Applies To: WatchGuard Advanced EPDR, WatchGuard EPDR, WatchGuard EDR
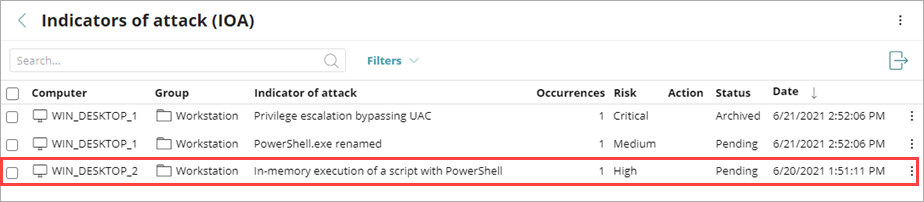
To open the details page for an IOA, in the Indicators of Attack (IOA) list, click a computer row.
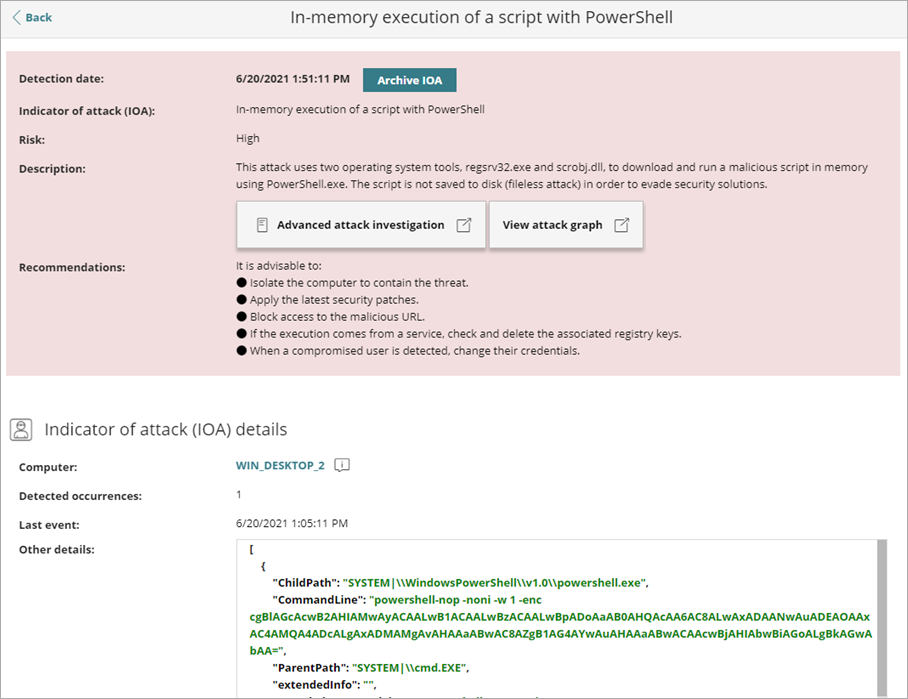
From the details page, you can review a description of the IOA and recommended actions. You can also archive the IOA. For information on how to archive an IOA, go to Archive an Indicator of Attack.
In the notification section of the page, you can review this information:
- Detection Date — Date and time when WatchGuard Endpoint Security detected the IOA on the workstation or server. Displayed in the user's time zone.
- Indicator of Attack — Name of the indicator of attack.
- Risk — Risk level of the indicator of attack (Critical, High, Medium, Low, or Unknown)
- Description — Description of the chain of events detected on the
computer, and the consequences it
could have if the attack achieves its objectives.
- To see a description of the tactics and techniques used on the affected computer, click Advanced Attack Investigation. A new tab opens with the report. Reports are available for a month after the IOA is generated. The report also shows events that are part of the attack during the 30 days prior to detection of the IOA.
If the IOA has a graph associated with it, click View Attack Graph to see an interactive diagram with the sequence of events that led to the generation of the IOA. For more information, go to About Attack Graphs.
- Action — Type of action taken by Endpoint Security.
- Recommendations — Recommended actions for the administrator from the WatchGuard Security team.
Indicator of Attack Details Section
The Indicator of Attack details section shows the affected computer, the number of detected occurrences, and the date and time of the last event. For Advanced EPDR only, there is a Details tab and an Investigation tab. To open the computer details page, click the computer name.
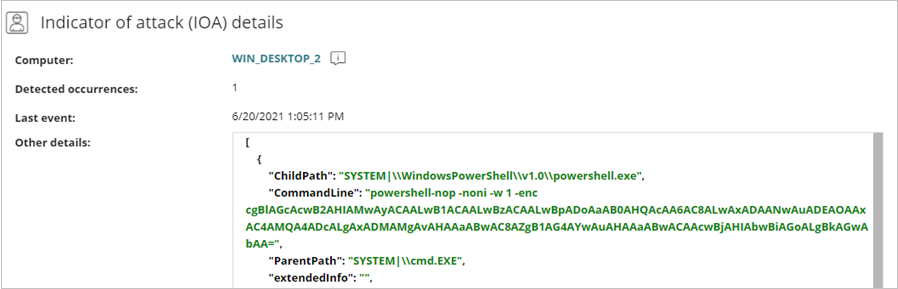
To open the Activity page from the Details page, click View Full Activity Details. For information on the Activity page, go to Activity Tab.
To open the Investigation page from the Details page, click View Computer Investigation or click the Investigation tab. For information on the Investigation page, go to Computer Telemetry on the Investigation Page.
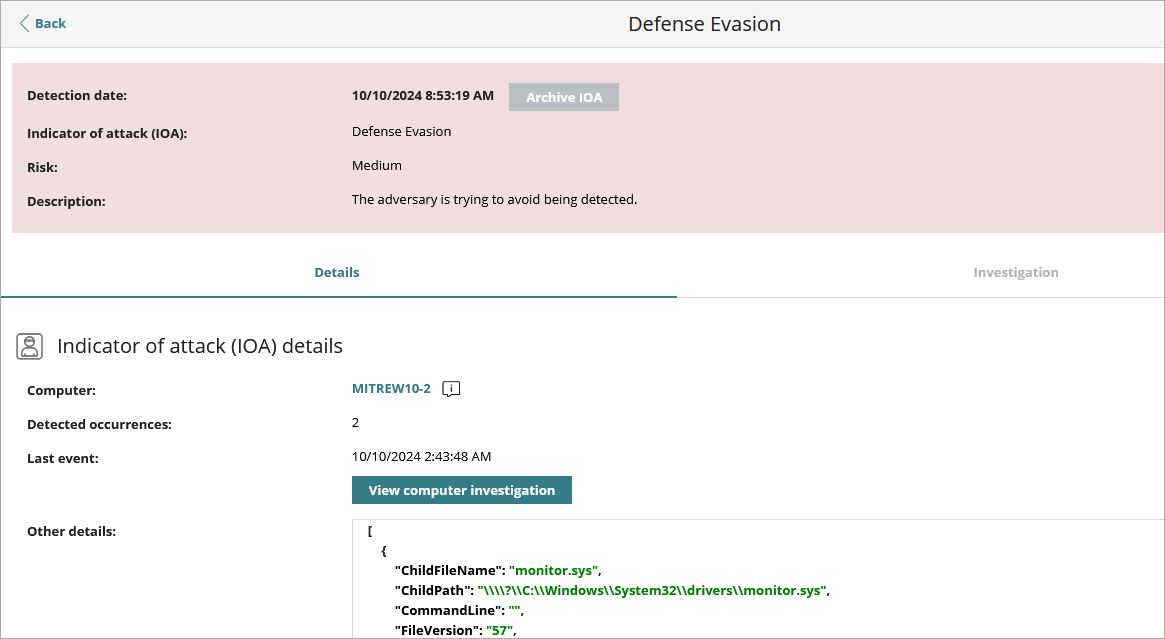
The Other Details text box provides data in JSON format that includes fields relevant to the event that led to the generation of the IOA.
MITRE Section
The MITRE section of the page shows details of the attack, mapped to the MITRE ATT&CK matrix.
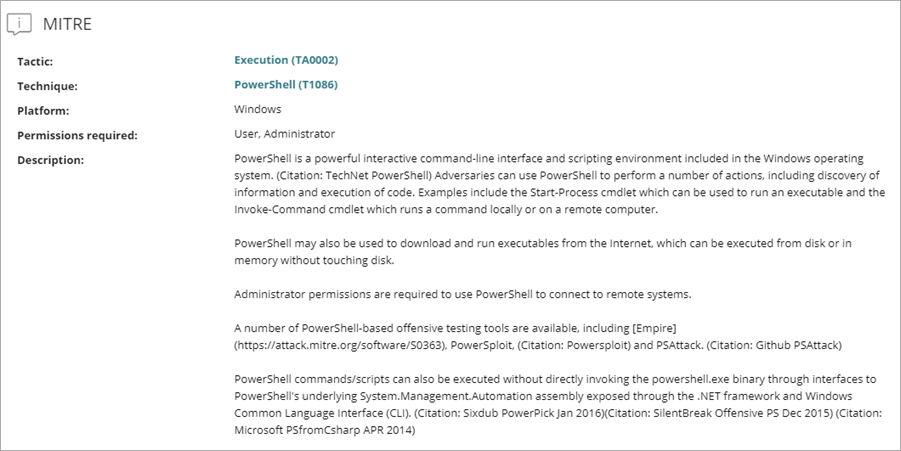
For each attack, these details are available:
- Tactic — Category of the attack tactic that generated the IOA, mapped to the MITRE matrix. Click the tactic to open a new window with detailed MITRE information on the tactic.
- Technique / Sub-technique — Category and sub-category (if available) of the attack technique that generated the IOA, mapped to the MITRE matrix (for example, T1012 - Query Registry). Click the technique to open a new window with detailed MITRE information on the technique.
- Platform — Operating system and environments where MITRE previously recorded this type of attack.
- Permissions Required — Permissions required to run the attack.
- Description — Details of the tactics and techniques used by the IOA detected, according to the MITRE matrix.
Activity Tab
Advanced indicators of attack are compatible with Windows, Linux, and Mac computers.
The IOA details page for endpoints with WatchGuard Advanced EPDR includes Details, Activity, and Investigation tabs. The information on the Details page is described in the previous section. For information on the Investigation page, go to Computer Telemetry on the Investigation Page.
On the Activity page, you can see the detected actions for the IOA, such as when the activity was detected and the MITRE technique.
- Date — When Advanced EPDR detected the action. Displayed in the user's time zone.
- Action — The action Advanced EPDR detected.
- Technique / Sub-Technique — The MITRE technique (and sub-technique, if available). The MITRE ID and name show in the label (for example, T1012 - Query Registry). Sub-techniques refer to the processes or mechanisms used by adversaries to achieve the objective of a tactic. For example, password spraying is a type of brute force attack to accomplish the objective of the Credential Access tactic.
To show detailed information (for example, event type, parent, and child information) in the Event Details dialog box, click a row in the table. On the MITRE tab, you can review detailed MITRE information (for example, tactic, technique, sub-technique, and description).