Applies To: Locally-managed Fireboxes
RADIUS Single Sign-On (RSSO) enables users to automatically authenticate to the Firebox when they use RADIUS to authenticate to a RADIUS client, such as a wireless access point. For information about how RADIUS SSO operates, and the requirements for RADIUS clients, go to About RADIUS Single Sign-On.
When you enable RADIUS SSO, the RADIUS-SSO-Users group and the Allow RADIUS SSO Users policy are automatically created to allow outbound connections from users authenticated through RADIUS SSO. You can use this group, or you can create new groups that match the user group names on your RADIUS server.
To allow RADIUS accounting traffic from the RADIUS server to the Firebox, the Allow RADIUS SSO Service policy is also automatically created .
For RADIUS SSO to operate, you must enable RADIUS accounting on the RADIUS client or access point.
Before You Begin
Before you enable RADIUS SSO on your Firebox, you must have this information:
- IP Address — The IP address of your RADIUS server
- Secret — Case-sensitive shared secret used to verify RADIUS messages between the RADIUS server and the Firebox
- Group Attribute — The RADIUS attribute number used to get group names from RADIUS accounting messages
Session Timeout and Idle Timeout
For RADIUS SSO, user sessions time out based on RADIUS SSO timeouts rather than the global authentication timeouts. The RADIUS SSO settings include two timeout values.
Session Timeout
The maximum length of time the user can send traffic to the external network. If you set this field to zero (0) seconds, minutes, hours, or days, the session does not expire and the user can stay connected for any length of time.
Idle Timeout
The maximum length of time the user can stay authenticated when idle (not passing any traffic to the external network). If you set this field to zero (0) seconds, minutes, hours, or days, the session does not time out when idle and the user can stay idle for any length of time.
If a user disconnects before these timeout limits are reached, the Firebox removes the session when it receives a RADIUS accounting STOP message that contains the user name and client IP address. For more information about RADIUS accounting messages, go to About RADIUS Single Sign-On.
Configure the RADIUS Server
To enable RADIUS SSO, you must configure the RADIUS server to forward RADIUS accounting packets to a Firebox IP address on port 1813, and you must configure the shared secret used for communication between the RADIUS server and the Firebox.
Configure the Firebox
When you enable and configure the settings for Single Sign-On (SSO) on your Firebox, you must specify the IP address of the RADIUS server. You can also specify the IP addresses (or ranges) to exclude from SSO.
- Select Authentication > Single Sign-On.
The Single Sign-On pages appear with the Active Directory tab selected. - Select the RADIUS tab.
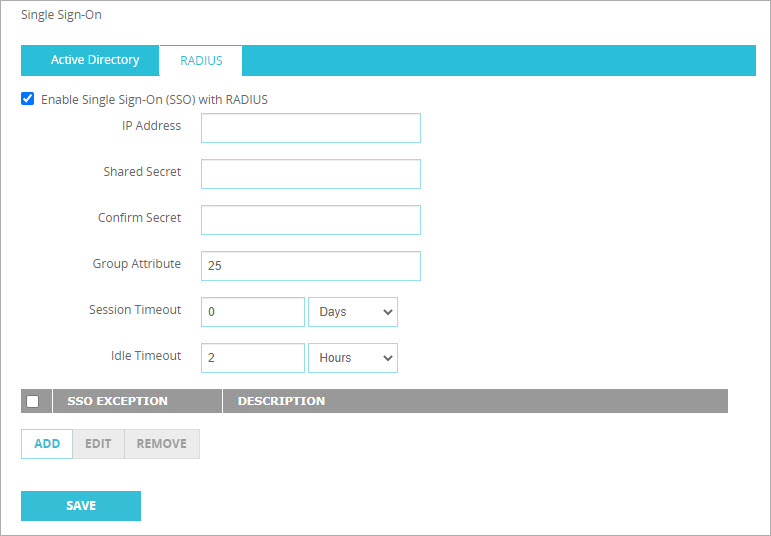
- Select the Enable Single Sign-On (SSO) with RADIUS check box.
- In the IP Address text box, type the IP address of your RADIUS server.
- In the Shared Secret text box, type the shared secret you configured on the RADIUS server.
The shared secret is case-sensitive and must be the same on the Firebox and the RADIUS server. - In the Confirm Secret text box, type the shared secret again.
- In the Group Attribute text box, specify the RADIUS attribute number that includes information about group membership.
We recommend that you use the Class attribute (25). This is the default value.The Filter-ID attribute (11) is not sent in RADIUS accounting packets.
- In the Session Timeout text box, type or select the maximum length of time the user can remain authenticated before the session times out.
- In the Idle Timeout text box, type or select the maximum length of time the user can be idle before the session times out.
- To specify which addresses cannot use RADIUS SSO, in the SSO Exceptions section, add or remove the IP addresses or ranges to exclude from RADIUS SSO.
For more information about RADIUS SSO exceptions, go to the Define SSO Exceptions section. - Click Save.
- Select Setup > Authentication > Single Sign-On.
The Single Sign-On dialog box appears with the Active Directory tab selected. - Select the RADIUS tab.
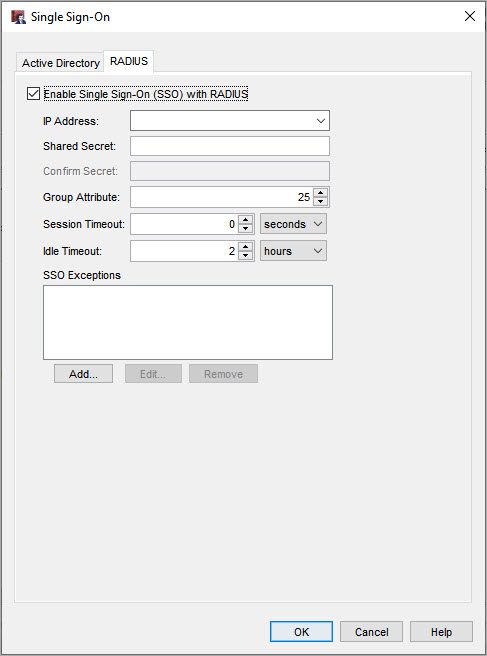
- Select the Enable Single Sign-On (SSO) with RADIUS check box.
- In the IP Address text box, type the IP address of your RADIUS server.
- In the Shared Secret text box, type the shared secret you configured on the RADIUS server.
The shared secret is case-sensitive and must be the same on the Firebox and the RADIUS server. - In the Confirm Secret text box, type the shared secret again.
- In the Group Attribute text box, specify the RADIUS attribute number that includes information about group membership.
In most cases, the Filter-ID attribute (11) is used for this purpose. This is the default value. - In the Session Timeout text box, type or select the maximum length of time the user can remain authenticated before the session times out.
- In the Idle Timeout text box, type or select the maximum length of time the user can be idle before the session times out.
- Click OK.
RADIUS SSO Policies and Groups
When you enable RADIUS SSO (RSSO), two policies are automatically added to your Firebox configuration:
- Allow RADIUS SSO Service — Allows RADIUS accounting traffic between the Firebox and the RADIUS server
- Allow RADIUS SSO Users — Allows outbound TCP and UDP traffic for RADIUS SSO authenticated users
RADIUS accounting messages include information about group membership for the authenticated user. The RADIUS-SSO-Users group on the Firebox automatically includes all users who are not a member of a group that exists on the Firebox. Outbound traffic for these users is allowed by the Allow RADIUS SSO Users policy.
If users who authenticate through RADIUS SSO are members of a group on the RADIUS server, you can create the same group on the Firebox, and then use that group name in policies. If a user authenticated through RADIUS SSO is a member of a group that exists on the Firebox, the user is not a member of the group RADIUS-SSO-Users, so you must create a policy to allow traffic for the user or group.
For more information, go to Use Users and Groups in Policies.
Define RADIUS SSO Exceptions
If you want to exclude certain devices from RADIUS SSO, you can add them to the RADIUS SSO Exceptions list. When the Firebox receives RADIUS accounting messages for a user with an IP address on the RADIUS SSO Exceptions list the Firebox does not create a Firewall authentication session for that user.
When you add an entry to the RADIUS SSO Exceptions list, you can choose to add a host IP address, network IP address, subnet,
- On the RADIUS tab, in the SSO Exceptions section, click Add.
The Add IP Addresses dialog box appears. - From the Choose Type drop-down list, select the type of entry to add to the SSO Exceptions list:
- Host IP
- Network IP
- Host Range
The text boxes that appear change based on the type you select.
- Type the IP address for the type you selected.
If you selected the type Host Range, in the From and To text boxes, type the start and end IP addresses for the range. - (Optional) In the Description text box, type a description to include with this exception in the SSO Exceptions list.
- Click OK.
The IP address or range appears in the SSO Exceptions list. - Click Save.
- In the SSO Exceptions section, click Add.
The Add SSO Exception dialog box appears.

- From the Choose Type drop-down list, select the type of entry to add to the SSO Exceptions list:
- Host IPv4
- Network IPv4
- Host Range IPv4
- Host Name (DNS lookup)

- In the Value text box, type the IP address for the type you selected.
If you selected the type Host Range, in the Value text box, type the IP address at the start of the range.
In the To text box, type the IP address at the end of the range. - (Optional) In the Description text box, type a description to include with this exception in the SSO Exceptions list.
The Comment text box does not appear for the Host Name type. - Click OK.
The IP address or range appears in the SSO Exceptions list.
You can also edit or remove entries from the SSO Exceptions list.
- From the SSO Exceptions list, select an entry.
- Click Edit.
The Edit SSO exception IP dialog box appears. - Change the settings for the SSO exception.
- Click OK.
The updated entry appears in the SSO Exceptions list.

- Click OK.
- From the SSO Exceptions list, select an entry.
- Click Remove.
The selected entry is removed from the SSO Exceptions list. - Click Save.
- From the SSO Exceptions list, select an entry.
- Click Remove.
The selected entry is removed from the SSO Exceptions list. - Click OK.
Use Authentication to Restrict Incoming Connections
Configure RADIUS Server Authentication with Active Directory for Wireless Users