
Related Topics
Configure Mobile Security Enforcement
You can enforce Mobile Security on one or more interfaces on your Firebox. The interfaces can be physical interfaces, or logical interfaces, such as VLAN or link aggregation interfaces. When you enable Mobile Security on an interface, the Firebox denies traffic from Android or iOS devices that do not comply with the configured device compliance settings. For an Android or iOS device to be compliant, FireClient must be installed and open on the mobile device, and FireClient must report that the device is compliant with the Mobile Security device compliance settings.
You can also configure whether to enforce Mobile Security for VPN connections, and you can configure Mobile Security exceptions.
Before you begin, you must Enable Mobile Security.
Configure Interfaces for Enforcement
By default, Mobile Security enforcement is enabled on all trusted and optional interfaces. When you configure the Mobile Security Enforcement settings, you can specify on which interfaces the Mobile Security compliance settings that you specified are enforced. This enables you to include only the interfaces for networks where you want to enforce Mobile Security, and remove all other interfaces. For example, you might want to enforce Mobile Security only for the employee wireless network, but not for the guest wireless network, so you remove the interfaces for the guest wireless network from the Interfaces list.
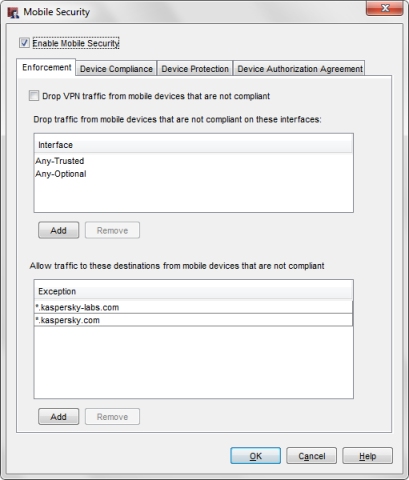
- On the Mobile Security page, select the Enforcement tab.
The Interfaces list shows the current list of interfaces for enforcement.
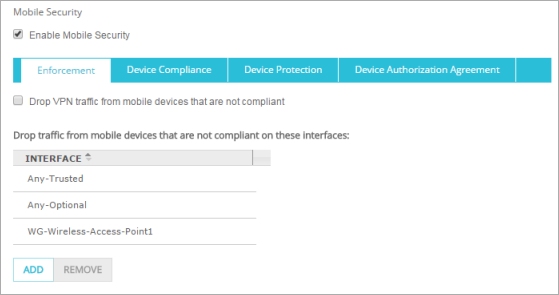
- To remove an interface, from the Interface list, select the interface alias and click Remove.
- To add an interface, click Add.
The Add Interface dialog box appears. - From the Interface drop-down list, select an interface alias.
- Click OK.
The interface is added to the Interfaces list. - Click Save.
- In the Mobile Security dialog box, select the Enforcement tab.
The Interface list shows the current list of interfaces for enforcement.
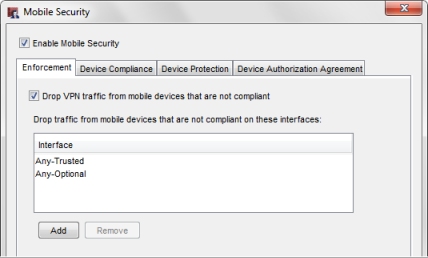
- To remove an interface, from the Interface list, select the interface alias and click Remove.
- To add an interface, click Add.
The Add Interface dialog box appears. - From the Interface drop-down list, select an interface alias.
- Click OK.
The interface is added to the Interfaces list. - Click Save.
Enable Enforcement for VPN Connections
You can use Mobile Security to enforce compliance of mobile devices that use Mobile VPN with SSL or Mobile VPN with IPSec to connect to the Firebox. To do this, you must enable Mobile Security on the Firebox that the VPN clients connect to.
- On the Mobile Security page, select the Enforcement tab.
- Select the Drop VPN traffic from mobile devices that are not compliant check box.
- Click Save.
- In the Mobile Security dialog box, select the Enforcement tab.
- Select the Drop VPN traffic from mobile devices that are not compliant check box.
- Click OK.
If you enable Mobile Security enforcement for VPN connections, a user must run FireClient after they establish the SSL or IPSec VPN connection from the mobile device. Because the user has already authenticated and established a connection through a VPN, FireClient does not prompt the user to authenticate again.
Configure Exceptions
Mobile Security does not drop traffic to sites on the Mobile Security Exceptions list. By default, the Mobile Security configuration includes two exceptions that enable the FireClient app to download the application signature database from Kaspersky Labs, so that it can scan installed apps for compliance. You cannot remove the two default exceptions. You can add other exceptions if you want to allow traffic to specific destinations from mobile devices that are not compliant.
- On the Mobile Security page, select the Enforcement tab.
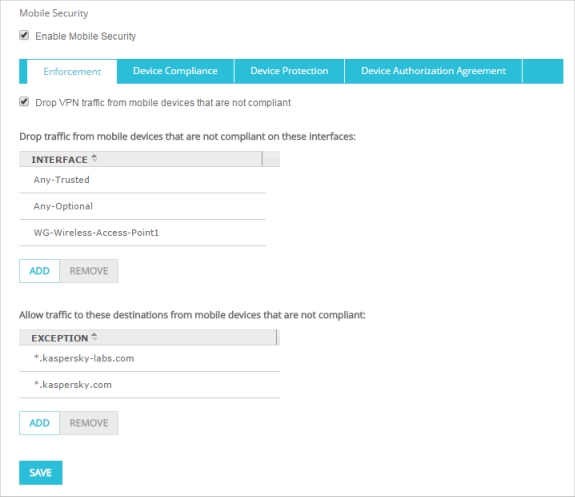
- Below the Exception list, click Add.
The Add Exception dialog box appears.
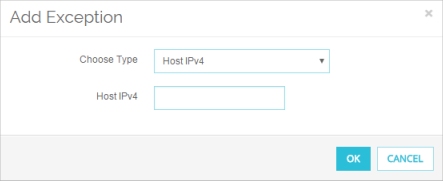
- From the Choose Type drop-down list, select a method to identify the blocked site exception:
- Host IPv4
- Network IPv4
- Host Range IPv4
- FQDN (Fully Qualified Domain Name)
- In the Value text box, type the IP address, network IP address, or FQDN.
If the exception is for a host range, type the start and end IP addresses for the range of IP addresses in the exception.
For FQDN, you can type a specific domain name or include a wildcard to indicate the domain and all subdomains. For example, example.com or *.example.com. - Click OK.
The exception is added to the Exception list. - To remove an exception, from the Exception list, select the exception, and click Remove.
- Click Save.
- In the Mobile Security dialog box, select the Enforcement tab.
- Below the Exception list, click Add.
The Add Sites dialog box appears.
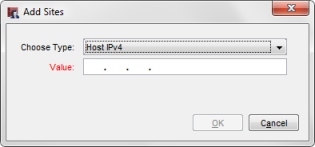
- From the Choose Type drop-down list, select a method to identify the blocked site exception.
- Host IPv4
- Network IPv4
- Host Range IPv4
- FQDN (Fully Qualified Domain Name)
- In the Value text box, type the IP address, network IP address, IPv4 host range, or FQDN.
If the exception is for a host range, type the start and end IP addresses for the range of IP addresses in the exception.
For FQDN, you can type a specific domain name or include a wildcard to indicate the domain and all subdomains. For example, example.com or *.example.com. - Click OK.
The exception is added to the Exception list. - To remove an exception, select the exception and click Remove.
- Click Save.