Configure Mobile Security Device Compliance
The FireClient app is no longer available for download from the Apple App Store or Google Play Store.
In the Mobile Security configuration, on the Device Compliance tab, you configure the compliance settings for Android and iOS devices, and configure how Mobile Security sets the compliance status for mobile devices that reconnect.
Before you configure Mobile Security device compliance, you must Enable Mobile Security.
Configure Device Compliance Settings for Android Devices
When you configure the Device Compliance settings for Android devices, you can specify which OS version are compliant . You can also choose whether to allow devices that are rooted, devices that have USB debugging enabled, or devices that allow installation of applications from unknown sources. You can also specify whether to allow connections from devices that have potentially insecure applications installed.
When mobile devices use FireClient to connect to your network, FireClient downloads the compliance settings you specified and uses them to assess whether the mobile device is compliant.
- Select Subscription Services > Mobile Security.
The Mobile Security configuration settings appear. - Select the Device Compliance tab.
The Device Compliance settings appear. - From the Compliance settings for drop-down list, select Android Devices.
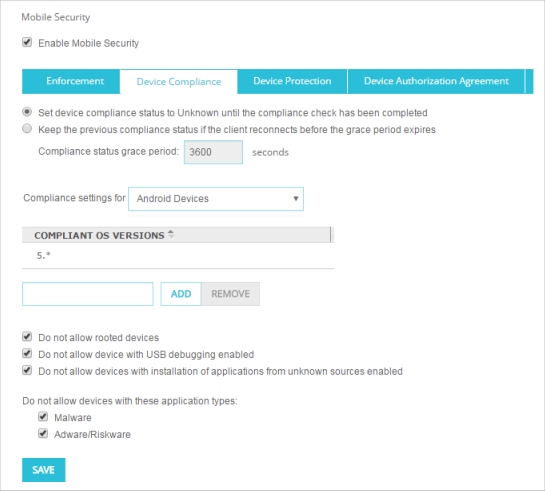
- To specify which OS versions a Android devices can run and be compliant, type the OS version in the text box and click Add.
OS versions can be any number in the format major.minor.subminor. You can also include the * wildcard character. For example you can type 6.* or 6.0.* for the OS version.
- To remove an OS version from the Compliant OS Versions list, select the version from the list and click Remove.
- Select the check box for each Mobile Security compliance option to enforce.
All compliance options are selected by default.- Do not allow rooted devices
- Do not allow devices with USB debugging enabled
- Do not allow devices with installation of applications from unknown sources enabled
- Do not allow devices with Malware
- Do not allow devices with Adware/Riskware
- Click Save.
- Select Subscription Services > Mobile Security.
The Mobile Security dialog box appears. - Select the Device Compliance tab.
The Device Compliance settings appear. - From the Compliance settings for drop-down list, select Android Devices.
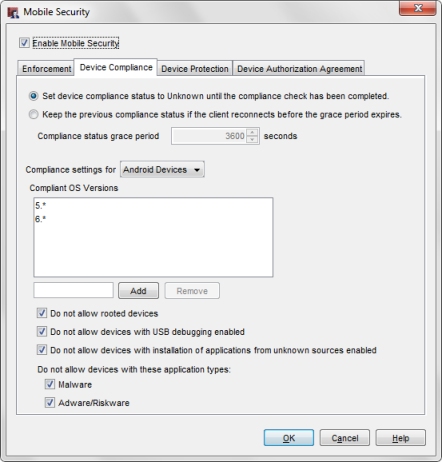
- To specify which OS versions Android devices can run and be compliant, type the OS version in the text box and click Add.
OS versions can be any number in the format major.minor.subminor. You can also include the * wildcard character. For example you can type 6.* or 6.0.* for the OS version.
- To remove an OS version from the Compliant OS Versions list, select the version from the list and click Remove.
- Select the check box for each Mobile Security compliance option to enforce.
All compliance options are selected by default.- Do not allow rooted devices
- Do not allow devices with USB debugging enabled
- Do not allow devices with installation of applications from unknown sources enabled
- Do not allow devices with Malware
- Do not allow devices with Adware/Riskware
- Click OK.
When Mobile Security is configured to not allow application types that are Malware or Adware/Riskware, an Android device is not compliant if it contains installed applications or APK (Android application package) files categorized as malware, adware, or riskware. FireClient can detect APK files within compressed archive files such as .zip. gz, rar, and .jar files.
Configure Device Compliance Settings for iOS Devices
When you configure the Device Compliance settings for iOS devices, you can specify which OS versions are compliant, and choose whether or not to allow connections to your network from devices that are jailbroken.
- On the Mobile Security page, select the Device Compliance tab.
- From the Compliance settings for drop-down list, select iOS Devices.
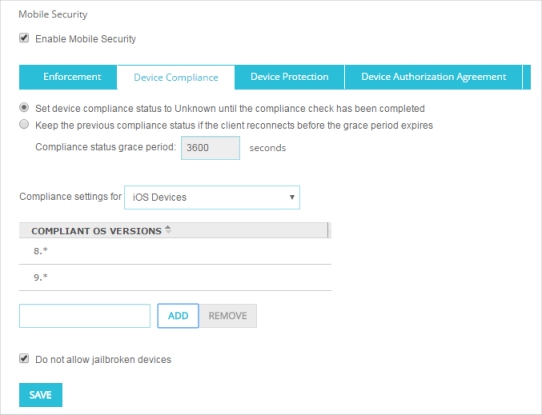
- To specify which OS versions an iOS device can run and be compliant, type the OS version in the text box and click Add.
OS versions must be a number in the format major.minor.subminor. You can also include the * wildcard character. For example you can specify 9.*, or 9.2.* as the OS version.
- To remove an OS version from the Compliant OS Versions list, select the version from the list and click Remove.
- By default jailbroken devices are not allowed. To allow jailbroken devices to connect to your network, clear the Do not allow jailbroken devices check box.
- Click Save.
- In the Mobile Security dialog box, select the Device Compliance tab.
- From the Compliance settings for drop-down list, select iOS Devices.
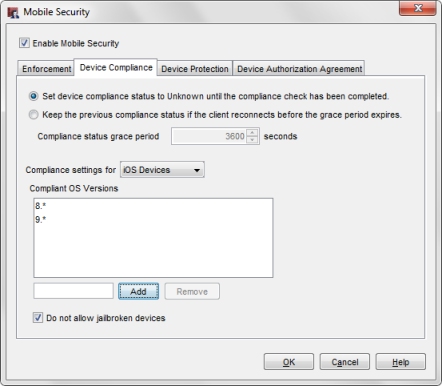
- To specify which OS versions an iOS device can run and be compliant, type the OS version in the text box and click Add.
OS versions must be a number in the format major.minor.subminor. You can also include the * wildcard character. For example you can specify 9.*, or 9.2.* as the OS version.
- To remove an OS version from the Compliant OS Versions list, select the version from the list and click Remove.
- By default jailbroken devices are not allowed. To allow jailbroken devices to connect to your network, clear the Do not allow jailbroken devices check box.
- Click OK.
Configure Reconnection Settings
You can specify how Mobile Security sets the compliance status for mobile clients that reconnect to the network. Mobile Security has two options for how to manage clients that disconnect and reconnect.
Set device compliance status to Unknown until the compliance check has been completed
If a mobile device disconnects and reconnects, FireClient sets the device compliance status to Unknown. When the mobile device reconnects, FireClient completes a new compliance check and sends the result to the Firebox. While the compliance status is Unknown, traffic from that client is dropped.
This is the most aggressive compliance check option, and is selected by default.
Keep the previous compliance status if the client reconnects before the grace period expires.
If a mobile device reconnects within the specified grace period, FireClient sends the result of the most recent compliance check to the Firebox and starts a new compliance check. When the new compliance check is complete, FireClient sends the result to the Firebox. If the mobile device reconnects after the specified grace period has expired, FireClient completes a new compliance check and sends that result to the Firebox.
Select this option to reduce dropped traffic for clients that reconnect. If you choose this option, you can specify the grace period. The default grace period is 3600 seconds (1 hour).
- On the Device Compliance tab, select an option:
- Set device compliance status to Unknown until the compliance check has been completed (Default setting)
- Keep the previous compliance status if the client reconnects before the grace period expires
- To change the grace period for clients that reconnect, in the Compliance status grace period text box, specify the grace period in seconds.
- Click Save.
- On the Device Compliance tab, select an option:
- Set device compliance status to Unknown until the compliance check has been completed (Default setting)
- Keep the previous compliance status if the client reconnects before the grace period expires
- To change the grace period for clients that reconnect, in the Compliance status grace period text box, specify the grace period in seconds.
- Click OK.