Applies To: WatchGuard Advanced EPDR, WatchGuard EPDR, WatchGuard EDR
On the Indicators of Attack dashboard, the Threat Hunting Service tile shows when computers are in RDP Attack Containment mode. RDP Attack Containment mode protects against scenarios where a hacker gets access to the IT network through a vulnerable computer, then looks laterally for other unprotected devices, and uses RDP to move from one device to another.
WatchGuard Endpoint Security monitors attempts to connect to a computer on the IT network through the RDP service. When numerous failed attempts originate from a single IP address, WatchGuard Endpoint Security enables RDP Attack Containment mode on the affected computer.
Initial RDP Attack Containment Mode
When a computer receives a large number of RDP connection attempts that fail due to invalid credentials, WatchGuard Endpoint Security generates a Brute-force attack against RDP IOA and puts the computer into Initial RDP attack containment mode.
In this mode, RDP access to the computer is blocked from IPs outside the customer network that have sent a large number of connection attempts over the last 24 hours.
If you do not want to block connections from specific allowed IP addresses, you can add those IPs to the allowlist. For more information, go to Configure RDP Attack Settings.
Restrictive RDP Attack Containment Mode
When the attacker is able to successfully log in to an account that previously failed due to invalid credentials, the computer in Initial RDP Attack Containment mode moves to the Restrictive RDP Attack Containment mode.
WatchGuard Endpoint Security generates a Credentials compromised after brute-force attack on RDP IOA, The account is considered to be compromised. All external RDP connections that have tried to connect at least once with the target computer in the previous 24 hours are blocked.
To open a list of computers in RDP Attack Containment mode:
- On the Status > Indicators of Attack dashboard, click View All in the Threat Hunting Service tile.
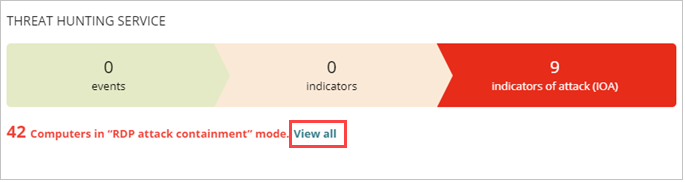
The Computer Protection Status list opens filtered to show computers with RDP Attack Containment mode enabled.
In the Computer Protection Status list, a red RDP ![]() icon indicates that RDP Attack Containment mode is enabled. The RDP icon flashes orange until WatchGuard Endpoint Security disables RDP Attack Containment mode.
icon indicates that RDP Attack Containment mode is enabled. The RDP icon flashes orange until WatchGuard Endpoint Security disables RDP Attack Containment mode.
End RDP Attack Containment Mode
Twenty-four hours after containment mode begins, WatchGuard Endpoint Security evaluates the number of connection attempts via RDP. If it is below default threshold, WatchGuard Endpoint Security automatically ends RDP Attack Containment mode. If the attempts continue, then the containment mode continues for another 24 hours.
When you consider the network secure and there is no longer any danger of an RDP attack, you can manually end RDP Attack Containment mode for a computer on the computer details page or from options menu in the computers list. When you manually end containment mode:
- All IPs recorded and blocked on the computer are released
- The computer allows RDP connections
If WatchGuard Endpoint Security automatically ends containment mode, it does not release the IPs and continues to block them.
To end RDP Attack Containment mode on the computer details page:
- Select a computer from the list.
The computer details page opens. The notification box shows that the computer is in RDP Attack Containment mode. - To turn off the mode, click End RDP Attack Containment Mode.
To end RDP Attack Containment mode on the Computers list:
- Select Computers.
- On the My Organization tab, select the group that contains the computer you want to end RDP Attack Containment mode for.
- On the Computers page, in the row for a computer that is in RDP Attack Containment mode, click
 .
.
Windows computers in RDP Attack Containment mode have a red RDP icon next to the IP address.
icon next to the IP address. - From the options menu, select End RDP Attack Containment Mode.
The RDP icon flashes orange until WatchGuard Endpoint Security disables RDP Attack Containment mode.
Computer Containment Status
When you end RDP Attack Containment mode, WatchGuard Endpoint Security immediately sends the command to all recipient computers. When the device is accessible and has real-time communication enabled, the action is executed immediately.
If WatchGuard Endpoint Security is unable to contact the computer, the computer continues in containment mode. WatchGuard Endpoint Security sends the command again every 4 hours for the next 7 days. If the action is unable to complete, the Endpoint Security management UI shows the computer status in RDP Attack Containment mode.