Configure Phase 2 Settings
Phase 2 settings include settings for a security association (SA), which defines how data packets are secured when they are passed between two endpoints. The SA keeps all information necessary for the Firebox to handle traffic between the endpoints. Parameters in the SA can include:
- Encryption and authentication algorithms used.
- Lifetime of the SA (in seconds or number of bytes, or both).
- The IP address of the device for which the SA is established (the device that handles IPSec encryption and decryption on the other side of the VPN, not the computer behind it that sends or receives traffic).
- Source and destination IP addresses of traffic to which the SA applies.
- Direction of traffic to which the SA applies (there is one SA for each direction of traffic, incoming and outgoing).
You can add more than one Phase 2 proposal in the Phase 2 Settings tab. However, you cannot add AH and ESP phase 2 proposals to the IPSec Proposals list for the same VPN tunnel.
If you plan to use the IPSec pass-through feature, you must use a proposal with ESP (Encapsulating Security Payload) as the proposal method. IPSec pass-through supports ESP but not AH. For more information on IPSec pass-through, see About Global VPN Settings.
The Phase 2 Settings also include a setting for Perfect Forward Secrecy (PFS). Perfect Forward Secrecy gives more protection to keys that are created in a session. Keys made with PFS are not made from a previous key. If a previous key is compromised after a session, your new session keys are secure. For more information, go to About Diffie-Hellman Groups.
The Phase 2 settings you can configure are the same for a BOVPN gateway or a BOVPN virtual interface.
- From the Branch Office VPN page for a tunnel or the BOVPN Virtual Interface page, select the Phase 2 Settings tab.
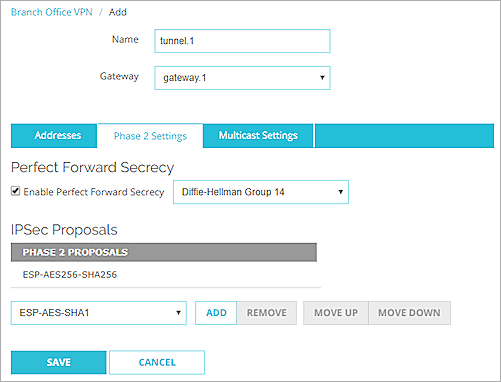
- By default, Perfect Forward Secrecy (PFS) is enabled, and Diffie-Hellman Group 14 is specified. You can disable PFS or select a different Diffie-Hellman group.
- By default, a VPN tunnel contains one default proposal, which appears in the IPSec Proposals list. This proposal specifies the ESP data protection method, AES 256-bit encryption, and SHA2-256 authentication. You can select a different proposal from the drop-down list and click Add.
If the proposal you want to use is not in the list, you can add an additional proposal, as explained in Add a Phase 2 Proposal.
- From the New Tunnel dialog box or the New BOVPN Virtual Interface dialog box, select the Phase 2 Settings tab.

- By default, Perfect Forward Secrecy (PFS) is enabled, and Diffie-Hellman Group 14 is specified. You can disable PFS or select a different Diffie-Hellman group.
- By default, a VPN tunnel contains one default proposal, which appears in the IPSec Proposals list. This proposal specifies the ESP data protection method, AES 256-bit encryption, and SHA2-256 authentication. You can either:
- Use the default proposal.
- Remove the default proposal and replace it with a new one.
- Add an additional proposal, as explained in Add a Phase 2 Proposal.