Deployment Overview
You can configure the WatchGuard Access Portal to enable your users to log in through one portal and get access to multiple services. This document describes how to configure the WatchGuard Access Portal to integrate with Microsoft IIS Application Request Routing (ARR) and Exchange Outlook Web Application.
Integration Summary
Hardware and Service versions:
- IIS URL Rewrite Module 7.2
- IIS Application Request Routing (ARR) 3.0
- Exchange 2019
- Microsoft Windows Server 2019
- WatchGuard Firebox:
- Fireware v12.7.1
- Feature key with an Access Portal license
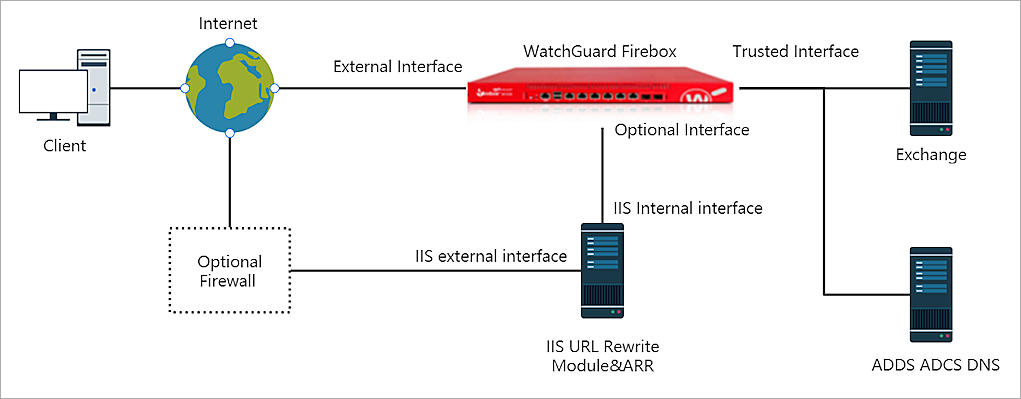
Test Topology
Before You Begin
- Install AD DS & DNS and AD CS on your Windows server
- Install Microsoft Exchange Server on your Windows server
- Install IIS URL Rewrite Module and ARR on your Windows server
- Publish certificate to domain member
Your Exchange server must be joined to the domain. Your ARR can bet joined to the domain, but this is optional. In this integration guide, our ARR sever is joined to the domain.
Configure IIS ARR
- Log in to IIS Manager.
- Navigate to IIS HOME.
- Click Server Certificates.
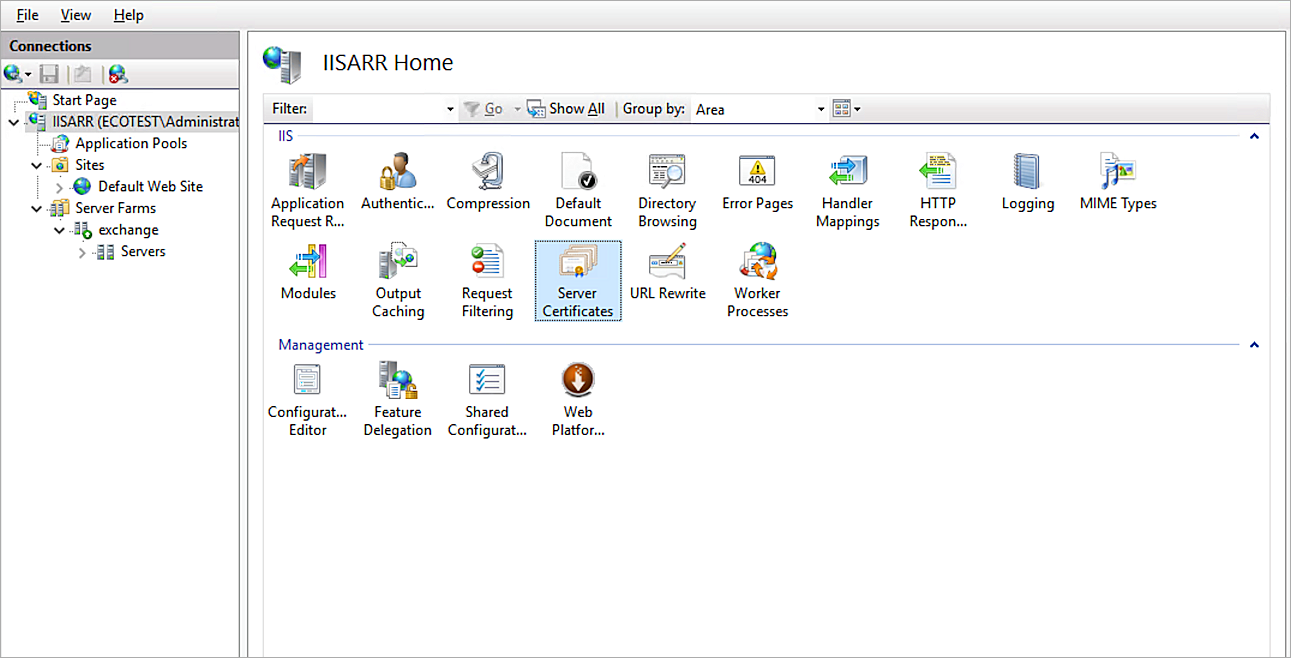
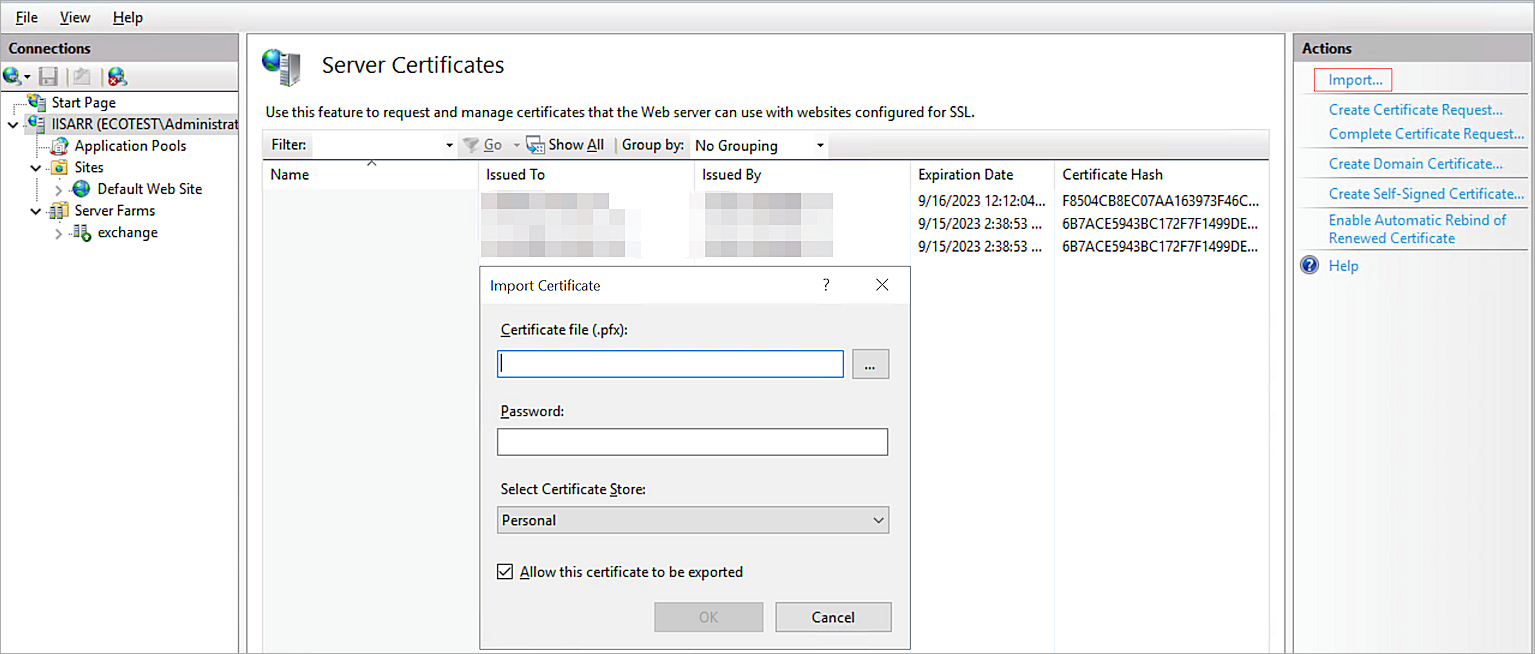
- Click Import to import the Exchange certificate.
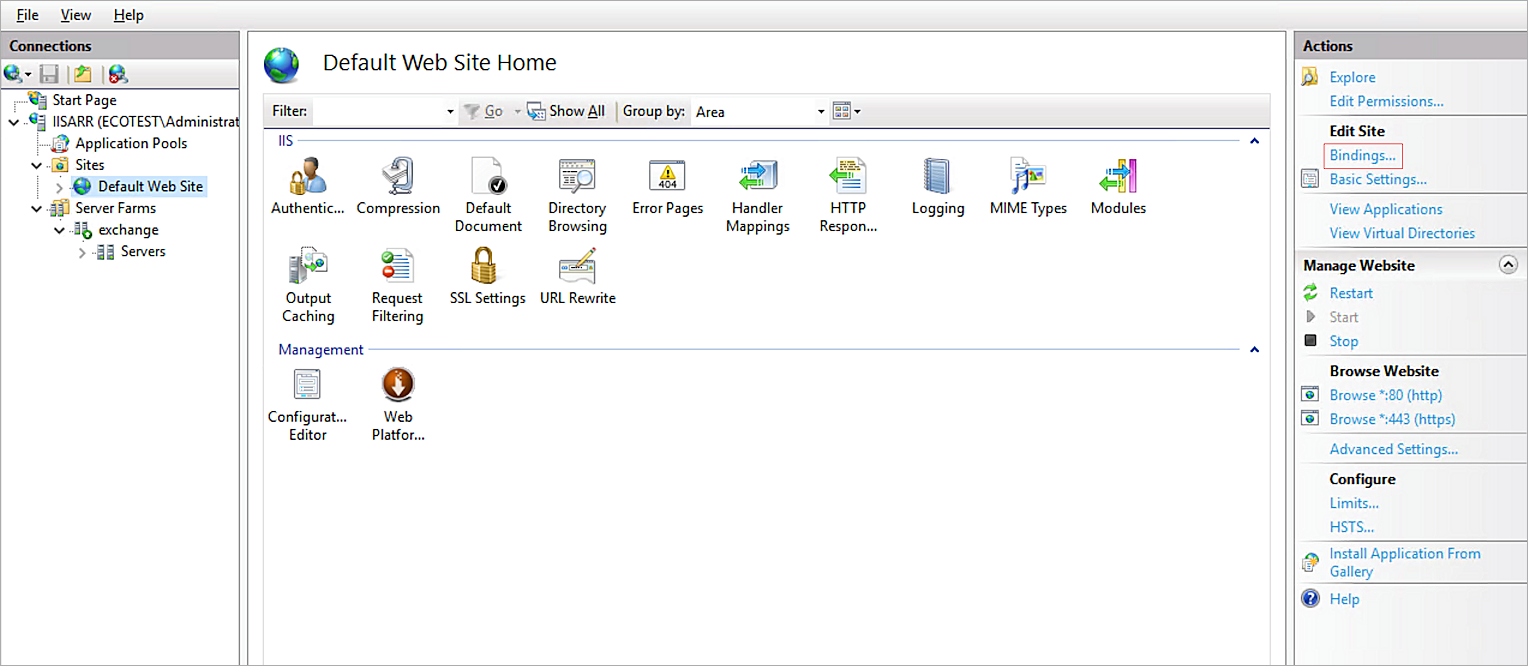
- Click Default Web Site.
- In the Actions list, click Bindings.
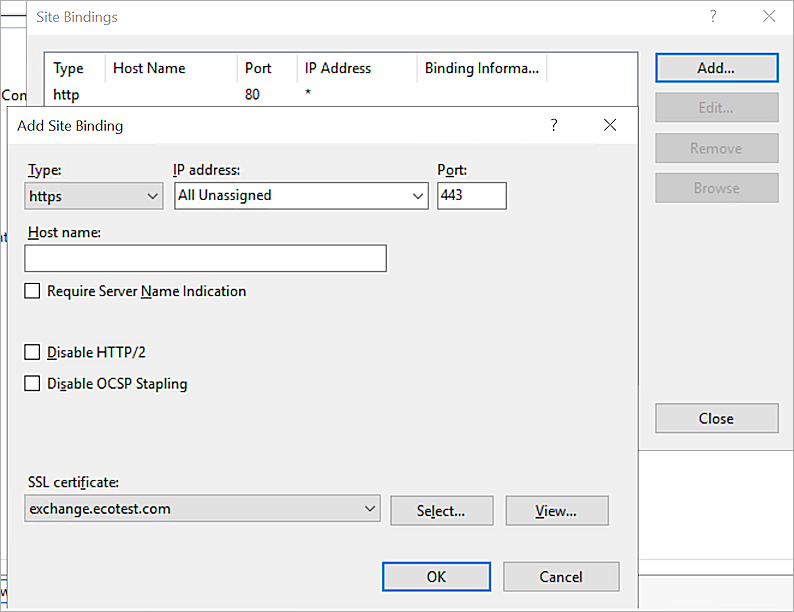
- Add an https Binding using the Exchange certificate.
- Right click Server Farms, select Create Server Farm.
- Type the Server farm name and Server address. The server is the exchange server. The server address can be an FQDN or IP address.
After the server is added, the server status should be Online.
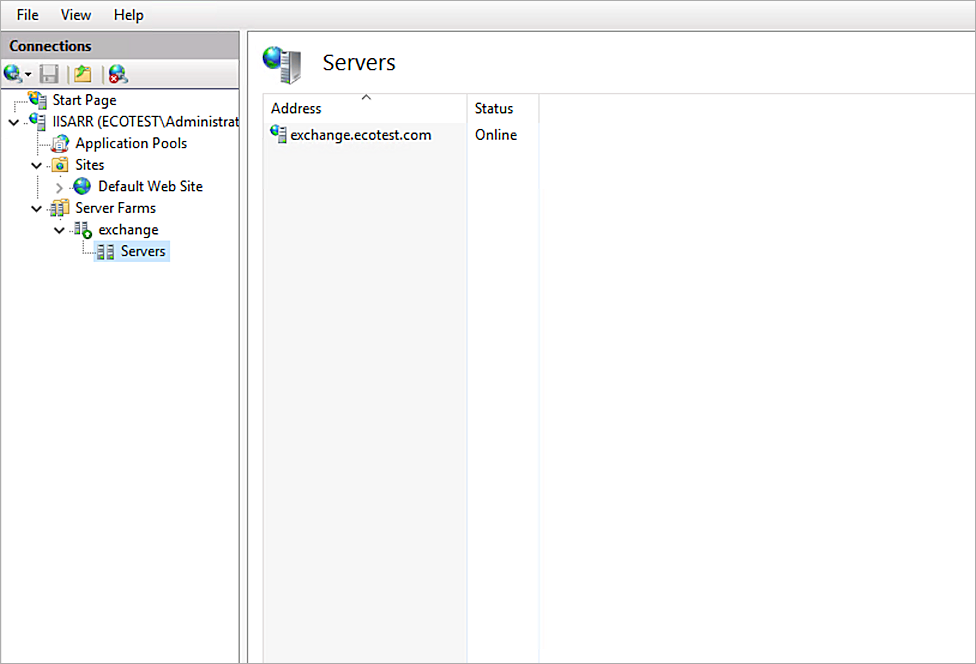
- Select the added Server Farm, then click Health Test.
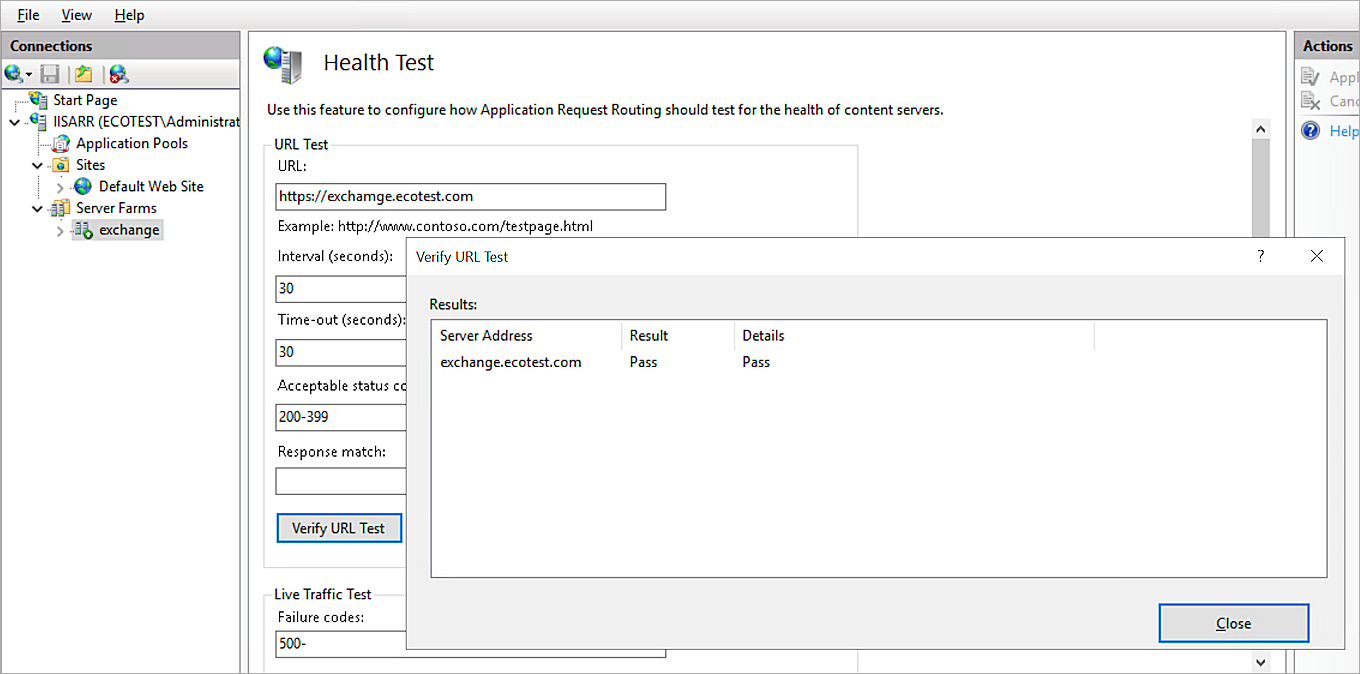
- To test the URL, in the Health Test settings:
- In the URL text box, type the URL of the Exchange server.
- Click Verify URL Test.
- Verify that the test result is Pass.
Configure the Firebox
Add Firebox Users
If you want to make the ARR server available only to specific users or groups, you must add those users or groups to Firebox-DB.
In this example, we use Firebox-DB, but you can use another authentication server for the Access Portal.
- Log in to Fireware Web UI at https://<IP address of Firebox>:8080.
- Select Authentication > Servers > Firebox-DB
- Add a new user for Firebox-DB authentication. Specify the user name and password. For more information, see Define a New User for Firebox Authentication and Define a New Group for Firebox Authentication.
Enable the Access Portal and Add the Web Application
- Select Subscription Services > Access Portal.
- Select the Enable Access Portal check box.
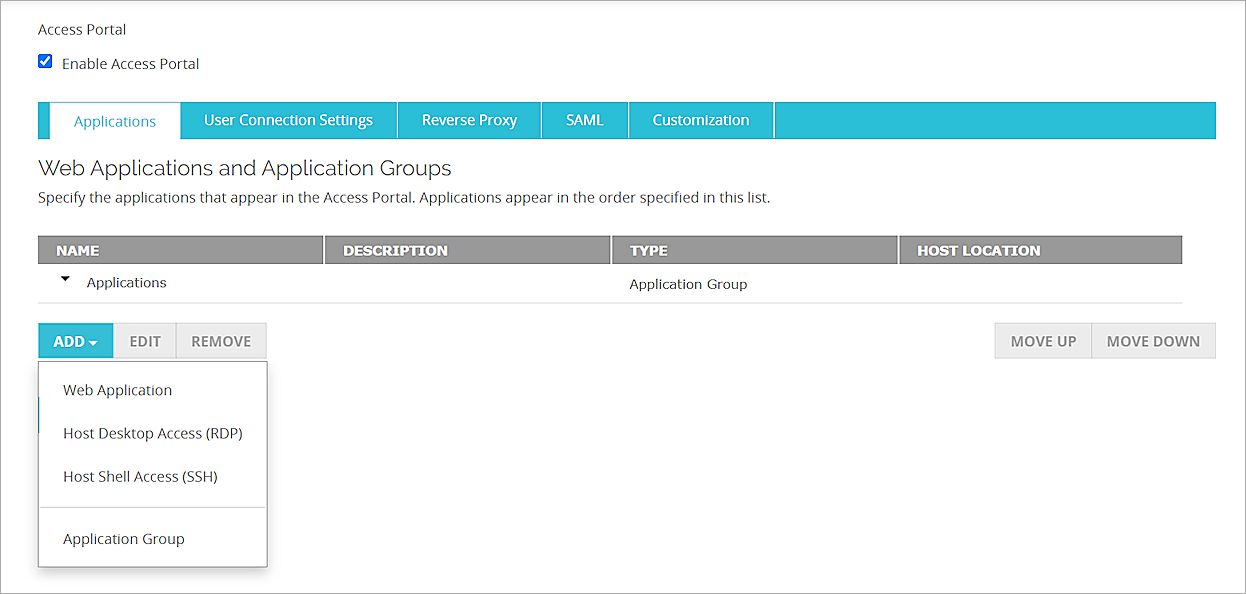
- In the Applications tab, select Add > Web Application.
The Add Web Application page appears. - In the Name text box, type the application name. In our example. this is Exchange.
- In the Description text box, type a description for this application.
- To upload a custom icon for this application, select Custom Icon (optional).
- In the URL text box, type the URL of the IIS ARR server.
- Click OK.
Configure the User Connection Settings
- Select the User Connection Settings tab.
- To give all users and groups permission to connect to all applications, select All applications are available to all users and groups authenticated with the Access Portal.
- To specify which users and groups can access which applications, select Specify the applications available to each user and group.
- Click Add, and select the Firebox-DB user or group which you added earlier.
- Select the application to make available to this user.
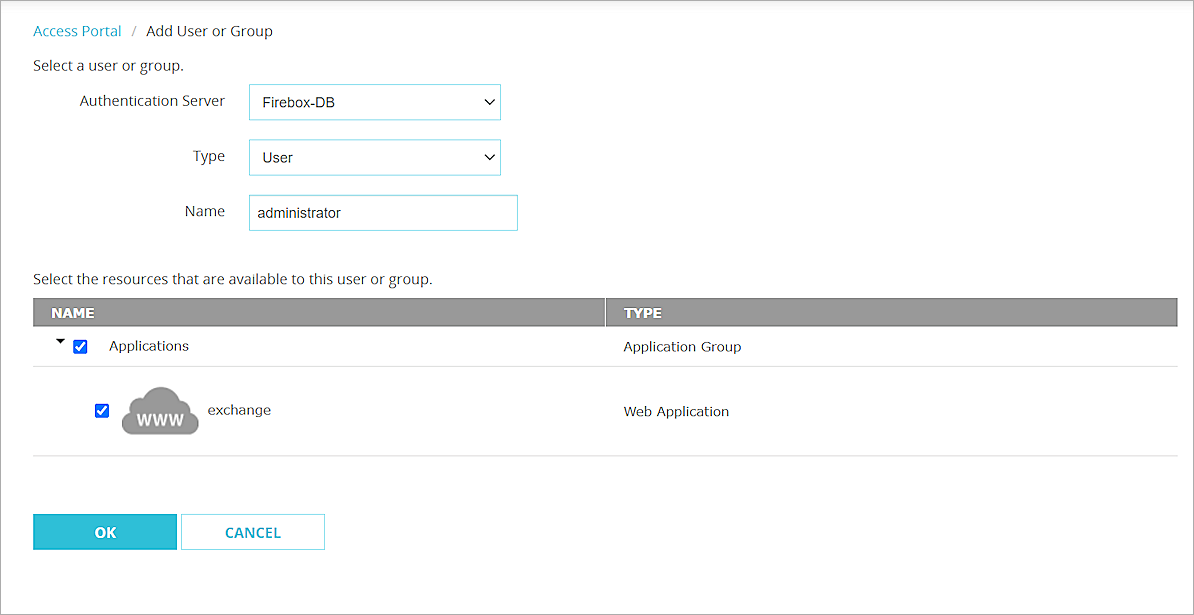
- Click OK.
- In the Authentication Servers list, select Firebox-DB.
- Click Save.
Add a Static NAT Action
Add a static NAT action for connections to the ARR server.
- Select Firewall > SNAT.
- Click Add.
- In the Name text box, type a name.
- In the Description text box, type a description (optional)
- Set the Type to Static NAT.
- In the SNAT Members list, click Add.
The Add Member dialogue box appears.
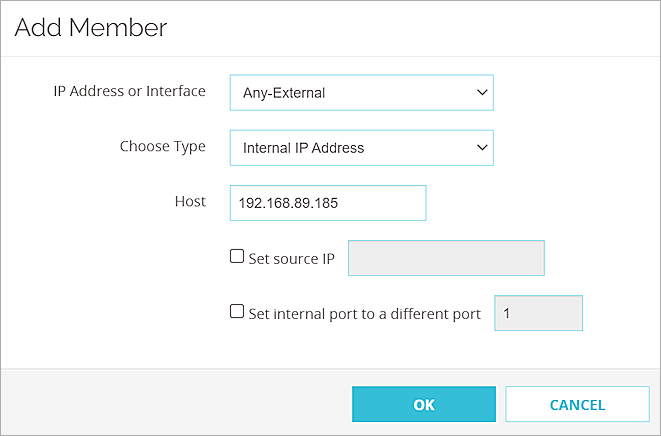
- From the IP Address or Interface drop-down list, select Any-External.
In Fireware v12.2 or lower, the IP Address or Interface drop-down list is named Externa/Optional IP Address.
- From the Choose Type drop-down list, select Internal IP Address
- In the Host text box, specify the IP address of the IIS ARR server on the private network.
- Click OK.
The SNAT member is added to the SNAT action.
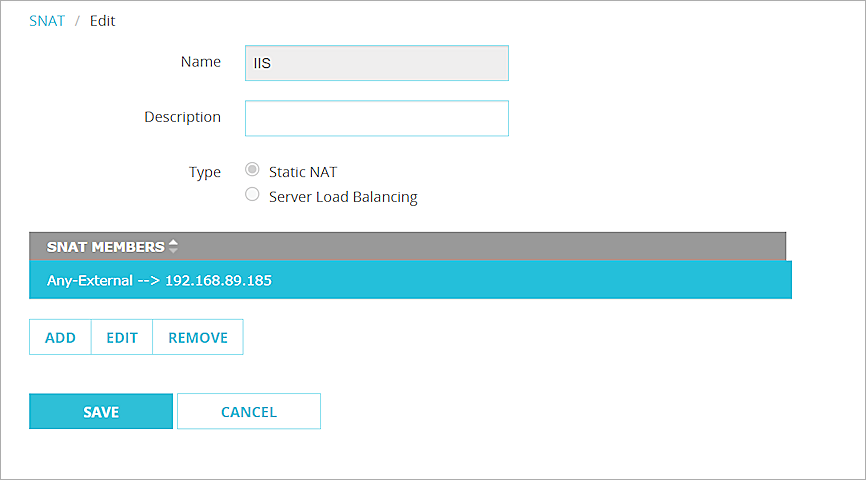
- Click Save.
Add a Policy for Connections to the ARR Server
Add an HTTPS proxy policy for connections through the Firebox to the ARR server. This policy uses the SNAT action you created earlier.
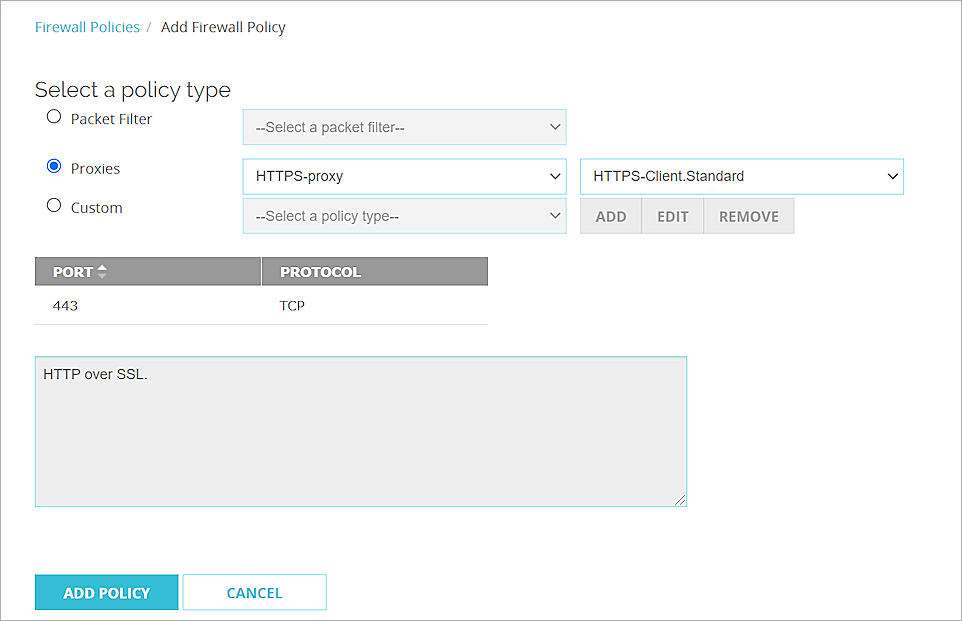
- Select Firewall > Firewall Policies.
- Click Add Policy.
- In the Select a policy type settings, select Proxies.
- From the Proxies drop-down list, select HTTPS-proxy, and select the HTTPS-Client.Standard proxy action.
- Click Add Policy.
- In the From list, add Any-External and Any-Optional.
- In the To list, add Any-Trusted, and the ARR SNAT action that you added earlier.
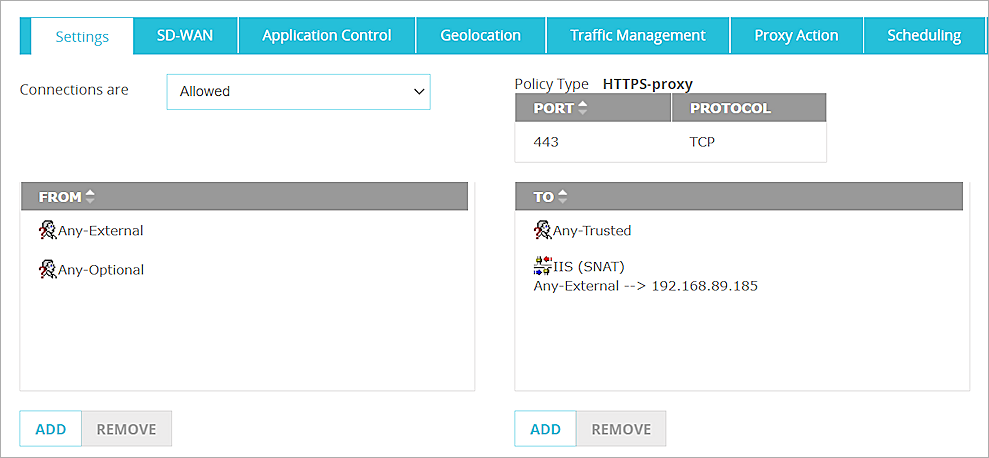
- Leave the default value for other policy settings. Click Save.
Test the Integration
- In a browser, go to https://<Firebox External IP address or FQDN>.

- Type your User Name and Password to authenticate to the Firebox.
- Click Log In.
The Access Portal appears.
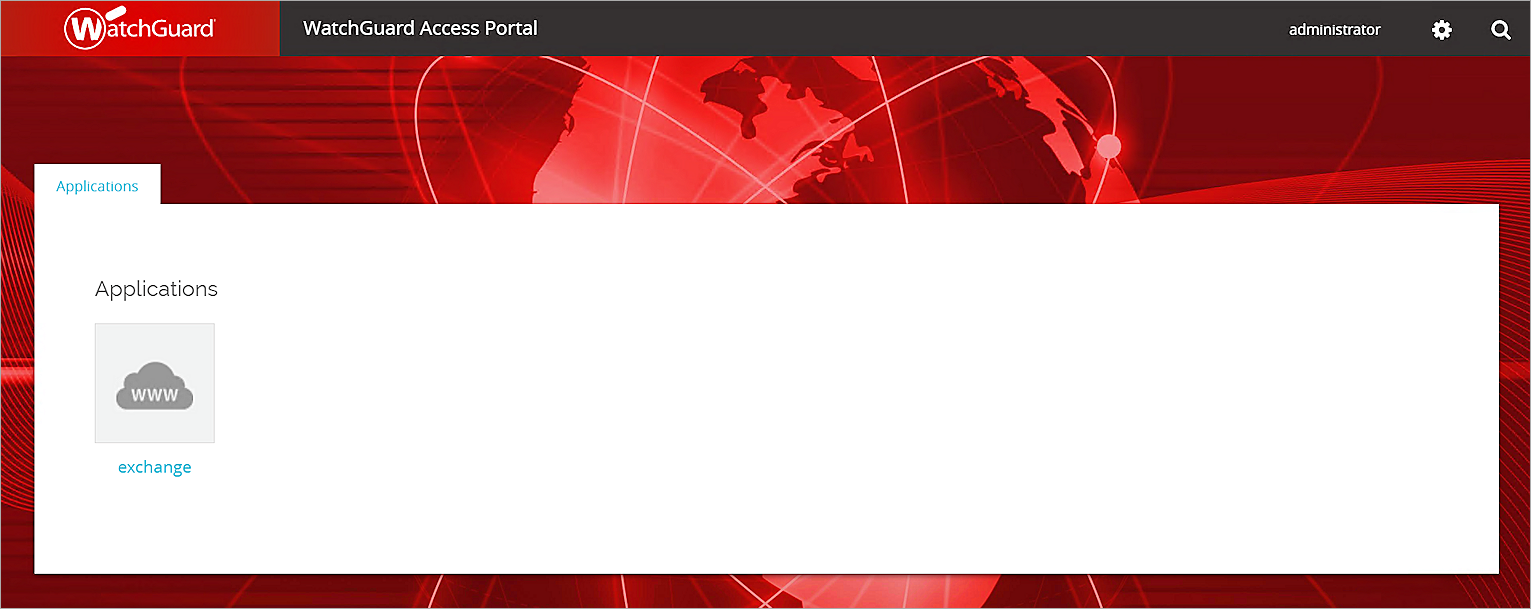
- Click the exchange application.
The browser goes to the ARR server URL. - Type the User name and Password to log in.
Exchange OWA successfully opens with ARR server URL.