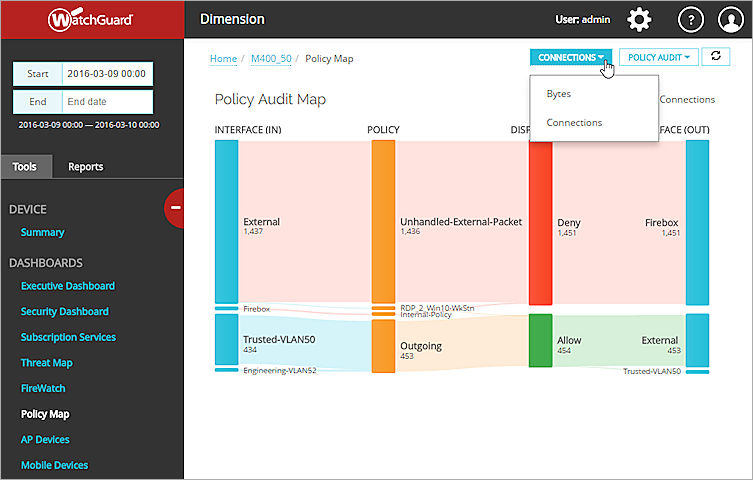
- Review the information in the Policy Map.
For more information about how to use the interactive features in Policy Map, see the next section.
About the Internal-Policy Traffic Flow
When you review traffic flows in Policy Map, you might see the Internal-Policy traffic flow. Unlike the other traffic flows in Policy Map, this traffic flow does not show connections through one policy (or protocol). Instead, the Internal-Policy traffic flow includes this traffic:
- IPSec traffic that uses the ESP or AH protocol
- Any traffic to or from a cluster interface in a FireCluster
- Traffic through a GRE tunnel from localhost to an IPSec tunnel
- UDP traffic from localhost port 68 to destination port 67 (DHCP)
- UDP traffic from destination port 67 to localhost port 68 (DHCP)
- Traffic to or from an interface with the GRE protocol
Though the Internal-Policy traffic flow appears in Policy Map when traffic through the device meets these conditions, Internal-Policy does not appear in the list of policies for your device.
If the settings change for any of the items that appear in the Internal-Policy traffic flow, the appearance of the traffic flow also changes. For example, if you disable an IPSec tunnel on your device, traffic and protocols for that IPSec traffic are no longer included in the Internal-Policy traffic flow.
Use Policy Map Interactive Features
After you have selected the map type and pivot options for a Policy Map, you can use the interactive features in Policy Map to see the details about the flow of traffic through your device, FireCluster, or group. Each Policy Map includes a data flow for each policy that is in use and a column for each node included in the traffic flow. The columns (nodes) included in each Policy Map depend on the map type you select.
Print Policy Map
From your web browser, you can print the Policy Map page. If you can generate a PDF file from your browser, you can also export your current view of the Policy Map page as a PDF. Because each web browser has different menu options, you must use the correct procedure for your web browser. For more information, see the documentation or Help provided with your web browser.
For example, to print Policy Map from Chrome:
- Click
 and select Print.
and select Print.
Or, press Ctrl + P on your keyboard.
The Print page appears. - Specify the print options.
To print a PDF, make sure to select a printer that can generate PDF file. - Click Print.
- To print a PDF, specify a file name and location to save your PDF.