Configure IPSec VPN Phase 1 Settings
A Phase 1 transform is a set of security protocols and algorithms used to protect VPN data. During IKE negotiation, the peers must agree on the transform to use. You can define a tunnel so that it offers a peer more than one transform for negotiation. For more information, go to Add a Phase 1 Transform.
When you use IKEv2, the NAT traversal and Phase 1 transforms are shared by all BOVPN gateways and BOVPN virtual interfaces that use IKEv2 and have a remote gateway with a dynamic IP address. For more information about IKEv2 shared settings, go to Configure IKEv2 Shared Settings.
Edit Phase 1 Settings
The available Phase 1 settings are the same for a BOVPN gateway or a BOVPN virtual interface.
- For a BOVPN gateway, you configure Phase 1 settings in the gateway settings.
- For a BOVPN virtual interface, you configure Phase 1 settings in the BOVPN virtual interface settings.
Configure Phase 1 Settings For IKEv1
For a branch office VPN that uses IKEv1, the Phase 1 exchange can use Main Mode or Aggressive Mode. The mode determines the type and number of message exchanges that occur in this phase.
In the IKEv1 Phase 1 settings, you can select one of these modes:
Main Mode
In Fireware v12.10 and higher, Fireware supports Diffie-Hellman Group 21.
This mode is more secure, and uses three separate message exchanges for a total of six messages. The first two messages negotiate policy, the next two exchange Diffie-Hellman data, and the last two authenticate the Diffie-Hellman exchange. Main Mode supports Diffie-Hellman groups 1, 2, 5, 14, 15, 19, 20, and 21. This mode also allows you to use multiple transforms, as described in Add a Phase 1 Transform.
Aggressive Mode
This mode is faster because it uses only three messages, to exchange data and identify the two VPN endpoints. The identification of the VPN endpoints makes Aggressive Mode less secure.
When you use Aggressive mode, the number of exchanges between two endpoints is fewer than it would be if you used Main Mode, and the exchange relies mainly on the ID types used in the exchange by both appliances. Aggressive Mode does not ensure the identity of the peer. Main Mode ensures the identity of both peers, but can only be used if both sides have a static IP address. If your device has a dynamic IP address, you should use Aggressive mode for Phase 1.
Main fallback to aggressive
The Firebox attempts Phase 1 exchange with Main Mode. If the negotiation fails, it uses Aggressive Mode.
In the IKEv1 settings, you can enable Dead Peer Detection or IKE Keep-alive so that the Firebox detects when a tunnel has disconnected and automatically starts a new Phase 1 negotiation. Dead Peer Detection is an industry standard that is used by most IPSec devices. We recommend that you select Dead Peer Detection if both endpoint devices support it.
- Do not enable both IKE Keep-alive and Dead Peer Detection
- IKE Keep-alive is used only by Fireboxes. Do not enable it if the peer is a third-party IPSec gateway endpoint.
- If you configure VPN failover, you must enable Dead Peer Detection. For more information about VPN failover, go to Configure Branch Office VPN (BOVPN) Failover.
For information about how these settings affect the availability of your VPN tunnels, go to Improve BOVPN Tunnel Availability, Security, and Performance.
- Edit the BOVPN gateway or BOVPN Virtual Interface.
- Select the Phase 1 Settings tab.
- From the Version drop-down list, select IKEv1.
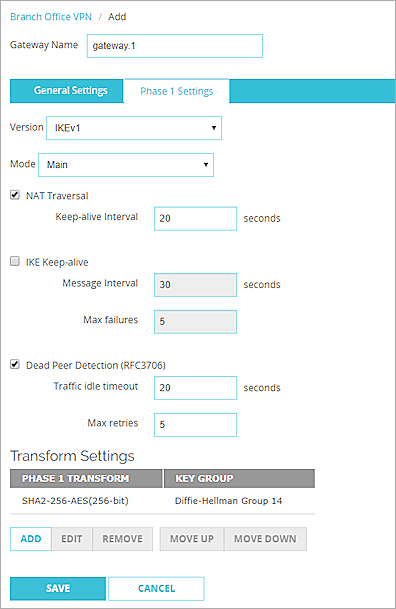
- From the Mode drop-down list, select Main, Aggressive, or Main fallback to Aggressive.
- If you want to build a BOVPN tunnel between the Firebox and another device that is behind a NAT device, select the NAT Traversal check box. NAT Traversal, or UDP Encapsulation, enables traffic to get to the correct destinations.
- In the Keep-alive Interval text box, type or select the number of seconds that pass before the next NAT keep-alive message is sent.
- To have the Firebox send messages to the IKE peer to keep the VPN tunnel open, select the IKE Keep-alive check box.
- In the Message Interval text box, type or select the number of seconds that pass before the next IKE Keep-alive message is sent.
- To set the maximum number of times the Firebox tries to send an IKE keep-alive message before it tries to negotiate Phase 1 again, type the number you want in the Max failures text box.
- Use the Dead Peer Detection check box to enable or disable traffic-based dead peer detection. When you enable dead peer detection, the Firebox connects to a peer only if no traffic is received from the peer for a specified length of time and a packet is waiting to be sent to the peer. This method is more scalable than IKE keep-alive messages.
- In the Traffic idle timeout text box, type or select the amount of time (in seconds) that passes before the Firebox tries to connect to the peer.
- In the Max retries text box, type or select the number of times the Firebox tries to connect before the peer is declared dead.
- The Firebox contains one default transform set, which appears in the Transform Settings list. This transform specifies SHA2 authentication, AES (256-bit) encryption, and Diffie-Hellman Group 14.
You can:- Use the default transform.
- Remove the default transform and replace it with a new one.
- Add an additional transform, as explained in Add a Phase 1 Transform.
- Edit the BOVPN gateway or BOVPN Virtual Interface.
- Select the Phase 1 Settings tab.
- From the Version drop-down list, select IKEv1.
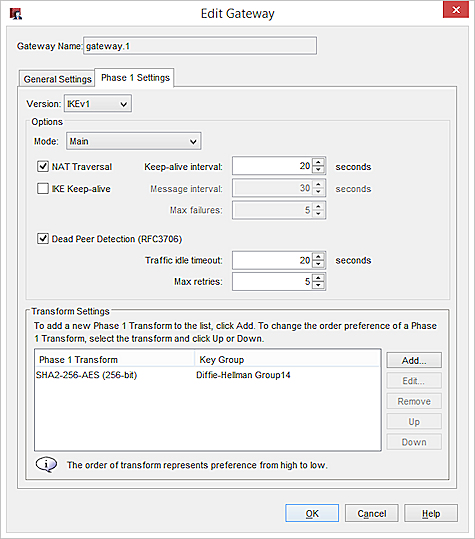
- From the Mode drop-down list, select Main, Aggressive, or Main fallback to Aggressive.
- If you want to build a BOVPN tunnel between the Firebox and another device that is behind a NAT device, select the NAT Traversal check box. NAT Traversal, or UDP Encapsulation, enables traffic to get to the correct destinations.
- In the Keep-alive Interval text box, type or select the number of seconds that pass before the next NAT keep-alive message is sent.
- To have the Firebox send messages to the IKE peer to keep the VPN tunnel open, select the IKE Keep-alive check box.
- In the Message Interval text box, type or select the number of seconds that pass before the next IKE Keep-alive message is sent.
- To set the maximum number of times the Firebox tries to send an IKE keep-alive message before it tries to negotiate Phase 1 again, type the number you want in the Max failures text box.
- Use the Dead Peer Detection check box to enable or disable traffic-based dead peer detection. When you enable dead peer detection, the Firebox connects to a peer only if no traffic is received from the peer for a specified length of time and a packet is waiting to be sent to the peer. This method is more scalable than IKE keep-alive messages.
- In the Traffic idle timeout text box, type or select the amount of time (in seconds) that passes before the Firebox tries to connect to the peer.
- In the Max retries text box, type or select the number of times the Firebox tries to connect before the peer is declared dead.
- The Firebox contains one default transform set, which appears in the Transform Settings list. This transform specifies SHA2 authentication, AES (256-bit) encryption, and Diffie-Hellman Group 14.
You can:- Use the default transform.
- Remove the default transform and replace it with a new one.
- Add an additional transform, as explained in Add a Phase 1 Transform.
Configure Phase 1 Settings For IKEv2
The IKEv2 protocol is different from IKEv1. Here is a summary of the differences between IKEv1 and IKEv2 settings on the Firebox:
- IKEv2 does not have multiple modes.
- IKEv2 does not support the IKE Keep-alive setting.
- NAT Traversal is always enabled.
- Dead Peer Detection (DPD) is always enabled.
- Dead Peer Detection can be Traffic-Based or Timer-Based, as described in IETF RFC 3706.
- Traffic-Based DPD — the Firebox sends a DPD message to the remote gateway only if no traffic is received from the remote gateway for a specified length of time and a packet is waiting to be sent to the remote gateway.
- Timer-Based DPD — the Firebox initiates a DPD exchange with the remote gateway at a specified message interval, regardless of any other traffic received from the remote gateway.
- IKEv2 uses shared Phase 1 settings for all BOVPN gateways that have a peer with a dynamic IP address.
- From the Version drop-down list, select IKEv2.
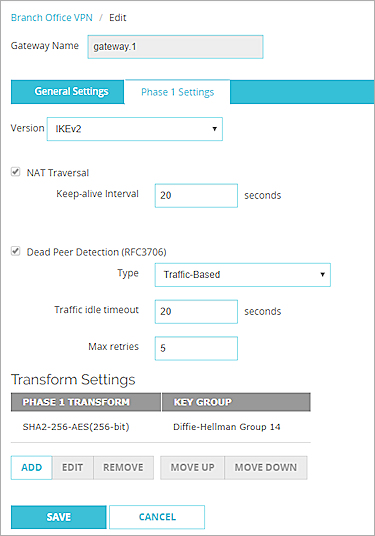
In Fireware Web UI, if the gateway has a peer with a dynamic IP address, the gateway uses shared IKEv2 settings and the NAT Traversal and Transform Settings are not visible in the gateway configuration . After you add the gateway, you can select VPN > IKEv2 Shared Settings to see and edit these shared settings.

- For a gateway that does not use IKEv2 shared settings, to change the NAT Traversal keep-alive interval, in the Keep-alive Interval text box, type or select the number of seconds between NAT keep-alive messages sent by the Firebox.
- In the Dead Peer Detection settings, from the Type drop-down list, select Traffic-Based or Timer-Based.
- Configure the DPD settings. The recommended settings are selected by default.
For Traffic-Based DPD:
- In the Traffic idle timeout text box, specify the amount of time (in seconds) that passes without receiving traffic from the peer before the Firebox sends a DPD message to the peer.
- In the Max retries text box, specify the number of times the Firebox tries to resend the DPD request message before it considers the peer dead.
For Timer-Based DPD:
- In the Message Interval text box, specify the number of seconds between DPD messages the Firebox sends to the peer.
- In the Max failures text box, specify the number of times the peer can fail to respond before the Firebox considers the peer dead.
In Fireware Web UI, if the gateway has a peer with a dynamic IP address, the gateway uses shared IKEv2 settings and the NAT Traversal and Transform Settings do not appear in the gateway configuration . After you add the gateway, you can select VPN > IKEv2 Shared Settings to see and edit these shared settings. For more information, go to Configure IKEv2 Shared Settings.
- For a gateway that does not use IKEv2 shared settings, you can edit the transform settings in the gateway configuration. The Firebox contains one default transform set, which appears in the Transform Settings list. This transform specifies SHA2 authentication, AES (256-bit) encryption, and Diffie-Hellman Group 14.
You can:- Use the default transform.
- Remove the default transform and replace it with a new one.
- Add an additional transform, as explained in Add a Phase 1 Transform.
- From the Version drop-down list, select IKEv2.
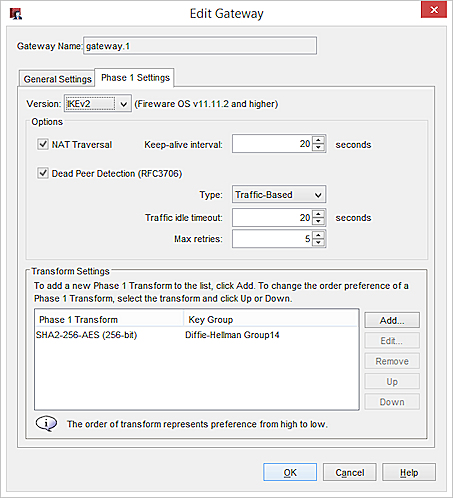
If a remote gateway peer has a dynamic IP address, some of the IKEv2 settings are shared. Settings that are not shared appear in the Gateway Settings tab. Shared settings appear in the Shared Settings tab.
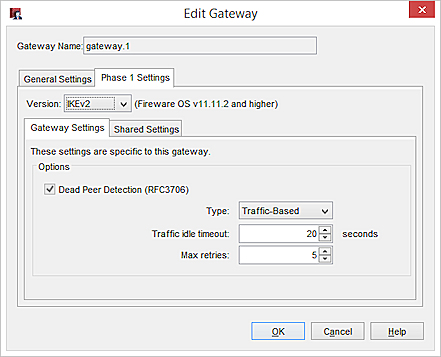
- In the Dead Peer Detection settings, from the Type drop-down list, select Traffic-Based or Timer-Based.
- Configure the DPD settings. The recommended settings are selected by default.
For Traffic-Based DPD:
- In the Traffic idle timeout text box, specify the amount of time (in seconds) that passes without receiving traffic from the peer before the Firebox sends a DPD message to the peer.
- In the Max retries text box, specify the number of times the Firebox tries to resend the DPD request message before it considers the peer dead.
For Timer-Based DPD:
- In the Message Interval text box, specify the number of seconds between DPD messages the Firebox sends to the peer.
- In the Max failures text box, specify the number of times the peer can fail to respond before the Firebox considers the peer dead.
- If the gateway uses shared settings, select the Shared Settings tab.
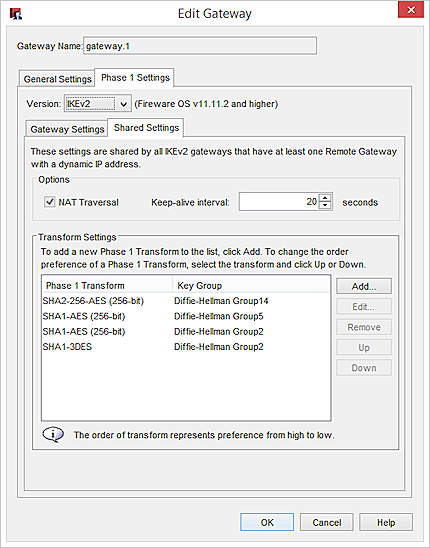
- To change the NAT Traversal keep-alive interval, in the Keep-alive Interval text box, type or select the number of seconds between NAT keep-alive messages sent by the Firebox.
- The Firebox contains one default transform set, which appears in the Transform Settings list. This transform specifies SHA2 authentication, AES (256-bit) encryption, and Diffie-Hellman Group 14.
You can:- Use the default transform.
- Remove the default transform and replace it with a new one.
- Add an additional transform, as explained in Add a Phase 1 Transform.
Any changes to the shared IKEv2 NAT Traversal and Phase 1 transform settings apply to all gateways that have a remote peer with a dynamic IP address. For more information about IKEv2 shared settings, go to Configure IKEv2 Shared Settings.