
Related Topics
Configure a Firewall Policy for TDR Traffic
When you enable TDR on your Firebox, the Firebox configuration must include a policy to allow the Host Sensors on your network to connect to your TDR account.
About The WG-TDR-Host-Sensor Policy Template
When you enable Threat Detection and Response in Fireware v11.12.1 and higher, the WatchGuard Threat Detection and Response policy is automatically added to the configuration. This policy uses the WG-TDR-Host-Sensor packet filter policy template which allows TCP traffic on port 443 from the alias Any-Trusted to the FQDNs for both TDR regions. To allow traffic from Host Sensors on the Optional networks, you can edit this policy to add the alias Any-Optional or add a specific interface name to the From list.
If your Firebox runs Fireware v11.12 or lower, when you enable TDR from Policy Manager or Fireware Web UI, you must manually add a policy that allows connections from your network to the FQDN for your TDR account.
Manually Add a Policy to Allow Host Sensor Traffic
If your Firebox runs Fireware v11.12.1 or higher, to allow Host Sensor connections from the trusted network, add the WG-TDR-Host-Sensor packet filter policy to your configuration. This policy is automatically added when you enable TDR on the Firebox.
If your Firebox runs Fireware v11.12, manually add an HTTPS packet filter policy with these settings:
- Connections are — Allowed
- From — Any-Trusted, Any-Optional (or the location where your Host Sensors are installed)
- To — FQDNs tdr-hsc-na.watchguard.com and tdr-hsc-eu.watchguard.com
If you want to allow connections only to the FQDN for your TDR account, you can find the FQDN in the TDR web UI, and add it to the packet filter policy.
- Log in to the TDR web UI as a user with Operator credentials.
- Select Configuration > Host Sensor.
The Host Sensor page appears. - In the Host Sensor section, find the Controller Address. It appears in the format FQDN:port.
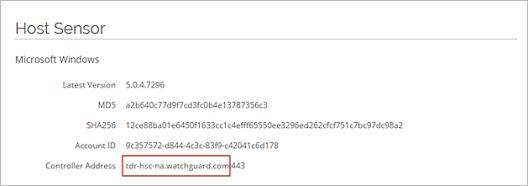
- Copy the FQDN value. Do not include the port number.
- Select Firewall > Firewall Policies.
- Click Add Policy.
- From the Packet Filter drop-down list, select HTTPS.
- Click Add Policy.
The policy settings appear. - In the Name text box, type a name to identify this policy.
For example, type HTTPS-TDR. - In the To list, select Any-External and click Remove.
- In the To list, click Add.
- From the Member Type drop-down list, select FQDN.
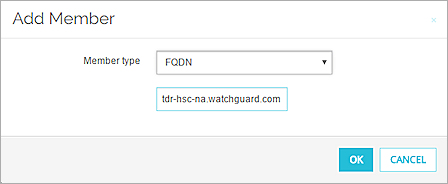
- In the text box, paste the FQDN you copied from the Host Sensor Controller Address.
- Click OK.
The FQDN is added as the destination for the policy.
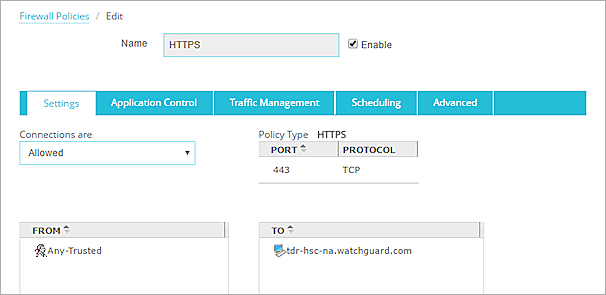
- Click Save.
- Open the Firebox configuration in Policy Manager.
- Select Edit > Add Policy.
- From the Packet Filter drop-down list, select HTTPS.
- Click Add.
- In the Name text box, type a name to identify this policy.
For example, type HTTPS-TDR. - In the To list, select Any-External and click Remove.
- In the To list, click Add.
- Click Add Other.
- From the Choose Type drop-down list, select FQDN.
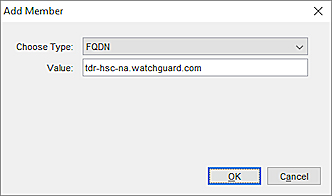
- In the Value text box, paste the FQDN you copied from the Host Sensor Controller Address.
- Click OK twice.
The FQDN is added as the destination for the policy.

- Click OK.
- Save the configuration to the Firebox.
Add FQDNs for TDR Sandbox Analysis and AD Helper
It might be necessary to add other FQDNs as destinations in the WG-TDR-Host-Sensor or other HTTPS packet filter policy to allow Host Sensors and AD Helper to connect to the TDR cloud.
You must add these FQDNs only if your Firebox has an HTTPS proxy policy with these certificate validation options enabled in the content inspection settings:
- Use OCSP to validate certificates
- If a certificate cannot be validated, the certificate is considered invalid
To allow TDR Host Sensors to execute the Sandbox File action, add these FQDNs as destinations in the WG-TDR-Host-Sensor policy:
tdr-frontline-eu.watchguard.com
tdr-frontline-na.watchguard.com
To allow AD Helper to connect to the TDR cloud, add these FQDNs as destinations in the WG-TDR-Host-Sensor policy:
tdr-adhh-na.watchguard.com
tdr-adhh-eu.watchguard.com
Enable Proxy Policies and Services
For TDR to effectively correlate network events with Host Sensor events, we recommend that you also enable proxy policies and services on the Firebox. For more information, see Configure Proxy Policies for TDR.