The logging and notification preferences are similar throughout the Firebox configuration. Logging and notification preferences control when and what types of log message the Firebox generates when an event occurs.
You can configure logging and notification settings in many locations in the Firebox configuration. For example:
- Firewall policies and proxies — Alarm notification for policy and proxy events
- Firebox feature key — Alarm notification when a feature key is expired or expires soon
- Default Packet Handling — Logging and alarm notification for specific types of attacks and events
- Blocked Sites and Blocked Ports — Logging and alarm notification for blocked site and blocked port events
- Intrusion Prevention — Alarm notification when IPS generates an alarm
- BOVPN — Alarm notification for BOVPN events
- Multi-WAN — Alarm notification for multi-WAN events
- FireCluster — Alarm notification for FireCluster events
Most of the options described in this topic are available in each location where you can define logging and notification preferences.
Logging and Notification Settings
The logging and notification settings you can configure are:
For a packet filter or proxy policy, this check box appears in the Logging settings.
When you select this check box, the Firebox sends a log message at the start of each connection that matches the configuration in the policy. You can review these log messages in Traffic Monitor, WebCenter, Dimension, and WatchGuard Cloud.
If you do not have to actively monitor allowed connections in the log file, we recommend you do not select Send a Log Message for policies that allow traffic. This increases CPU load on the Firebox and reduces log storage in Dimension.
For more information about reviewing logs in these tools, go to:
- Device Log Messages (Traffic Monitor)
- Traffic Monitor (Fireware Web UI)
- View Device Log Messages in WebCenter
- View Log Messages (Dimension)
- Log Manager (WatchGuard Cloud)
With the release of Fireware v12.8, WatchGuard announced the deprecation of the WatchGuard Log Server, Report Server, and Quarantine Server. WSM still includes these server components, but they are no longer supported in v12.9 and higher. We will remove them in a future WSM release.
In Fireware v12.7 and higher, you can select an option to specify the maximum number of log messages the Firebox generates for some types of events. The options are:
- Set Maximum Log Rate — Specify the maximum number of log messages for each minute
- Unlimited — Do not limit the number of log messages

You can configure the log rate for Blocked Sites, Blocked Ports, and these Default Packet Handling categories:
- IP Spoofing Attacks
- Port Scan
- IP Scan
- IP Source Route
- IPSec, IKE, SYN, ICMP, UDP Flood Attacks
- DDOS Attack Destination
- DDOS Attack Source
The log rate you specify for Blocked Sites also controls the maximum number of Geolocation log messages.
Log rate limits apply to all logs of that type, regardless of the event that generates the log that reaches the limit. For example, if you set the Blocked Ports log rate limit to 5, after the Firebox generates 5 Blocked Ports logs in a minute, it does not generate any more Blocked Ports logs until the next minute.
For a packet filter policy that allows connections, this check box appears in the Logging settings.
For proxy policies, this setting is in the proxy action and is called Enable Logging for Reports.
When you select this check box, whenever a connection matches the configuration in the policy, the Firebox sends a log message to Dimension or WatchGuard Cloud for inclusion in predefined reports. The log message, which is sent at the end of the connection, includes connection duration and bandwidth. These log messages also appear in Traffic Monitor for proxy policies, but not for packet filters.
For more information about viewing reports, go to:
When you select this check box, the Firebox sends an event notification to the SNMP management system. Simple Network Management Protocol (SNMP) is a set of tools used to monitor and manage networks. An SNMP trap is an event notification the device sends to the SNMP management system when a specified condition occurs.
If you select the Send SNMP Trap check box and you have not yet configured SNMP, a dialog box opens and asks if you want to do this. Click Yes to go to the SNMP Settings dialog box. You cannot send SNMP traps if you do not configure SNMP.
For more information about SNMP, go to:
When you select this check box, the Firebox generates an alarm log message that contains alarm_type=email when the specified event occurs. All alarm messages appear in the Alarms report. You can also receive notification about alarms. For more information about notification, go to About Notification Settings.
This setting enables the Firebox to send log messages required to generate the Alarms report, even if other logging settings are disabled.
When Dimension, WatchGuard Cloud, or a WSM Log Server receives the alarm log message, it can send an email notification to specified email addresses. For the server to send email notifications, you must configure email notification settings and email recipients in WatchGuard Cloud, Dimension, or WSM Log Server. For more information about how to configure email notification settings, go to:
- Dimension — Configure Notification Settings for Dimension
- WatchGuard Cloud — Configure Rules for Notifications
- WSM Log Server — Configure Notification Settings for the Log Server
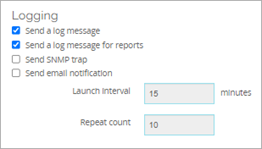
You can enter values for these options to limit the number of notifications in a specified period of time:
- Launch Interval — The time (in minutes) for the notification interval. This limits the notifications sent for the same event to the number specified in the repeat count for the specified period of time.
- Repeat Count — The maximum amount of notifications to send. When the number of notifications sent is equal to the repeat count, the Firebox sends no further notifications until the time specified in the launch interval expires.
For example, you set Launch Interval to 10 minutes and Repeat Count to 4. The Firebox detects a port space probe that starts at 10:00 AM and continues each minute. The Firebox starts to generate log messages and notifications for the event.
These actions occur at these times:
- 10:00 — Initial port space probe (first event)
- 10:01 — Second event starts (first repeat count notification)
- 10:02 — Third event starts (second repeat count notification)
- 10:03 — Fourth event starts (third repeat count notification)
- 10:04 — Fifth event starts (fourth repeat count notification)
- 10:05 — Sixth event starts (no notification until the launch interval expires at 10:10)
When you select this check box, the Firebox generates an alarm log message when the specified event occurs. All alarm messages appear in the Alarms report. You can also receive notification about alarms. For more information about notification, go to About Notification Settings.
This setting enables the Firebox to send log messages required to generate the Alarms report, even if other logging settings are disabled.
When you enable notification, you specify a notification method. This sets the alarm type in the log message, and controls how you can receive notification when the event occurs. Select one of these options:
The Firebox sends an alarm log message that contains alarm_type=email.
When Dimension, WatchGuard Cloud, or a WSM Log Server receives the alarm log message, it can send an email notification to specified email addresses. For the server to send email notifications, you must configure email notification settings and email recipients in WatchGuard Cloud, Dimension, or WSM Log Server. For more information about how to configure email notification settings, go to:
- Dimension — Configure Notification Settings for Dimension
- WatchGuard Cloud — Configure Rules for Notifications
- WSM Log Server — Configure Notification Settings for the Log Server
Pop-Up Window
The Firebox sends an alarm log message that contains alarm_type=pop-up.
If you select this option, the alarm log message appears in the Alarms report, but no other alert or email notification is generated.
When you select Pop-Up Window, you can enter values for these options to limit the number of notifications in a specified period of time:
- Launch Interval — The time (in minutes) for the notification interval. This limits the notifications sent for the same event to the number specified in the repeat count for the specified period of time.
- Repeat Count — The maximum amount of notifications to send. When the number of notifications sent is equal to the repeat count, the Firebox sends no further notifications until the time specified in the launch interval expires.
For example, you set Launch Interval to 10 minutes and Repeat Count to 4. The Firebox detects a port space probe that starts at 10:00 AM and continues each minute. The Firebox starts to generate log messages and notifications for the event.
These actions occur at these times:
- 10:00 — Initial port space probe (first event)
- 10:01 — Second event starts (first repeat count notification)
- 10:02 — Third event starts (second repeat count notification)
- 10:03 — Fourth event starts (third repeat count notification)
- 10:04 — Fifth event starts (fourth repeat count notification)
- 10:05 — Sixth event starts (no notification until the launch interval expires at 10:10)
WSM Log Server no longer supports pop-up window notification. We recommend you select the default Email notification method in Fireware v12.10.4 and lower.
Logging and Notification in Policies
Where you configure policy logging settings depends on the type of policy. The setting that controls logging for reports is different for packet filter policies and proxy policies.
Packet filter policies
For packet filter policies, you configure these logging settings in the policy properties:
- Send Log Message
- Send a Log Message for Reports
- Send SNMP Trap
- Send Email Notification (Fireware v12.11 and higher) or Send Notification (Fireware v12.10.4 and lower)
The Send a Log Message for Reports setting appears only in packet filter policies that allow connections. Packet filter policies that deny connections always generate log messages for reports.
Fireboxes that run Fireware v12.10.3 or higher include additional information in some types of log messages when you select the Send a Log Message for Reports setting. For more information, go to Read a Log Message.
The Pop-Up Window option in Fireware v12.10.4 and lower does not generate a pop-up notification. To generate an alert in WatchGuard Cloud, select the Email notification method. For more information, go to Configure Firebox Notification Rules.
Proxy policies
For proxy policies, you configure these logging settings in the policy properties.
- Send Log Message
- Send SNMP Trap
- Send Email Notification (Fireware v12.11 and higher) or Send Notification (Fireware v12.10.4 and lower)
For proxy policies, the setting that enables the Firebox to send a log message for reports is in the proxy action, and is called Enable Logging for Reports.

Logging settings for a proxy action in Fireware Web UI.
Proxy actions also include a setting to override the diagnostic log level for policies that use the proxy action. For information about the diagnostic log levels, go to Set the Diagnostic Log Level.