About Management Tunnels
Management Tunnels enable you to make a management connection to your remote Fireboxes that are behind a third-party NAT gateway device, so you can centrally manage your remote Fireboxes. This is helpful when you do not control the third-party NAT gateway device that your managed Fireboxes are behind, particularly if connections to your remote Fireboxes are blocked at the NAT gateway.
When your remote Fireboxes are behind a third-party NAT gateway, your remote devices can initiate outbound management and IPSec or SSL connections to your Management Server through the NAT gateway device and your gateway Firebox, but for your Management Server to be able to make inbound connections to manage your remote devices, you must configure a Management Tunnel. Your Management Server receives the connection from the remote device, and can then send information and updates back through the Management Tunnel to your remote devices.
You can choose from two Management Tunnel options:
- Management Tunnel over SSL
For a Management Tunnel over SSL, the Management Tunnel transmits data through an SSL encrypted tunnel and uses the same OpenVPN server that your Mobile VPN with SSL VPN tunnels use.
For more information, go to Management Tunnel over SSL Resources.
- Management Tunnel over IPSec
If you create a Management Tunnel over IPSec, your gateway Firebox and remote Fireboxes transmit data through the IPSec encrypted tunnel.
For more information, go to Management Tunnel over IPSec Resources.
Mobile VPN with SSL — Manually Configure the Firebox for Mobile VPN with SSL
Access Portal — About the Access Portal
Branch Office VPN over TLS — About Branch Office VPN over TLS
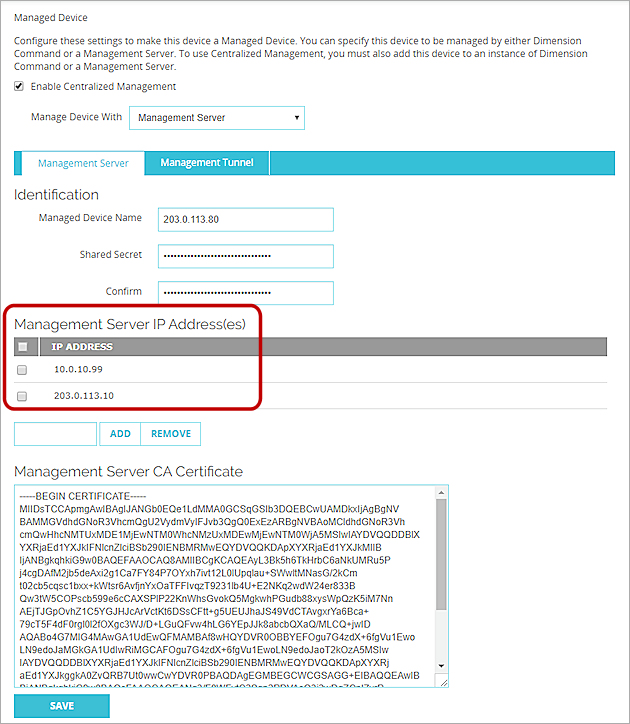
About Management Tunnel Configuration
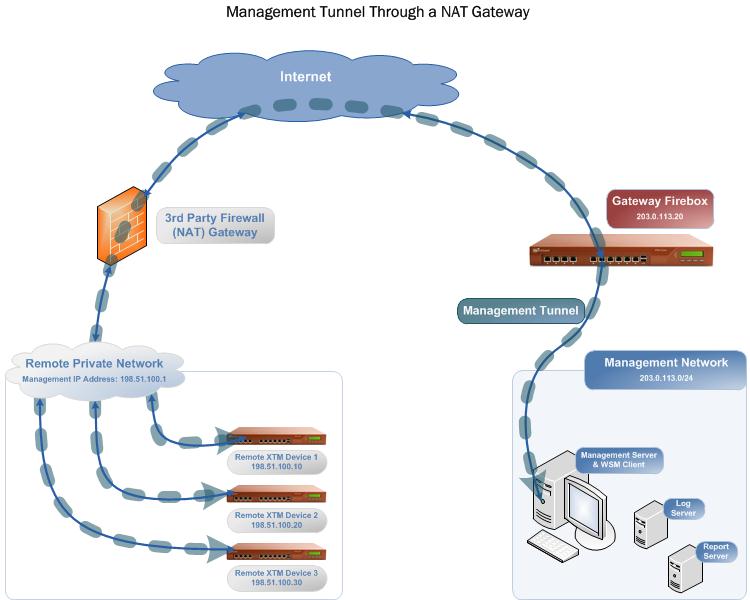
This diagram shows one example of a Management Tunnel configuration. The gateway Firebox is between the WatchGuard management network, which includes the WatchGuard Management Server, Log Server, Report Server, and the Internet. The remote Fireboxes in the remote private network are behind a third-party firewall (the NAT gateway device). The remote private network and the management IP address for the remote devices are on a different network from the gateway Firebox and the management network.
Requirements for Management Tunnels
Before you configure a Management Tunnel, you must make sure that your Fireboxes and network configurations meet these requirements:
- Management Network
- The WSM client and Management Server are installed
- (Optional) WatchGuard Dimension instance is installed, or WSM Log Server and Report Server are installed
To collect log messages from the Management Tunnel devices, you must install and configure at least one WatchGuard logging and reporting solution. - The Management Server is behind your gateway Firebox
- The subnet you select for the management network (the management IP address pool and virtual IP address pool) is large enough to accommodate the necessary connections
Because both the remote Fireboxes and the Mobile VPN with SSL clients get IP addresses from this pool, you must make sure that the subnet is large enough to accommodate all of these device connections, without an overlap in any IP addresses for any of the client devices or the gateway Firebox.
- Gateway Firebox
- Configured with static NAT policies to allow inbound traffic to the Management Server and Log Server over ports 4112, 4113, and 4115
These policies are automatically generated by the Management Server. - Includes a VPN resource for the management network
You configure this in WSM through the Management Server. - Includes a policy to allow traffic through the OpenVPN server over TCP port 443
The WatchGuard SSLVPN policy is automatically added by the Management Server when you add a Management Tunnel over SSL. - The Firebox-DB authentication server is enabled and configured
- Configured with static NAT policies to allow inbound traffic to the Management Server and Log Server over ports 4112, 4113, and 4115
- Third-party Firewall NAT Gateway
- Must allow outbound IPSec connections for a Management Tunnel over IPSec
- Must allow outbound connections over port 443 for a Management Tunnel over SSL
- Remote Fireboxes
- For a Management Tunnel over IPSec, Fireboxes are configured in Mixed Routing Mode
- For a Management Tunnel over SSL, Fireboxes can be configured in Mixed Routing Mode, Transparent Bridge Mode, or Drop-In Mode
- Each remote Firebox is added to management as a dynamic device (the external interface on the Firebox can have a static, DHCP, or PPPoE IP address)
- Trusted interfaces on all remote Fireboxes can either be the same IP addresses or be unique IP addresses
- Includes a policy to allow traffic over TCP port 443
The WatchGuard SSLVPN policy is automatically added by the Management Server when you add a Management Tunnel over SSL. - Fireboxes must be under management, but can be in Basic Managed Mode or Fully Managed Mode
For more information about the ports required for WatchGuard services, go to Install WatchGuard Servers on Computers with Desktop Firewalls.
About VPN Resources
When you add a Firebox to the Management Server, the Management Server automatically creates these default VPN resources for the Firebox:
- A Hub Network resource
- A Interface Network for each configured interface on the Firebox that is not an External interface (for example, Trusted Network or Optional Network)
When you configure a Management Tunnel, you select which VPN resources to use for the traffic through the tunnel. The VPN resource you select specifies which network interface on the remote device sends traffic through the tunnel. You can select any of the default VPN resources, or you can add other VPN resources. Before you select a VPN resource, it is important to understand how the VPN resource you select affects the traffic through the Management Tunnel.
Hub Network
If you configure your Management Tunnel gateway Firebox to use the Hub Network resource, in addition to management traffic, your remote devices send all Internet traffic through the Management Tunnel. This can decrease Internet connection speed and might reduce tunnel performance.
Trusted Network
If you configure your Management Tunnel gateway Firebox to use the Trusted Network resource, your remote devices only send traffic from their Trusted network interfaces through the Management tunnel.
Optional Network
If you configure your Management Tunnel gateway Firebox to use the Optional Network resource, your remote devices will only send traffic from their Optional network interfaces through the Management tunnel.
Select a Management Tunnel Type
Before you can select the type of Management Tunnel to configure, you must consider all of the resources that each tunnel type uses.
Management Tunnel over SSL Resources
Each Management Tunnel over SSL uses one of your Mobile VPN with SSL client licenses, and shares the same OpenVPN server with the Branch Office VPN over TLS in Server Mode, Mobile VPN with SSL, and Access Portal features. Because Management Tunnels over SSL use port 443, which is typically open on most third-party devices, a Management Tunnel over SSL is less likely to be blocked by the third-party NAT gateway device.
When you enable a Management Tunnel over SSL, the Management Server locks the settings shared by the Branch Office VPN over TLS in Server Mode, Mobile VPN with SSL, and Access Portal features, so they cannot be modified. These settings include:
- The port number (443)
- OpenVPN Server IP address (the IP address of your Management Tunnel hub device)
- Management IP address pool (this is the Virtual IP address pool in the Mobile VPN with SSL tunnel settings)
Because Management Tunnels over SSL use the same OpenVPN server that the Branch Office VPN over TLS in Server Mode, Mobile VPN with SSL, and Access Portal features on your Firebox also use, your Management Tunnel shares the same IP address pool with these features. This means that you must make sure that the IP address pool is large enough to accommodate all the necessary connections. You must also make sure to use the same network address when you specify the Management IP Address Pool setting in the Management Tunnel settings for the gateway Firebox that is specified in the Virtual IP Address Pool settings in the other features.
The Management Tunnel over SSL and Mobile VPN with SSL clients also share a license, so the gateway Firebox and each remote client device use one of the allowed connections in your license. Make sure your license can accommodate all of the connections necessary for your Management Tunnel.
When you add a Management Tunnel over SSL, the virtual IP address pool and server details are updated, and your Mobile VPN with SSL tunnels that use the same OpenVPN server as your Management Tunnels restart.
For more information about Mobile VPN with SSL, go to Manually Configure the Firebox for Mobile VPN with SSL.
Before you create a Management Tunnel over SSL, make sure that the private IP address for your Management Server is the first IP address included in the Distribution IP Address list for the Management Server and in the Managed Device settings for the remote (spoke) devices. This enables the tunnel to be rebuilt successfully after it has been interrupted.

The private IP address is the first IP address in the Management Server Distribution IP Address list
If you update the client settings for a managed device at either end of the Management Tunnel over SSL to expire the lease or reset the Management Server configuration, and the private IP address is not the first IP address included in the Distribution IP Address list and the Managed Device Settings dialog box, the private IP address is replaced in the tunnel configuration with the public IP address of the Management Server, and the Management Tunnel over SSL no longer functions.
For more information about how to add the private IP address of the Management Server to the Distribution IP Address list, go to Configure the Certificate Authority on the Management Server.
For more information about how to add the private IP address of the Management Server to the Management Server IP Address(es) list in the Managed Device Settings, see Configure a Firebox as a Managed Device.
Management Tunnel over IPSec Resources
A Management Tunnel over IPSec tunnel uses your Mobile VPN with IPSec license, and each remote device at the end of a Management Tunnel uses one available tunnel route in your license.
Because a Management Tunnel over IPSec does not share any resources with your Mobile VPN with IPSec configuration, you have more flexibility in your Mobile VPN with SSL configuration if you use a Management Tunnel over IPSec.
When you have active Management Tunnels over IPSec:
- Each remote device in a Management Tunnel uses one tunnel route.
- The remote Firebox management IP address is used to establish the tunnel and connect to the device. This IP address is used as the 1-to-1 NAT address for the Management Tunnel.
- The gateway Firebox uses one tunnel route for each remote device at the end of a Management Tunnel.
Managed Branch Office VPN Tunnels (WSM)
Make Managed Tunnels Between Devices