Applies To: WatchGuard Advanced EPDR, WatchGuard EPDR, WatchGuard EDR, and WatchGuard EDR Core
In the Advanced Protection settings of a workstations and servers settings profile, you configure settings to track the activity of programs run on your computers and detect and block malicious programs. The Advanced Protection features available vary for each platform.
| Advanced Protection Feature | Windows (Intel & ARM) |
Linux |
Mac (Intel & ARM) |
Android |
iOS |
|---|---|---|---|---|---|
| Operating mode behavior |

|
||||
| Advanced security policies and blocked programs |

|
||||
| Windows Anti-Malware Scan Interface (AMSI) |

|
||||
| Anti-exploit protection, including code injection and vulnerable driver detection |

|
||||
| Network attack protection |

|
||||
| Privacy |

|

|

|
||
| Network usage |

|

|

|
For more information on supported features, go to Endpoint Security Supported Features by Platform.
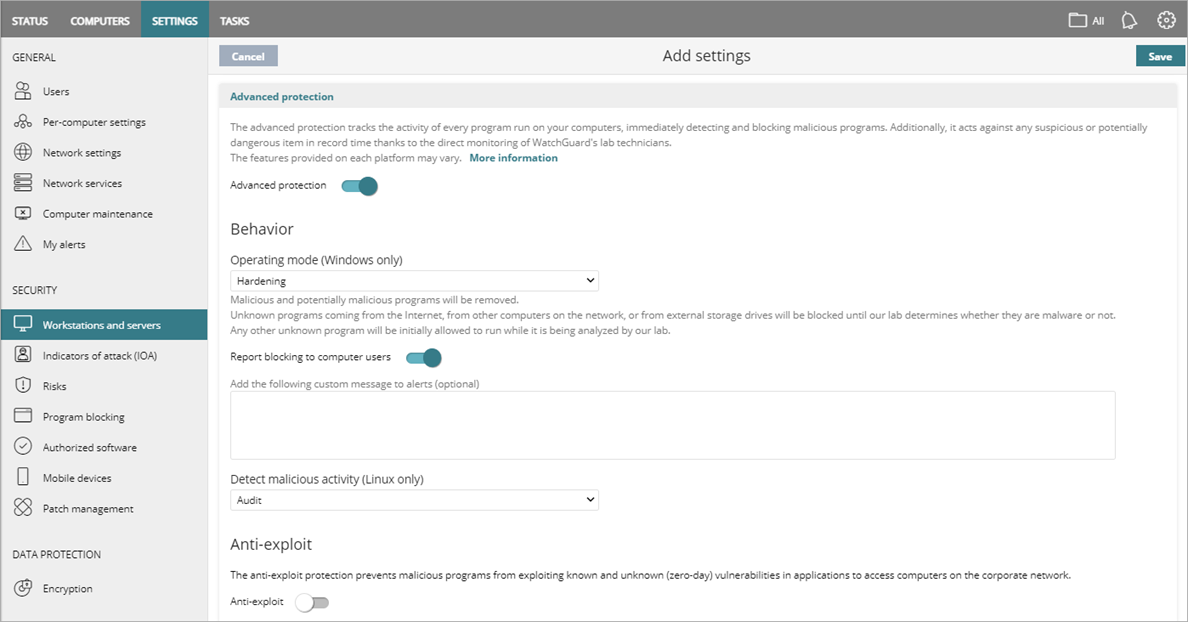
To configure Advanced Protection settings:
- In WatchGuard Cloud, select Configure > Endpoints.
- Select Settings.
- From the left pane, select Workstations and Servers.
- Select an existing security settings profile to edit, copy an existing profile, or in the upper-right corner of the window, click Add to create a new profile.
The Add Settings or Edit Settings page opens. - Enter a Name and Description for the profile, if required.
- Select Advanced Protection.
- Enable the Advanced Protection toggle.
- Configure settings as required:
- Configure Operating Mode Behavior (Windows Computers)
- Configure Advanced Security Policies (Windows Computers)
- Configure AMSI Advanced Scanning (Windows Computers)
- Configure Anti-Exploit Protection (Windows Computers)
- Configure Network Attack Protection (Windows Computers)
- Configure Privacy
- Configure Network Usage
- Click Save.
- Select the profile and assign recipients, if required.
For more information, go to Assign a Settings Profile.
Configure Operating Mode Behavior (Windows Computers)
Operating mode is not available with EDR Core or WatchGuard EPP.
When you allocate WatchGuard EDR or EDR Core to a new account, and the account does not have a workstations and servers settings profile assigned, the default profile assigned to the All group has decoy files disabled.
To configure operating behavior, in the Behavior section:
- For Windows computers, select an Operating Mode from the list (Audit, Hardening, or Lock).
For more information on operating modes, go to Advanced Protection – Operating Modes (Windows Computers).
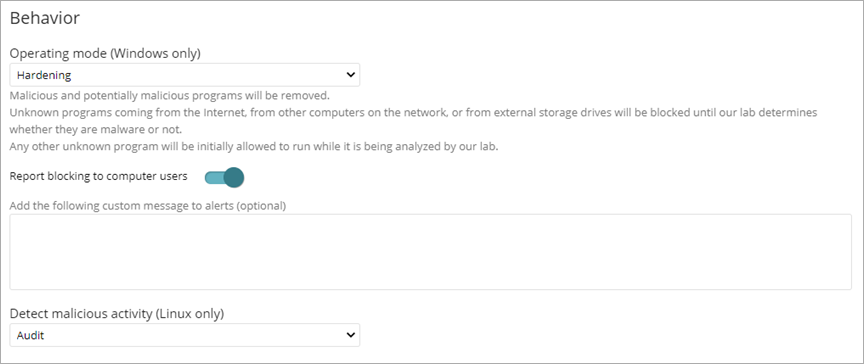
- To show a message in a pop-up alert on the user computer when advanced protection or anti-exploit features block a file, enable the Report Blocking to Computer Users toggle.
- (Optional) Type a custom message to include in the alert.
- For Linux computers, from the Detect Malicious Activity drop-down list, select the action to take when Endpoint Security detects malicious activity.
- Audit — Reports detected threats, but does not block malware.
- Block — Reports and blocks detected threats. This is the default option.
- Do Not Detect — Malware is not detected or reported.
Configure AMSI Advanced Scanning (Windows Computers)
Windows Anti-Malware Scan Interface (AMSI) provides telemetry and additional information about script and macro execution to improve antivirus protection for Windows computers. In a workstations and servers settings profile, advanced scanning with AMSI is enabled by default.
If you experience performance issues, you can add exclusions for problematic programs or disable advanced scanning with AMSI. We recommend that you only add exclusions for programs that might cause performance issues. When you add an exclusion, Endpoint Security does not scan the specified files and your computers could be at risk of an attack.
To add exclusions, in the AMSI section:
- Enable the toggle, if necessary.
- In the Programs text box, enter the file name for a program you want to exclude for advanced AMSI scanning.
Configure Anti-Exploit Protection (Windows Computers)
Anti-exploit technology is not available on Windows ARM systems.
Anti-exploit protection prevents malicious programs that exploit known and unknown (zero-day) vulnerabilities in applications to get access to computers on the corporate network. You can enable protection against code injection and protection for vulnerable drivers.
Code Injection is a general term for attacks that insert harmful code into an application that is then interpreted or executed by the application. For more information, go to About Anti-Exploit Protection (Windows Computers).
We recommend that you enable anti-exploit protection gradually on computers with a third-party security solution already installed to make sure it works properly.
When you allocate WatchGuard EDR or EDR Core to a new account, and the account does not have a workstations and servers settings profile assigned, the default profile assigned to the All group has anti-exploit disabled.
To configure anti-exploit protection:
- In the Anti-Exploit section, enable the Code Injection toggle.
If you disable Code Injection, it is disabled in all processes. It also disables PowerShell advanced policies. For information on PowerShell advanced policies, go to Configure Advanced Security Policies (Windows Computers). - If needed, add the file name in the Excluded Processes text box and press Enter.
Exploit attempts on excluded processes are not detected by anti-exploit protection. We recommend that you only add exclusions for programs that might cause performance issues. When you add an exclusion, Endpoint Security does not scan the specified files and your computers could be at risk of an attack. -
To make sure that Advanced Protection does not block an unclassified program, add it to the Authorized Software list.
For more information, go to Configure Authorized Software Settings (Windows Computers). - Select an Operating Mode from the list (Windows computers only):
- Audit — Reports exploit detections in the management UI, but does not take action against them or display information to the user.
- Block — Blocks exploit attacks. In some cases, it might be necessary to end the compromised process or restart the computer.
- To notify users when anti-exploit protection blocks a compromised process, enable the Report Blocking to the Computer User toggle.
The user receives a notification and the compromised process is automatically ended if required. - To prompt users to end a compromised process, enable the Ask the User for Permission to End a Compromised Process toggle.
Every time a compromised computer needs to restart, the user must provide confirmation, regardless of whether the toggle is enabled. - To detect vulnerable drivers that could be exploited, enable the Detect Drivers with Vulnerabilities toggle.
Vulnerable drivers are drivers that have vulnerabilities that have been used in the threat landscape. This can include outdated drivers that contain security gaps. Drivers supplied by legitimate vendors can contain vulnerabilities that malware could exploit to infect a computer or disable the security software. If the driver detected is part of the Windows boot process, it is not blocked. - Select an Operating Mode from the list (Windows computers only):
- Audit — Reports vulnerable drivers in the Exploit Activity tile on the Security dashboard and shows an alert on the affected computer. No action is taken.
- Block — Blocks vulnerable drivers from loading and shows an alert on the affected computer. Reports vulnerable drivers in the Exploit Activity tile on the Security dashboard.
To see driver details, select the affected computer in the Exploit Activity list. You can allow the blocked driver to run and stop allowing the driver if it was previously allowed. You can select to not detect the driver again. For more information, go to Allow Blocked Items to Run.
Many exploits continue to run malicious code until the relevant process ends. An exploit does not appear as resolved in the Exploit Activity tile on the Security dashboard until the compromised program terminates.
Configure Network Attack Protection (Windows Computers)
Network Attack Protection is not available with EDR Core or WatchGuard EPP.
Many security incidents begin with attacks that exploit vulnerabilities in Internet-exposed services. If malicious actors achieve their goal and infect computers in your organization, you must stop the attack. Network Attack Protection is enabled by default to block attacks in new accounts with WatchGuard Endpoint Security.
Network Attack Protection scans network traffic in real time to detect and stop threats. It prevents network attacks that attempt to exploit vulnerabilities in services that are open to the Internet and in the internal network. For more information, go to Network Attack Protection — Types of Attacks Detected (Windows Computers).
If you disable Network Attack Protection, it appears as a risk on the Risks dashboard. For more information, go to Security Risks Status in WatchGuard Endpoint Security.
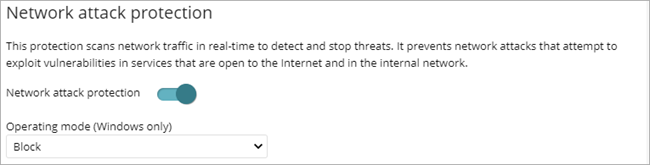
To enable network attack protection, enable the toggle. You can select the operating mode:
- Audit — Allows network attacks.
- Block — Blocks network attack before they can perform actions. This is the default option.
For a list of the attacks that WatchGuard Endpoint Security detects, go to Network Attack Protection — Types of Attacks Detected (Windows Computers).
You can send email alerts when Network Attack Protection detects a network attack. For more information, go to Configure Email Alerts.
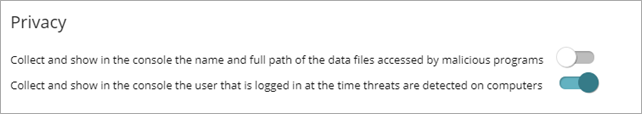
Configure Privacy
Endpoint Security collects the name and full path of the files it sends to WatchGuard Cloud for analysis, as well as the name of the logged in user. This information is used in the reports and forensic analysis tools shown in the management UI.
To enable data collection, in the Privacy section, enable the toggles.
Configure Network Usage
Endpoint Security sends every unknown executable file found on user computers to WatchGuard Cloud for analysis. This behavior is configured so that it has no impact on the customer’s network bandwidth:
- Endpoint Security only sends a compressed file up to 50 MB to WatchGuard Cloud each hour for each client.
- The WatchGuard Agent sends each unknown file once only for all customers who use Endpoint Security.
- Endpoint Security implements bandwidth management mechanisms to prevent intensive usage of network resources.
To configure network usage, in the Network Usage section:
- In the Maximum number of MBs that can be transferred in an hour text box, type the maximum number of MB to transfer between the computers and devices on your network and WatchGuard Cloud.
About Anti-Exploit Protection (Windows Computers)
Advanced Protection for Devices on Windows, Linux, and macOS Platforms