Configure SAML Single Sign-On
You can enable Security Assertion Markup Language (SAML) single sign-on (SSO) to authenticate users with your Firebox. With SAML, you can exchange data between an Identity Provider (IdP) and a Service Provider (SP). In the SAML configuration on the Firebox, you can configure the Firebox as the SP.
To configure SSO for Firebox users:
- Configure the SAML service provider settings on your Firebox.
- Connect to the configuration instructions page hosted on your Firebox.
- Give the SAML information on the configuration instructions page to your IdP administrator.
- In your account on the IdP website, the IdP administrator must configure the Firebox as an SP.
- On the Firebox, configure the SAML IdP settings.
Your Identity Provider must meet the WatchGuard requirements for SAML 2.0 communication. For more information about SAML requirements, go to SAML Requirements for Identity Providers.
Configure the SAML Service Provider Settings on the Firebox
In the SAML configuration on the Firebox, you configure the Firebox as the SP and a third-party service as the IdP.
You can configure SSO and SAML to authenticate with:
- Access Portal
- Authentication Portal
- Mobile VPN with SSL client
Fireware v12.11 expands support for SAML authentication and now includes Firebox authentication. The Mobile VPN with SSL v12.11 client for Windows supports SAML authentication. Because SAML authentication for Mobile VPN with SSL requires a client update that supports integration with an embedded web browser that can interact with an IdP, lower versions of the Mobile VPN with SSL for Windows client, all versions of the Mobile VPN with SSL for macOS client, and third-party OpenVPN clients are not supported.
SAML authentication is disabled by default.
When you configure a SAML authentication user or group in a firewall policy but then enable SAML authentication for Mobile VPN with SSL or Access Portal, or when you configure a SAML authentication user or group in a firewall policy and Mobile VPN with SSL or Access Portal but later disable SAML authentication for Mobile VPN with SSL or Access Portal, the SP metadata changes and SAML authentication no longer works. You must provide the updated SP metadata to your IdP administrator.
To configure the SAML service provider settings on your Firebox, from Fireware Web UI:
- Select Authentication > Servers.
- Select SAML.
The SAML settings page opens. - Select Enable SAML.
- In the IdP Name text box, type the name of your IdP.
This name appears on the login pages as the authentication server name. - In the Host Name text box, type an FQDN that resolves to the Firebox external interface.
- Keep the IdP Metadata URL text box blank for now. You must complete the steps in the next sections before you can get the IdP Metadata URL from your IdP administrator.

- Click Save.
You can configure SSO and SAML to authenticate with:
- Access Portal
- Authentication Portal
- Mobile VPN with SSL client
Fireware v12.11 expands support for SAML authentication and now includes Firebox authentication. The Mobile VPN with SSL v12.11 client for Windows supports SAML authentication. Because SAML authentication for Mobile VPN with SSL requires a client update that supports integration with an embedded web browser that can interact with an IdP, lower versions of the Mobile VPN with SSL for Windows client, all versions of the Mobile VPN with SSL for macOS client, and third-party OpenVPN clients are not supported.
SAML authentication is disabled by default.
When you configure a SAML authentication user or group in a firewall policy but then enable SAML authentication for Mobile VPN with SSL or Access Portal, or when you configure a SAML authentication user or group in a firewall policy and Mobile VPN with SSL or Access Portal but later disable SAML authentication for Mobile VPN with SSL or Access Portal, the SP metadata changes and SAML authentication no longer works. You must provide the updated SP metadata to your IdP administrator.
To configure the SAML service provider settings on your Firebox, from Policy Manager:
- Select Setup > Authentication > Authentication Servers.
- Select the SAML tab.
- Select Enable SAML.
- In the IdP Name text box, type the name of your IdP.
This name appears on the Firebox login pages as the authentication server name. - In the Host Name text box, type an FQDN that resolves to the Firebox external interface.
- Keep the IdP Metadata URL text box blank for now. You must complete the steps in the next sections before you can get the IdP Metadata URL from your IdP administrator.

- Click OK.
You can configure SSO and SAML to authenticate Access Portal users. SAML authentication is disabled by default.
To configure the SAML service provider settings on your Firebox, from Fireware Web UI:
- Select Subscription Services > Access Portal.
- Select the SAML tab.
If your Firebox has Fireware v12.1 or v12.1.1, select Subscription Services > Access Portal > User Connections Settings > Configure. - Select Enable SAML.
- In the IdP Name text box, type the name of your IdP.
This name appears on the login pages as the authentication server name. - In the Host Name text box, type an FQDN that resolves to the Firebox external interface.
- Keep the IdP Metadata URLtext box blank for now. You must complete the steps in the next sections before you can get the IdP Metadata URL from your IdP administrator.

- Click Save.
You can configure SSO and SAML to authenticate Access Portal users. SAML authentication is disabled by default.
To configure the SAML service provider settings on your Firebox, from Policy Manager:
- Select Subscription Services > Access Portal.
- Select the SAML tab.
If your Firebox has Fireware v12.1 or v12.1.1, select Subscription Services > Access Portal > User Connections Settings > Configure. - Select Enable SAML.
- In the IdP Name text box, type the name of your IdP.
This name appears on the Firebox login pages as the authentication server name. - In the Host Name text box, type an FQDN that resolves to the Firebox external interface.
- Keep the IdP Metadata URL text box blank for now. You must complete the steps in the next sections before you can get the IdP Metadata URL from your IdP administrator.

- Click OK.
Next, you must connect to the Configuration Instructions Page hosted by the Firebox.
Connect to the Configuration Instructions Page
After you save the SAML configuration, the Firebox automatically generates a web page that includes additional SAML configuration information. You must give this information to your IdP administrator so the administrator can configure the account settings for your company on the IdP website.
To connect to the configuration instructions page:
- Go to https://[Host name or IP address for Firebox SAML]/auth/saml.
The configuration instructions page appears.
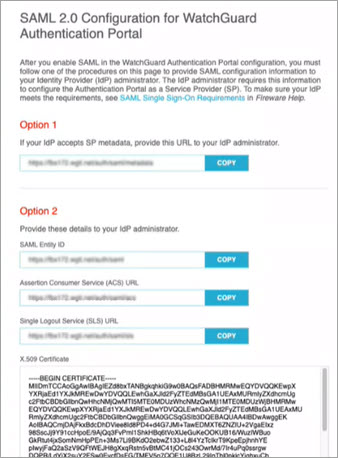
- Follow the instructions for either Option 1 or 2.
Option 1 — Automatic Configuration
If your IdP accepts SAML metadata from SPs, give the URL in the Option 1 section to your IdP Administrator.
Option 2 — Manual Configuration
If your IdP does not accept SAML metadata from SPs, give the URLs and certificate in the Option 2 section to your IdP Administrator.
Next, your IdP administrator must input the metadata URL from Option 1, or the URLs and certificate from Option 2, to the account settings for your company on the IdP website. The IdP administrator must also give you the IdP Metadata URL. For information about IdP configuration, see the documentation for your Identity Provider.
To complete the SAML setup, you must configure the Identity Provider settings on your Firebox.
Configure the SAML Identity Provider Settings on Your Firebox
In the SAML configuration on the Firebox, you must now configure the SAML configuration settings for your third-party IdP.
- Select Authentication > Servers.
- Select the SAML tab.
The SAML settings page opens. - Select Enable SAML.
- In the IdP Metadata URL text box, type the metadata URL provided by your IdP.
- (Optional) To change the Group Attribute Name, click Edit and type the Group Attribute Name. Tip!
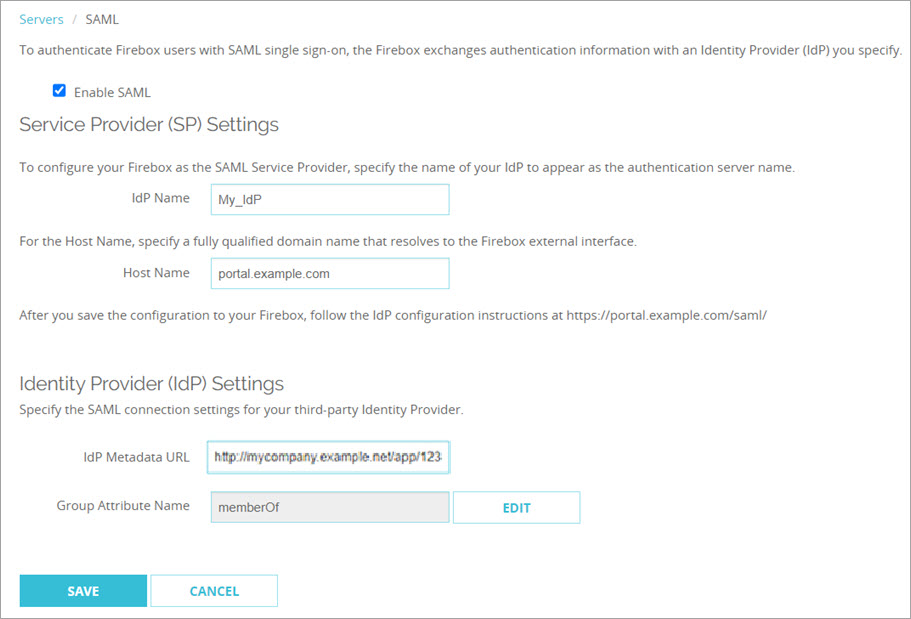
- Click Save.
- Select Setup > Authentication > Authentication Servers.
- Select the SAML tab.
- Select Enable SAML.
- In the IdP Metadata URL text box, type the metadata URL provided by your IdP.
- (Optional) To change the Group Attribute Name, click Edit and type the Group Attribute Name. Tip!
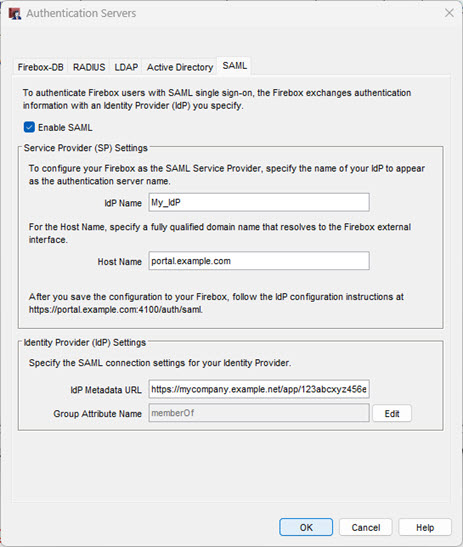
- Click OK.
- Select Subscription Services > Access Portal.
- Select the SAML tab.
If your Firebox has Fireware v12.1 or v12.1.1, select Subscription Services > Access Portal > User Connections Settings > Configure. - Select Enable SAML.
- In the IdP Metadata URL text box, type the metadata URL provided by your IdP.
- (Optional) To change the Group Attribute Name, click Edit and type the Group Attribute Name. Tip!
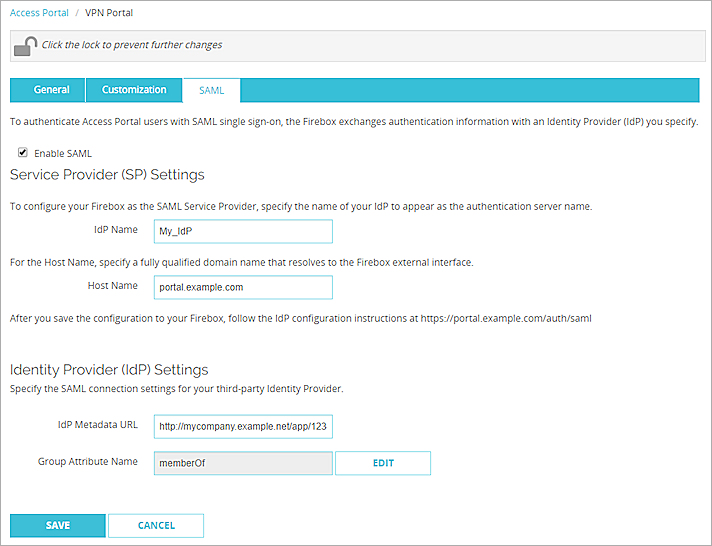
- Click Save.
- Select Subscription Services > Access Portal.
- Select the SAML tab.
If your Firebox has Fireware v12.1 or v12.1.1, select Subscription Services > Access Portal > User Connections Settings > Configure. - Select Enable SAML.
- In the IdP Metadata URL text box, type the metadata URL provided by your IdP.
- (Optional) To change the Group Attribute Name, click Edit and type the Group Attribute Name. Tip!

- Click OK.
View Log Messages for SAML Authentication
In Fireware v12.11 and higher, you can use the SAML authentication diagnostic log messages to troubleshoot problems with SAML authentication for users. SAML log messages use the samld identifier.
For example:
2024-08-15 16:26:43 samld ACS: user [email protected] from sslvpn_client logged in
For information about diagnostic logs and how to view them, go to Traffic Monitor.