Applies To: WatchGuard Advanced Reporting Tool and Data Control
WatchGuard Advanced EPDR, EPDR, and EDR (WatchGuard Endpoint Security) send data to the Advanced Visualization Tool, which organizes it into data tables that are easy to read.
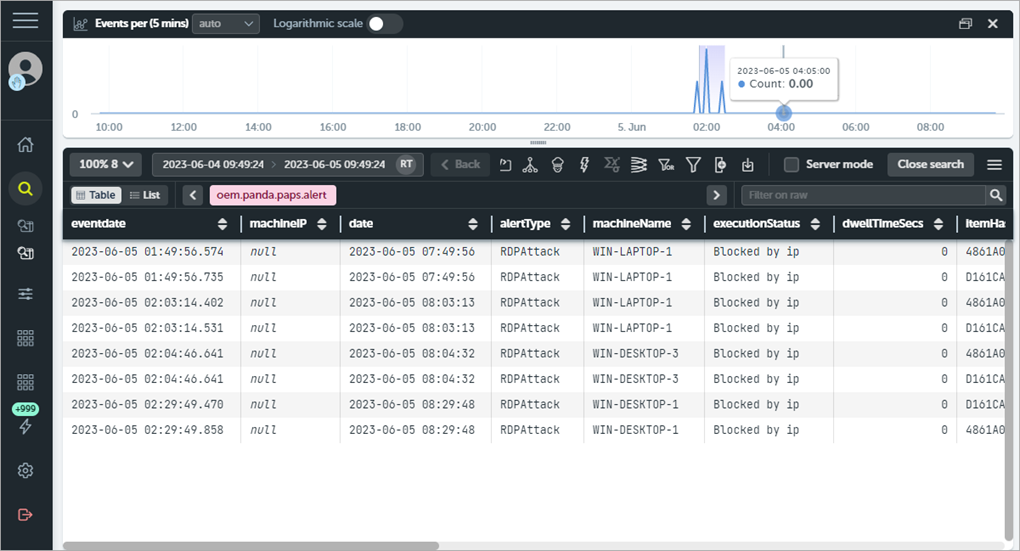
Each line of a data table is an event monitored by WatchGuard Endpoint Security. In the Advanced Visualization Tool you can search, browse, and analyze the information in your data tables.
- To see the list of available data tables, from the left pane, select Data Search.
The Subtype column shows the list of tables.
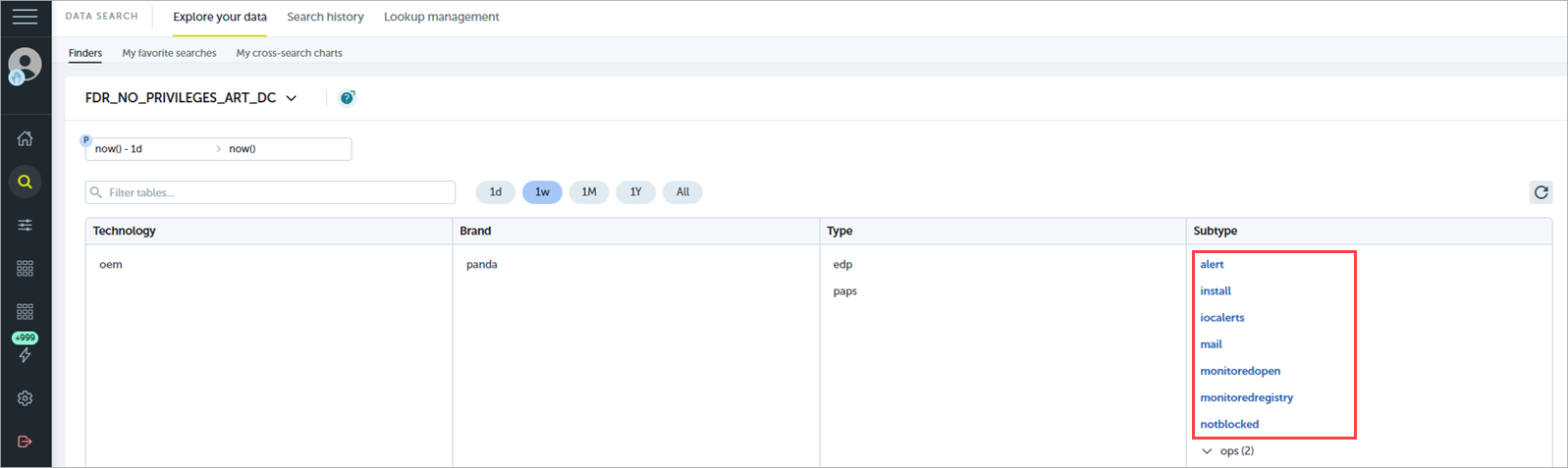
When you open a data table, a shortcut appears in the left pane below Data Search. Select the shortcut to quickly open the data table.
Finders group and organize the tags applied to data into four levels — Technology, Brand, Type, and Subtype.
Tables Specific to WatchGuard Advanced Reporting Tool Data
These data tables are available by default with the Subtype tag. For information on the fields in each data table, go to Advanced Reporting Tool — Data Fields.
alert
This data table includes information on incidents shown in the Activity tile on the WatchGuard Endpoint Security dashboard. It contains a line for each threat detected on the network with information such as the computer involved, type of incident, timestamp, and result.
You can use several fields in the Alerts table to extract valuable information on the attacks:
- Eventdate — Group by this field to see the number of daily attacks and determine if there is an ongoing attack.
- dwellTimeSecs — Provides the detection window of the threats received. This is the time from when the threat was first seen on the network to its classification.
- itemHash — Because the name of the threat varies across security vendors, you can use the hash field to group threats instead of the itemName. This also helps to distinguish malware that is labeled with the same name.
install
This data table logs information about the installation of the endpoint agent on computers
monitoredopen
This data table logs the data files accessed by applications that are not generally used to access that type of data file.
monitoredregistry
This data table logs every attempt to modify the registry as well as when software accesses the registry permissions, passwords, certificate stores, and similar information.
notblocked
This data table logs the items that WatchGuard Endpoint Security did not scan because of exceptional situations, such as service timeout on startup or configuration changes.
ops
This data table logs all operations performed by processes seen on the network.
processnetbytes
This data table logs the data usage of processes seen on the network. ART generates a log for each process approximately every four hours with the amount of data transferred since the last log was sent.
Use this table to see which programs on the network computers use the most data. This table does not differentiate between internal data and external data usage. The total amount of data a process uses might be a mixture of data requested over the Internet and data obtained from your internal servers (such as mail servers, Intranet web servers, files shared among workstations).
registry
This data table logs all operations performed on the registry branches used by malicious programs to become persistent and survive computer restarts.
This table logs when processes access the registry and affect branches that are read when the system starts during the operating system boot process. Malware modifies these branches to make sure it runs on every boot up.
Many registry branches allow a program to run at start up, but those most commonly used by Trojans and other types of threats are:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnceEx
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnceEx
socket
This data table logs all network connections established by the processes seen on the network.
toastblocked
This data table contains a record for each process blocked because WatchGuard Endpoint Security has not yet returned the relevant classification.
URLdownload
This data table contains information on HTTP downloads performed by processes seen on the network (such as URLs, downloaded file data, computers that downloaded data).
This table shows all downloads performed by users on the network, regardless of whether they are malware or goodware. You can filter by download information, and see a chart that shows the domains that receive most download requests.
vulnerableappsfound
This data table logs every vulnerable application found on each computer on the network. Unlike the Ops table, whose ocsExec, ocsName and ocsVer fields show the vulnerable applications that ran on the network, this table shows all vulnerable applications that reside on computers. WatchGuard Endpoint Security sends a daily log for each detected application. When WatchGuard Endpoint Security detects an application, the endpoint agent stops sending the relevant event.
Use this table to determine which computers on the network have most vulnerable applications.
Tables Specific to WatchGuard Data Control Data
When a process accesses files with Personally Identifiable Information (PII), the information is sent to the WatchGuard Data Control server, where it is organized into an easy-to-read table.
Each line of the table is an event monitored by Data Control, and provides information such as when the event occurred, the computer where it took place, its IP address, etc. For information on the fields in each data table, go to Data Control Visualization — Data Fields.
These data tables are available in the Advanced Visualization Tool by default with the Subtype tag:
ops
This data table stores all information related to the monitoring of files with PII.
usrrules
This data table stores all information collected from the files specified in rules defined by the administrator.
usrrulesmail
This data table stores all information collected from the email messages that contain files monitored as specified in the rules defined by the administrator.
This data table stores all information collected from the email messages that contain files classified as PII, as well as the characteristics of the files with personal data.