BOVPN Virtual Interface for Dynamic Routing to Amazon Web Services (AWS)
For VPN connections to AWS, we recommend that you configure a BOVPN virtual interface on the Firebox instead of a BOVPN. You can use static or dynamic routing.
In this example, we show a VPN configuration with:
- Dynamic BGP routing
- One Firebox external physical interface
- Two Firebox BOVPN virtual interfaces
- One AWS gateway with two IP addresses for failover
AWS does not support OSPF.
Configure AWS
An AWS VPN configuration includes one virtual private gateway with two external IP addresses for redundancy. AWS automatically determines which IP address is the primary IP address.
Failover between the external IP addresses is enabled by default. If the primary AWS external IP address is unavailable, VPN traffic automatically fails over to the other AWS external IP address.
For detailed instructions about how to configure the AWS VPN settings, go to the Amazon Virtual Private Cloud User Guide.
Download the AWS Configuration File
Before you configure the Firebox, download the configuration file from your AWS account:
- Log in to the AWS Management Console at https://aws.amazon.com/console.
- Click to expand All Services.
- In the Networking & Content Delivery section, click VPC.
- From the navigation menu, in the Virtual Private Network section, click Site-to-Site VPN Connections.
- Select the box for the connection.
- Click Download Configuration.
- From the Vendor drop-down list, select WatchGuard, Inc.
- From the Software drop-down list, select Fireware OS 11.12.2 +.
- Click Download.
A .txt file downloads to your desktop. - Open the .txt file in a text editor.
Find the AWS Pre-Shared Keys and IP Addresses
The .txt configuration file contains the pre-shared keys, gateway IP addresses for AWS Tunnel 1 and Tunnel 2, and routes to the trusted (private) network of your AWS VPC.
You can also find the IP addresses in your AWS configuration:
- For the gateway IP addresses, select Virtual Private Network > Site-to-Site VPN Connections > [name].
- For the routes, select Virtual Private Cloud > Subnets or Virtual Private Cloud > Route Tables.
For this example, the AWS configuration uses these IP addresses:
- Customer Gateway Address — 203.0.113.2 (external interface on the Firebox )
- VPN Connections:
- Tunnel 1 — 198.51.100.2 (first IP address of the AWS virtual private gateway)
- Tunnel 2 — 192.0.2.2 (second IP address of the AWS virtual private gateway)
- Static Route — 10.0.1.0/24 (trusted network of the Firebox)
Gateway ID — 203.0.113.2 (external interface on the Firebox)
Remote gateway IP address — 198.51.100.2 (first IP address of the AWS virtual private gateway)
Remote gateway ID — 198.51.100.2 (first IP address of the AWS virtual private gateway)
VPN route for the VPC
- Outside IP addresses:
- Customer Gateway — 203.0.113.2 (external interface on the Firebox)
- Virtual Private Gateway — 198.51.100.2 (first IP address of the AWS virtual private gateway)
- Inside IP addresses:
- Customer Gateway — 169.254.11.254/30 (virtual interface IP address of the first virtual interface on the Firebox) Tip!
- Virtual Private Gateway — 169.254.11.253 (IP address for the first virtual interface of the AWS VPN)
- BGP:
- Neighbor IP address — 169.254.11.254
- Customer Gateway ASN — 10001 (the BGP ASN of the Firebox)
- Outside IP addresses:
- Customer Gateway — 203.0.113.2 (external interface on the Firebox)
- Virtual Private Gateway — 192.0.2.2 (second IP address of the AWS virtual private gateway)
-
Inside IP addresses:
- Customer Gateway — 169.254.9.162/30 (virtual interface IP address of the second virtual interface on the Firebox) Tip!
- Virtual Private Gateway — 169.254.9.161 (IP address for the second virtual interface of the AWS VPN)
- BGP:
- Neighbor IP address — 169.254.9.162
- Customer Gateway ASN — 10001 (the BGP ASN of the Firebox)
Configure the Firebox
For this example, the Firebox has one external interface and one trusted network:
| Interface | Type | Name | IP Address |
|---|---|---|---|
| 0 | External | External | 203.0.113.2/24 |
| 1 | Trusted | Trusted | 10.0.1.1/24 |
Add the BOVPN Virtual Interfaces
To configure a redundant gateway that uses both AWS external IP addresses, you must configure two BOVPN virtual interfaces.
- Select VPN > BOVPN Virtual Interfaces.
- Click Add.
- In the Interface Name text box, type a name that describes the virtual interface. In our example, we use toAWS-1.
- From the Remote Endpoint Type drop-down list, select Cloud VPN or Third-Party Gateway.
- From the Gateway Address Family drop-down list, select IPv4 Addresses. AWS does not support IPv6 for VPN tunnels.
- For the credential method, select Use Pre-Shared Key.
- Specify the pre-shared key included in the AWS VPN configuration file for IPSec Tunnel #1. AWS supports only the pre-shared key authentication method for site-to-site VPNs.
- In the Gateway Endpoint section, click Add.
The Gateway Endpoint Settings dialog box appears. - From the Physical drop-down list, select External.
- From the Interface IP Address drop-down list, select Primary IPv4 Interface Address.
- Select By IP Address.
- In the adjacent text box, type the IP address for the Firebox external interface. In our example, we use 203.0.113.2.
- Select the Remote Gateway tab.
- Select Static IP Address.
- In the adjacent text box, type the first IP address of the AWS virtual private gateway. In our example, we use 198.51.100.2.

- Select VPN > BOVPN Virtual Interfaces.
- Click Add.
- In the Interface Name text box, type a name that describes the virtual interface. In our example, we use toAWS-2.
- From the Remote Endpoint Type drop-down list, select Cloud VPN or Third-Party Gateway.
- From the Gateway Address Family drop-down list, select IPv4 Addresses. AWS does not support IPv6 for VPN tunnels.
- For the credential method, select Use Pre-Shared Key.
- Specify the pre-shared key included in the AWS VPN configuration file for IPSec Tunnel #2. AWS supports only the pre-shared key authentication method for site-to-site VPNs.
- In the Gateway Endpoint section, click Add.
The Gateway Endpoint Settings dialog box appears. - From the Physical drop-down list, select External.
- From the Interface IP Address drop-down list, select Primary IPv4 Interface Address.
- Select By IP Address.
- In the adjacent text box, type the IP address for the Firebox external interface. In our example, we use 203.0.113.2.
- Select the Remote Gateway tab.
- Select Static IP Address.
- In the adjacent text box, type the first IP address of the AWS virtual private gateway. In our example, we use 192.0.2.2.
- Click OK.

Configure the Virtual Interface IP Address and Netmask
- Select the VPN Routes tab.
- Select Assign virtual interface IP addresses.
- In the Local IP address text box, type the IP address. In our example, we use 169.254.11.254 .
In the AWS VPN Configuration file, in the IPSec Tunnel #1 section, this is the Inside Customer Gateway IP address. - In the Peer IP address or netmask text box, type the netmask. The netmask assigned by AWS is always /30 (255.255.255.252).
In the AWS VPN Configuration file, in the IPSec Tunnel #1 section, this is the Inside Customer Gateway netmask.

- Select the VPN Routes tab.
- Select Assign virtual interface IP addresses.
- In the Local IP address text box, type the IP address. In our example, we use 169.254.9.162 .
In the AWS VPN Configuration file, in the IPSec Tunnel #2 section, this is the Inside Customer Gateway IP address. - In the Peer IP address or netmask text box, type the netmask. The netmask assigned by AWS is always /30 (255.255.255.252).
In the AWS VPN Configuration file, in the IPSec Tunnel #2 section, this is the Inside Customer Gateway netmask.

Configure the Phase 1 and Phase 2 Settings
During VPN negotiations, AWS identifies the authentication and encryption algorithm settings from the Firebox. If AWS supports the settings, AWS automatically uses the same settings. AWS supports specific proposals. You cannot edit the AWS configuration to specify different proposals.
In Fireware v12.10 and higher, Fireware supports Diffie-Hellman Group 21.
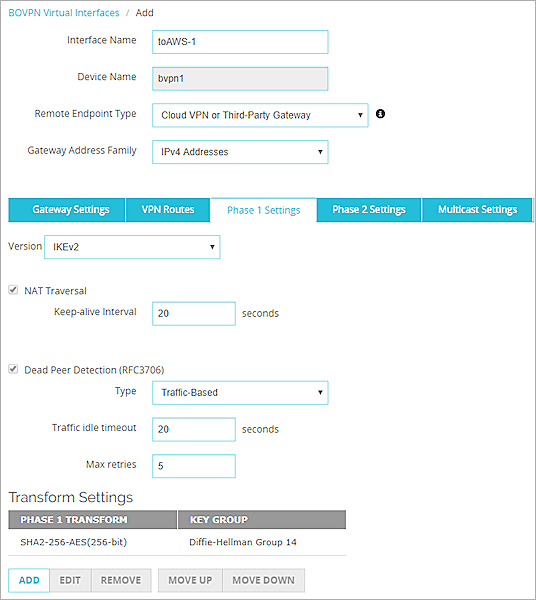
- Select the Phase 1 Settings tab.
- From the Version drop-down list, select IKEv2. AWS also supports IKEv1.
- In the Transform Settings section, click Add.
The Transform Settings dialog box appears. - From the Authentication drop-down list, select SHA2-256. AWS also supports SHA-1.
- From the Encryption drop-down list, select AES (256-bit). AWS also supports AES (128-bit) is also supported.
- From the Diffie-Hellman Group drop-down list, select 14. AWS also supports groups 2, 15, 19, 20, and 21.
- Click OK and keep all other Phase 1 settings at the default values.
- Select Enable Perfect Forward Secrecy.
- From the drop-down list, select Diffie-Helman Group 14.
Groups 1, 2, 5, 15, 19, 20, and 21 are also supported. - From the IPSec Proposals drop-down list, select ESP-AES256-SHA256.
SHA1 and AES128 are also supported. - Repeat these steps to configure the Phase 2 settings for the second BOVPN virtual interface.

Specify BGP Commands
The AWS BGP ASN and the virtual IP address (the BGP peer address) are defined by AWS and cannot be changed.
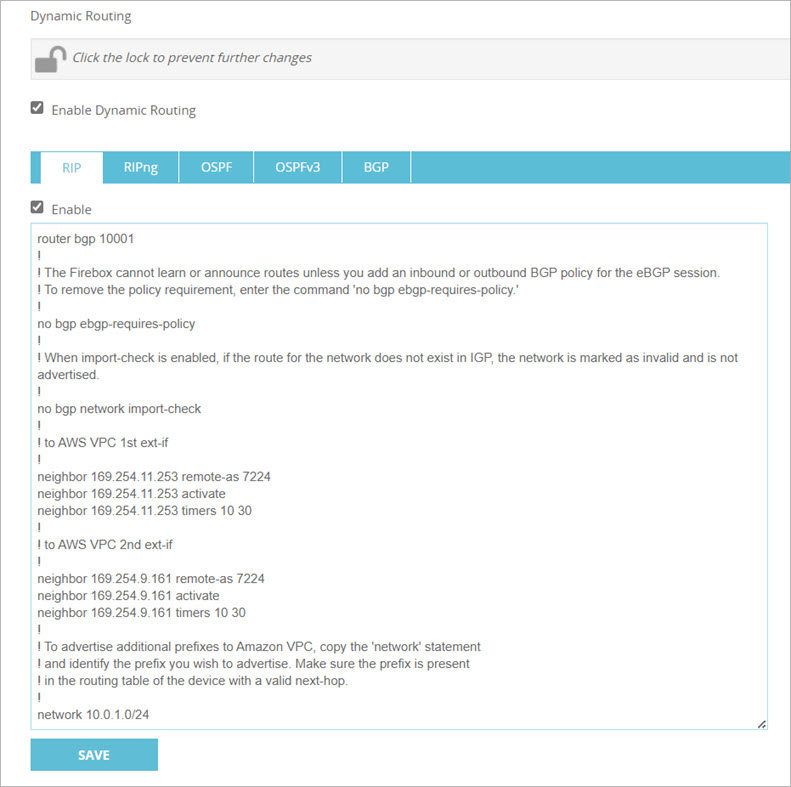
- Select Network > Dynamic Routing.
- Select Enable Dynamic Routing.
- Select the BGP tab.
- Select the Enable check box.
- Specify the BGP commands. In our example, we specify these commands:
router bgp 10001
!
! The Firebox cannot learn or announce routes unless you add an inbound or outbound BGP policy for the eBGP session. ! To remove the policy requirement, enter the command 'no bgp ebgp-requires-policy.'
!
no bgp ebgp-requires-policy
!
! When import-check is enabled, if the route for the network does not exist in IGP, the network is marked as invalid and is not advertised.
!
no bgp network import-check
!
! to AWS VPC 1st ext-if
!
neighbor 169.254.11.253 remote-as 7224
neighbor 169.254.11.253 activate
neighbor 169.254.11.253 timers 10 30
!
! to AWS VPC 2nd ext-if
!
neighbor 169.254.9.161 remote-as 7224
neighbor 169.254.9.161 activate
neighbor 169.254.9.161 timers 10 30
!
! To advertise additional prefixes to Amazon VPC, copy the 'network' statement
! and identify the prefix you wish to advertise. Make sure the prefix is present
! in the routing table of the device with a valid next-hop.
!
network 10.0.1.0/24
If you configure more than one trusted network on your Firebox, and you want AWS to learn the route to an additional trusted network, use an additional network command. For example:
network 10.0.1.0/24
network 10.0.2.0/24
BOVPN Virtual Interface for Static Routing to Amazon Web Services (AWS)