
Related Topics
About FireCluster Management IP Addresses
In a FireCluster configuration, all cluster members share the same IP addresses for each enabled interface. When you use an interface IP address to connect to the cluster in WatchGuard System Manager, you automatically connect to the cluster master and can see the status for all cluster members.
For some management functions, such as restore, you must connect to a specific cluster member. To do that, you use the FireCluster Management IP address, which is a unique IP address you assign to each cluster member. The cluster master also uses the Management IP address of the backup master to communicate with the backup master about device status and action aggregation. For example, when you connect to a FireCluster in Firebox System Manager, the cluster master uses the Management IP address of the backup master to request status information from the backup master. The cluster master then sends that information to Firebox System Manager, so the status of both cluster members appears.
The cluster master uses the Management IP address to manage the backup master even when you are not connected to the cluster. For this reason, it is important that the management interfaces of both cluster members are connected to the same switch at all times.
When you configure the FireCluster, you configure settings related to the FireCluster Management IP address:
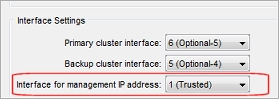
Interface for management IP address (one for the cluster)
First, you must select an interface to assign the FireCluster Management IP address to. This is a global setting that applies to all cluster members. You can select any enabled physical, bridge, VLAN, or Link Aggregation interface, or an external interface that uses PPPoE. We recommend that you select the interface that the management computer usually connects to.
To use a bridge or VLAN interface as the cluster management interface, the cluster must use Fireware XTM v11.9 or higher.
If you want to use IPv6 to connect to an individual cluster member, you must choose an interface that has IPv6 enabled.
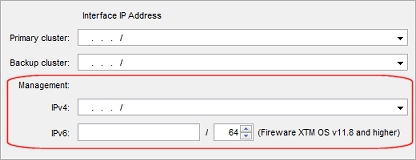
IPv4 management addresses (one for each cluster member)
For each cluster member, you configure a FireCluster Management IP address to use on the selected Interface for management IP address.
We recommend that you select two unused IPv4 addresses on the same subnet as the primary IP address of the interface. This is to make sure that the IP addresses are routable.
For example, if you select the trusted interface as the Interface for management IP address, choose two unused IP addresses from your trusted subnet to use as the FireCluster management IP addresses. If you choose the External interface as the Interface for management IP address, choose two unused external IP addresses on the same subnet as the External interface IP address that you can dedicate to FireCluster management functions.
The management IP addresses must be on the same subnet as the WatchGuard Log Server or syslog server your FireCluster sends log messages to.
If you set the Management IP addresses of a FireCluster member to an IPv4 address that is not on the same subnet as the IP address of the Interface for management IP address, make sure your network configuration includes routes to allow the management software to communicate with FireCluster members and to allow the FireCluster members to communicate with each other.
IPv6 management addresses (one for each cluster member)
If the interface you selected as the Interface for management IP address has IPv6 enabled, you can configure an IPv6 management IP address. If you configure an IPv6 management IP address, it must be an unused IP address. We recommend that you use two IPv6 address with the same prefix as an IPv6 IP address assigned to the Interface for management IP address. This is to make sure that the IP addresses are routable.
If you configure an IPv6 management address for each member:
- The cluster master uses the IPv6 management address of the backup master to communicate with the backup master
- The IPv4 management address for each member is optional
If you use a FireCluster Management IP address to directly connect to the backup master, you cannot save configuration changes in Policy Manager.
Use the Management IP Address to Restore a Backup Image
When you restore a FireCluster backup image, you must use the FireCluster Management IP address to connect directly to a cluster member. When you use this IP address to connect to a cluster member, there are two additional commands available in Firebox System Manager on the Tools menu: Cluster > Leave and Cluster > Join. You use these commands when you restore a backup image to the cluster.
For more information, see Restore a FireCluster Backup Image.
Use the Management IP Address to Upgrade from an External Location
The WatchGuard System Manager software uses the FireCluster Management IP address when you upgrade the OS for the members of a cluster. If you want to update the OS from a remote location, make sure that:
- The Interface for management IP address is set to an external interface
- The Management IP address for each cluster member is a public IP address and is routable
For more information, see Upgrade Fireware OS for a FireCluster.
The Management IP Address and the WatchGuard Policy
The WatchGuard policy (policy type WG-Firebox-Mgmt) controls administrative connections to the device. By default, the WatchGuard policy allows management connections from the Any-Trusted or Any-Optional aliases. If you set the FireCluster Management Interface to a Trusted or Optional interface, the Management Interface IP addresses are automatically included in the Any-Trusted alias or the Any-Optional alias, and you do not need to modify the WatchGuard policy for FireCluster management connections to operate correctly.
There are two situations for which you must edit the WatchGuard policy to add the FireCluster Management IP addresses:
- If you restrict management access to specific IP addresses
To restrict management access to specific IP addresses, you can edit the WatchGuard policy to remove the Any-Trusted or Any-Optional aliases from the From section, and add only the IP addresses or aliases that you want to manage the device. If you do this, it is important that you also add the FireCluster Management IP addresses to the From section of the WatchGuard policy.
- If you set the FireCluster Management Interface to an External interface
If you select an External interface as the FireCluster Management Interface, you must either add the FireCluster Management IP addresses or add the Any-External alias to the From section of the WatchGuard policy. Your configuration is more secure if you add the specific Management IP addresses than it is if you add the Any-External alias.
For more information about the WatchGuard policy, see Administer Your Firebox From a Remote Location.