
Related Topics
SMTP-Proxy: TLS Encryption
You can configure the SMTP-proxy to use TLS encryption to process email sent from a client email server (the sender) to your SMTP server (the recipient). SMTP over TLS is a secure extension to the SMTP service that allows an SMTP server and client to use TLS (transport-layer security) to provide private, authenticated communication over the Internet. For SMTP, this usually involves the use of STARTTLS keywords. TLS encryption settings for the SMTP-proxy have two configurable parts: when to use encryption (sender or recipient channel) and how to encrypt traffic (SSL or TLS protocol and certificate type). You can use these settings to specify the encryption settings for incoming traffic (sender email), for traffic from your SMTP server (the recipient), or both.
For the SMTP proxy to use TLS encryption, you must enable Content Inspection with TLS in the SMTP proxy action. For more information, see Configure TLS Encryption Settings.
About TLS Encryption
SSLv3, SSLv2, and TLSv1 are all protocols used for encrypted SMTP connections. SSLv2 is not as secure as SSLv3 and TLSv1. When you enable TLS encryption, by default, the SMTP-proxy only allows connections that negotiate the TLSv1 protocol. You can, however, enable the SMTP-proxy to use the SSLv3 and SSLv2 protocols for connections to and from SMTP clients or servers that require these protocols.
About Certificates for TLS Encryption
The SMTP TLS function uses the Proxy Server certificate. The Proxy Server certificate is used for any inbound traffic inspection (HTTPS or SMTP).
For more information, see About Certificates.
About OCSP Options
You can also choose whether to use OCSP (Online Certificate Status Protocol) to validate certificates. If you enable this option, your Firebox automatically uses OCSP to check for certificate revocations. When this feature is enabled, the Firebox uses information in the certificate to contact an OCSP server that keeps a record of the certificate status. If the OCSP server responds that the certificate has been revoked, the Firebox disables the certificate. This process can cause a delay of several seconds while the Firebox requests a response from the OCSP server. To improve performance for frequently accessed hosts, the Firebox keeps between 300 and 3000 OCSP responses in a cache. The number of responses stored in the cache is determined by your Firebox model.
When you use OCSP to validate certificates, you can also specify whether certificates that cannot be validated are considered valid. If you specify that invalidated certificates are invalid, and if an OCSP responder does not send a response to a revocation status request, the Firebox considers the original certificate as invalid or revoked. This option can cause certificates to be considered invalid if there is a routing error or a problem with your network connection.
About Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) cipher settings control the type of TLS ciphers that the Firebox negotiates in the TLS handshake process. You can separately control PFS for client and server TLS encryption. Fireware supports only Elliptic Curve Ephemeral Diffie-Hellman (ECDHE) ciphers for PFS.
To control whether the Firebox uses PFS-capable ciphers, choose one of these options:
- None — The Firebox does not advertise or select PFS-capable ciphers.
- Allowed — The Firebox advertises and selects both PFS-capable and non-PFS-capable ciphers.
- Required— The Firebox advertises and selects only PFS-capable ciphers.
The PFS cipher settings you select apply to all channels that use STARTTLS, as specified in the Encryption Rules.
Perfect Forward Secrecy Ciphers require significant resources and can impact system performance on Firebox T10, T15, T30, T35, T50, XTM 25, XTM 26, and XTM 33 devices. In Fireware v11.12.1, you cannot enable PFS ciphers for these models.
The cipher name for client/server TLS sessions appears in the SMTP request log messages generated by the Firebox. For more information about log messages, see Types of Log Messages.
About Encryption Rules
After you enable TLS encryption for your SMTP proxy action, you add rules to specify the sender and recipient domains, and the required encryption details for each domain. When you add rules to the Encryption Rules list, the rules are evaluated in order from the first rule to the last rule in the list. Make sure to put your rules in an order that provides the most flexibility. For example, if you have more than one SMTP server domain, put the rule for your primary SMTP server first in the list, with rules for any backup SMTP servers lower in the list.
When you add encryption rules, you can create rules for specific sender and recipient domains. Or, to create a global rule, you can use a wildcard character (*) for either the sender or recipient domain. You can specify encryption rules for the sender channel, for the recipient channel, or both. This enables you to set different encryption rules for specific domains that send email to your SMTP server. Each encryption rule must be 200 bytes or less in length.
Sender Encryption
- Required — The sender SMTP server must negotiate encryption with the Firebox.
- None — The Firebox does not negotiate encryption with the sender SMTP servers.
- Optional — The sender SMTP server can negotiate encryption with the receiver SMTP server. TLS encryption depends on the encryption capabilities and settings of the receiver SMTP server.
Recipient Encryption
- Required — The Firebox must negotiate encryption with the recipient SMTP server.
- None — The Firebox does not negotiate encryption with the recipient SMTP server.
- Preferred — The Firebox tries to negotiate encryption with the recipient SMTP server.
- Allowed — The Firebox uses the behavior of the sender SMTP server to negotiate encryption with the recipient SMTP server.
If you do not want to add rules for more than one domain, you can set the Sender Encryption to Optional, Recipient Encryption to Preferred, and use the wildcard character (*) for the domain information. With these encryption settings, most email is safely sent to your SMTP server.
If your users connect to your network over a public Internet connection, WatchGuard recommends that you select Required for the Sender Encryption setting. If your SMTP server does not support encryption, WatchGuard recommends that you select Optional, because email that is not encrypted can still be accepted.
If your users send email to your SMTP server through your protected corporate intranet, you have the most flexibility if you set Sender Encryption to Optional and Recipient Encryption to None.
If you add a rule that always requires traffic from a sender domain to be encrypted, you can also specify that a TLS protocol must be used for the recipient, sender, and body information in the email message.
Configure TLS Encryption Settings
When you create a new configuration file, you must enable Content Inspection with TLS in the SMTP proxy action before you can configure the settings for TLS encryption. If your configuration file already has Content Inspection with TLS enabled, you can complete the configuration settings for TLS encryption.
To enable TLS encryption and configure the rules for an SMTP proxy action:
- In the SMTP proxy action settings, select ESMTP > TLS Encryption.

SMTP-Proxy Action TLS encryption configuration in Fireware Web UI
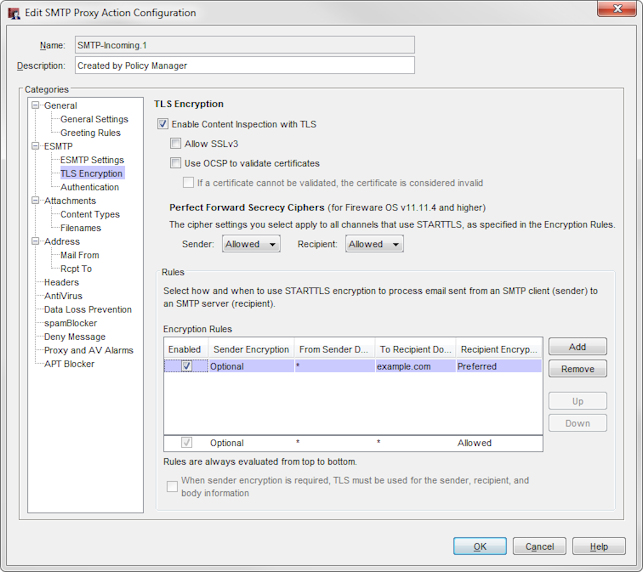
SMTP-Proxy Action TLS encryption configuration in Policy Manager
- Select the Enable Content Inspection with TLS check box.
- To allow the use of the SSLv3 protocol for content inspection with TLS, select the Allow SSLv3 check box. Tip!You can enable SSLv3 to support legacy mail servers.
- (Optional) Select the Use OCSP to validate certificates check box.
- To specify how certificates that cannot be validated are processed, select the If a certificate cannot be validated, the certificate is considered invalid check box.
- To add encryption rules, in the Rules section, click Add.
A new encryption rule appears in the Encryption Rules list. - In the To Recipient Domain text box, type the domain name for your SMTP server and press Enter on your keyboard.
- To specify the domain that client traffic can come from, in the From Sender Domain column, double-click the default setting, *, type a new setting in the text box, and press Enter on your keyboard.
To allow traffic from any domain, keep the default setting, *. - To change the Recipient Encryption option, click the default setting, Preferred, and select an option from the drop-down list:
- Required
- None
- Preferred
- Allowed
- To change the Sender Encryption option, click the default setting, Optionally Encrypted, and select an option from the drop-down list:
- Required
- None
- Optional
- To change the order that rules are applied, select a rule in the Encryption Rules list, and click Up or Down.
- To disable a rule in the list, clear the Enabled check box for that rule.
- To delete a rule from the list, click Remove.
- To require the TLS protocol to be used for encrypted sender traffic, select the When sender encryption is required, TLS must be used for the sender, recipient, and body information check box.
This option is only available if you configure a rule with a Sender Encryption setting of Always Encrypted.
For more information about proxy action rules, see Add, Change, or Delete Rules. - To change settings for another category in this proxy action, see the topic for that category.
- Save the configuration.
If you modified a predefined proxy action, when you save the changes you are prompted to clone (copy) your settings to a new action.
For more information on predefined proxy actions, see About Proxy Actions.