
Related Topics
TLS Profiles
Transport Layer Security (TLS) profiles define a set of security settings that can be used by an IMAP proxy action. To use a TLS profile, you must configure a proxy action to use it, and you must enable TLS support in the IMAP proxy policy that uses the proxy action.
For information about how to configure TLS for IMAP-Proxy, see IMAP-Proxy: TLS.
TLS Profiles are supported in Fireware OS v12.1 and higher.
Predefined TLS Profiles
The configuration includes two predefined TLS profiles:
- TLS-Client.Standard — This profile is used by the predefined IMAP-Client.Standard proxy action. It does not enforce SSL compliance.
- TLS-Server.Standard — This profile is used by the predefined IMAP-Server.Standard proxy action. It allows only SSL compliant traffic.
You cannot edit the predefined profiles, you can only clone them, and then edit the copy.
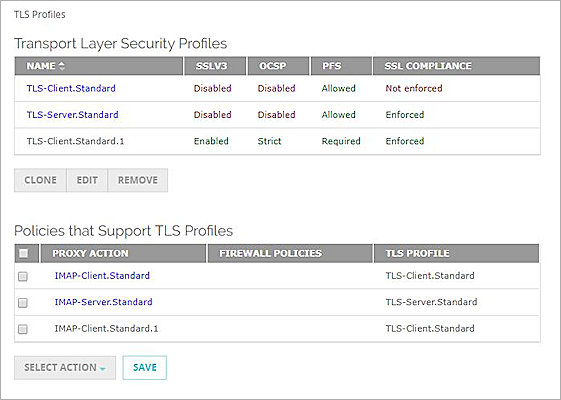
View TLS Profiles
To view TLS Profiles, select Firewall > TLS Profiles.
Screen shot of the TLS Profiles page in Fireware Web UI
Transport Layer Security Profiles
These settings are shown for each Proxy Action that supports TLS:
- SSLv3 — Enabled or Disabled
- OCSP — Disabled, Lenient, or Strict
- PFS Ciphers — Allowed, Required, or None
- SSL Compliance — Enforced or Not Enforced
These settings are described in the next section.
You can Clone predefined profiles and Clone, Edit, or Remove user-defined profiles.
Policies that Support TLS Profiles
The Proxy Actions that support TLS are listed along with their Firewall Policy Name and TLS Profile.
Select Action
Select a Proxy Action and then choose a TLS Profile from the Select Action drop-down list.
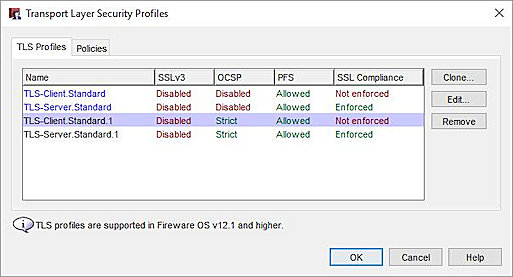
To view TLS Profiles, select Setup > Actions > TLS Profiles.
Screen shot of the TLS Profiles dialog in Policy Manager
Transport Layer Security Profiles
These settings are shown for each Proxy Action that supports TLS:
- SSLv3 — Enabled or Disabled
- OCSP — Disabled, Lenient, or Strict
- PFS Ciphers — Allowed, Required, or None
- SSL Compliance — Enforced or Not Enforced
These settings are described in the next section.
You can Clone predefined profiles and Clone, Edit, or Remove user-defined profiles.
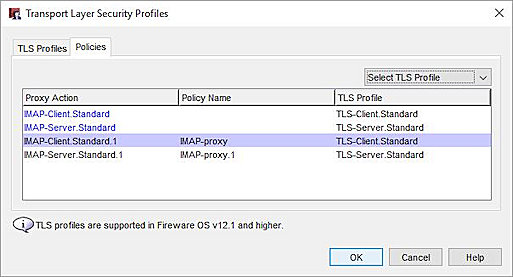
To view the profile policies, select the Policies tab.
Screen shot of the TLS Profiles dialog Policies tab in Policy Manager
Policies that Support TLS Profiles
The Proxy Actions that support TLS are listed along with their Firewall Policy Name and TLS Profile.
Select TLS Profile
Select a Proxy Action and then choose a TLS Profile from the Select TLS Profile drop-down list.
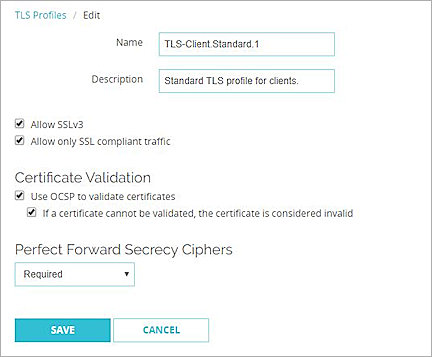
Clone or Edit TLS Profile
Clone or Edit TLS Profile allows you to configure the settings for the TLS profile. For more information about cloning or editing predefined and user-defined proxy actions, see About Proxy Actions
Allow SSLv3
SSLv3 and TLSv1 are protocols used for secure connections. SSLv3 is not as secure as TLSv1. By default, the IMAP proxy only allows connections that negotiate the TLSv1 protocol. If your users connect to client or server applications that only support SSLv3, you can configure the IMAP proxy to use SSLv3 for connections to these websites.
To enable SSLv3, select the Allow SSLv3 check box. This option is disabled by default.
Enabling SSLv3 increases the vulnerability of your network. SSLv3 should only be enabled for a specific need such as backwards compatibility of legacy systems on internal networks.
Allow only TLS-compliant traffic
This option enables the IMAP proxy policy to allow only traffic that is compliant with the TLS 1.0, TLS 1.1, TLS 1.2 protocols.
Only TLS protocol messages that adhere to TLS standards that are considered secure and can be interpreted by the IMAP proxy. This option is automatically enabled when you enable content inspection.
When content inspection is enabled and TLS compliant traffic establishes a secure tunnel through the IMAP proxy, if the tunneled traffic does not use a valid TLS protocol, the IMAP proxy action used for inspection prompts the Firebox to send a log message about the errors and drop the traffic. If content inspection is disabled, the IMAP proxy listens on port 443 only.
For more information on how to enable content inspection, see IMAP-Proxy: TLS.
Use OCSP to validate certificates
This option applies only to client proxy actions. Server proxy actions do not validate certificates.
Select this check box to enable your Firebox to automatically check for certificate revocations with OCSP (Online Certificate Status Protocol). When this feature is enabled, your Firebox uses information in the certificate to contact an OCSP server that keeps a record of the certificate status. If the OCSP server responds that the certificate has been revoked, your Firebox disables the certificate.
If you select this option, there can be a delay of several seconds while your Firebox requests a response from the OCSP server. The Firebox retains 300 and 3000 OCSP responses in a cache to improve performance for frequently visited websites. The number of responses stored in the cache is determined by your Firebox model.
This option implements a Lenient OCSP policy. If the OCSP server cannot be contacted for any reason and does not send a response, the Firebox does not disable the certificate or break the certificate chain. Only revoked certificates are considered invalid.
The OCSP specification defines the following definitive response indicators for use in the certificate status value:
- Good — This state indicates a positive response to the status inquiry. At a minimum, this positive response indicates that no certificate with the requested certificate serial number currently within its validity interval is revoked. This state does not necessarily mean that the certificate was ever issued or that the time at which the response was produced is within the certificate's validity interval. Response extensions may be used to convey additional information on assertions made by the responder regarding the status of the certificate, such as a positive statement about issuance, validity, etc.
- Revoked — This state indicates that the certificate has been revoked, either temporarily (the revocation reason is certificate Hold) or permanently. This state MAY also be returned if the associated CA has no record of ever having issued a certificate with the certificate serial number in the request, using any current or previous issuing key (referred to as a "non-issued" certificate in this document).
- Unknown — This state indicates that the responder doesn't know about the certificate being requested, usually because the request indicates an unrecognized issuer that is not served by this responder.
If a certificate cannot be validated, the certificate is considered invalid
When this option is enabled, the Firebox enforces a Strict OCSP policy. If an OCSP responder does not send a response to a revocation status request, your Firebox considers the original certificate as invalid or revoked. This option can cause certificates to be considered invalid if there is a routing error or a problem with your network connection. Only certificates with a good response indicator are considered valid.
Perfect Forward Secrecy Ciphers
The IMAP proxy supports PFS-capable ciphers for TLS connections. Fireware supports only Elliptic Curve Ephemeral Diffie-Hellman (ECDHE) ciphers for PFS.
To control whether the Firebox uses PFS-capable ciphers, choose one of these options:
- None — The Firebox does not advertise or select PFS-capable ciphers.
- Allowed — The Firebox advertises and selects both PFS-capable and non-PFS-capable ciphers.
- Required— The Firebox advertises and selects only PFS-capable ciphers.
The setting you select applies to both client and server side TLS connections. When this option is set to Allowed, the client does not use a PFS-cipher unless the server also uses one.
Perfect Forward Secrecy Ciphers require significant resources and can impact system performance on Firebox T10, T15, T30, T35, T50, XTM 25, XTM 26, and XTM 33 devices.
The cipher name used for client/server TLS sessions appears in the IMAP content inspection traffic log messages generated by the Firebox. For more information about log messages, see Types of Log Messages.
Screen shot of the Edit TLS Profiles page in Fireware Web UI

Screen shot of the Edit TLS Profiles page in Policy Manager