To increase network performance and scalability, you can configure a FireCluster, which is the high availability (HA) solution for WatchGuard Fireboxes.
- FireCluster Overview
- FireCluster Types
- About FireCluster Failover
- Cluster Member Roles
- FireCluster Supported Features
- Configure FireCluster
- Monitor FireCluster Status
- About FireCluster in WatchGuard Cloud
- Disable FireCluster
FireCluster Overview
A FireCluster includes two Fireboxes configured as cluster members. If a cluster member fails, the other cluster member takes over.
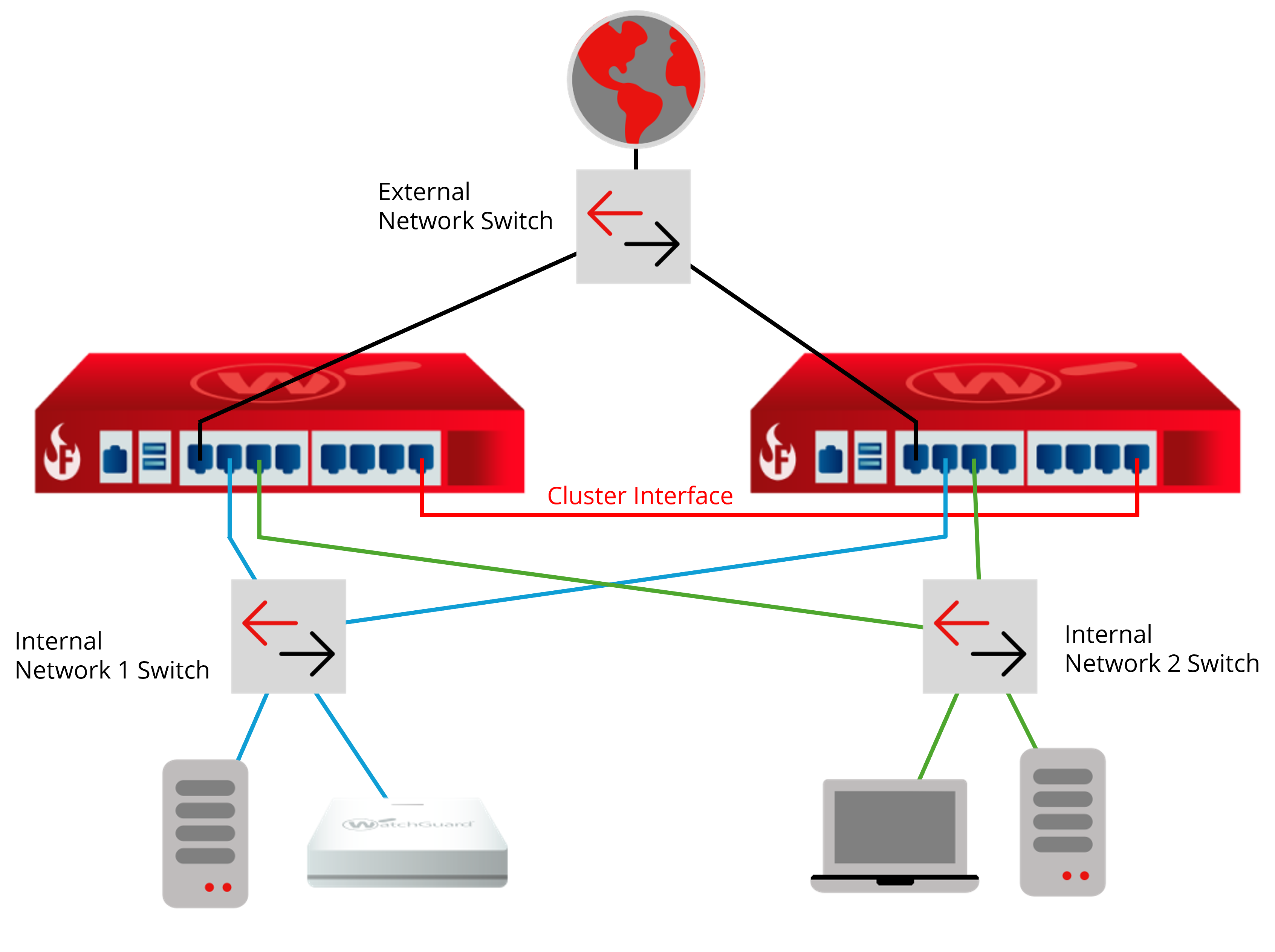
In this example, the FireCluster has one external and one trusted interface connected to network switches. The primary cluster interfaces are connected by an Ethernet cable.
For more information about hardware connections and an additional example for multi-WAN configurations, go to Connect the FireCluster Hardware.
FireCluster Types
FireCluster supports two types of cluster configurations.
- Active/Passive cluster — In an active/passive cluster, one cluster member is active, and the other is passive. The active cluster member handles all network traffic unless a failover event occurs. The passive cluster member actively monitors the status of the active device. If the active device fails, the passive device takes over the connections assigned to the failed device.
- Active/Active cluster — In an active/active cluster, the cluster members share the traffic that passes through the cluster. To distribute connections between the active Fireboxes in the cluster, configure FireCluster to use a round-robin or least connections algorithm. If one member of a cluster fails, the other cluster member takes over the connections assigned to the failed member. The same cluster member handles response traffic unless that member fails. For example, Cluster Member 1 is assigned an outbound packet from a user computer on your local network. Cluster Member 1 also handles the response traffic. This packet flow occurs because the Firebox is a stateful firewall that tracks and controls network traffic in a layer 3 session. Cluster Member 2 does not handle the response packet unless Member 1 fails.
For both active/passive and active/active clusters, all traffic for traffic interfaces on either cluster member is delivered to both cluster members. This occurs because cluster members share the same virtual mac address (VMAC).
For more information on requirements for active/passive and active/active FireClusters, go to Before You Configure a FireCluster.
You can also enhance performance and achieve full redundancy with a FireCluster through the configuration of link aggregation. This method enables a group of physical interfaces to function as a single, logical interface, and results in a comprehensive mesh configuration. For more information, go to About Link Aggregation.
About FireCluster Failover
For more information about FireCluster failover, go to About FireCluster Failover.
When a cluster member fails, FireCluster seamlessly fails over and maintains:
- Packet filter connections
- BOVPN tunnels
- User sessions
- Access Portal user sessions
When FireCluster fails over, these connections might be disconnected:
- Proxy connections
- Mobile VPN connections
- RDP and SSH connections initiated through the Access Portal
Mobile VPN users might have to manually restart the VPN connection after a failover.
For interfaces included in multi-WAN or link aggregation configurations:
- Multi-WAN — FireCluster failover is triggered when the physical interface is down or does not respond. FireCluster failover is not triggered if multi-WAN failover occurs because of a link monitor failure.
- Link Aggregation — FireCluster failover is triggered if all Link Aggregation member interfaces fail. FireCluster failover is not triggered if only some Link Aggregation member interfaces fail.
Cluster Member Roles
It is important to understand the roles each Firebox can play in the cluster.
Cluster Master
The cluster master assigns network traffic flows to other cluster members, and responds to all requests from external systems such as WatchGuard System Manager, SNMP, DHCP, ARP, routing protocols, and IKE. When you configure or modify the cluster configuration, you save the cluster configuration to the cluster master. The cluster master can be either device. The first device in a cluster to power on becomes the cluster master.
Backup Master
This cluster member synchronizes all necessary information with the cluster master so that it can become the master if the current cluster master fails. The Backup cluster master can be active or passive.
Active Member
This can be any cluster member that actively handles traffic flow. In an active/active cluster, both devices are active. In an active/passive cluster, the cluster master is the only active device.
Passive Member
A Firebox in an active/passive cluster that does not handle network traffic flows unless an active device fails over. In an active/passive cluster the passive member is the backup master.
FireCluster Supported Features
When FireCluster is enabled, your Fireboxes continue to support:
- Secondary networks on external, trusted, or optional interfaces
- Multi-WAN connections
A multi-WAN failover caused by a failed connection to a link monitor host does not trigger FireCluster failover. FireCluster failover occurs only when the physical interface is down or does not respond. - VLANs
- Dynamic routing
For information about features not supported for a FireCluster, go to Features Not Supported for a FireCluster.
Configure FireCluster
We highly recommend you review the list of FireCluster requirements before you configure a FireCluster. For more information, go to Before You Configure a FireCluster.
For an overview on how to configure a FireCluster, go to Configure FireCluster.
For quick start setup instructions, go to Quick Start — Set Up a FireCluster.
Monitor FireCluster Status
After you configure FireCluster, you can view the cluster status when you connect to the cluster with:
- WatchGuard System Manager
- Firebox System Manager — Go to Device Status.
- Fireware Web UI — Select System Status > FireCluster. You Firebox must have Fireware v12.3 or higher.
After you configure a cluster in Policy Manager, you can use Fireware Web UI to connect to it. You can use the Web UI to monitor the cluster and update policies and other configuration settings, but you cannot use the Web UI to modify the FireCluster settings.
When you use Fireware Web UI to connect to devices configured as a cluster, it is important to understand the cluster member roles.
Cluster Master
The cluster master assigns network traffic flows to other cluster members, and responds to all requests from external systems such as WatchGuard System Manager, SNMP, DHCP, ARP, routing protocols, and IKE. When you configure or modify the cluster configuration, you save the cluster configuration to the cluster master. The cluster master can be either device. The first device in a cluster to power on becomes the cluster master.
Backup Master
The backup cluster master synchronizes all necessary information with the cluster master so that it can become the master if the current cluster master fails. You cannot use Fireware Web UI to save configuration changes to the backup cluster master.
About FireCluster in WatchGuard Cloud
In WatchGuard Cloud, you can add a locally-managed FireCluster, initiate system actions (upgrade, reboot, and fail over), and view log messages. For more information, go to About FireCluster in WatchGuard Cloud.
Disable FireCluster
If you no longer want your Fireboxes configured in a cluster and want to break the cluster, you can disable and remove the FireCluster configuration. When you disable FireCluster, one cluster member reboots and keeps its current configuration, and the other cluster member reboots with factory-default settings.
For more information, go to Disable FireCluster.
Before You Configure a FireCluster
FireCluster (Video)
Monitor and Control FireCluster Members
FireCluster Upgrade, Downgrade, Backup, Restore, and Migration