Use Mobile VPN with IPSec with an Android Device
To make an IPSec VPN connection to a Firebox from an Android device:
- Your VPN client must operate in Aggressive mode.
- The Firebox must be configured with Phase 1 and 2 transforms that are supported by the Android device.
Recent versions of the native Android VPN client use Main mode which is not compatible with Mobile VPN with IPSec. You cannot view or change the mode setting on the native Android VPN client. However, if the hardware manufacturer of your Android device modified the native VPN client, you might be able to change this setting.
If you cannot change your device settings to Aggressive mode, we recommend that you try one of these connection methods:
- If your hardware manufacturer installed its own VPN client on your Android device, try to connect with that client if it can operate in Aggressive mode. For more information, see the documentation from the manufacturer.
- In the settings for the native Android VPN client, configure the L2TP with IPSec option. Next, enable L2TP on your Firebox. L2TP on the Firebox uses Main mode. For more information about L2TP, go to About L2TP User Authentication.
- Install the OpenVPN SSL client on your Android device. You must manually download the SSL client profile from the SSL Portal on your Firebox. For more information about the client profile, go to Manually Distribute and Install the Mobile VPN with SSL Client Software and Configuration File.
Authentication and Encryption Settings
Android devices have a pre-configured list of supported VPN transforms. Unless the hardware manufacturer of your device modified the native Android VPN client, you cannot view this list or specify different default transforms. Recent Android OS versions have these default transforms:
Phase 1 — SHA2(256)–AES(256)–DH2
Phase 2 — SHA2(256)–AES(256)
Some older versions of Android OS use these default transforms:
Phase 1 — SHA1–AES(256)–DH2
Phase 2 — SHA1–AES(256)
In some cases, the hardware manufacturer of your Android device might specify different default transforms for the native Android VPN client.
To initiate a VPN connection to the Firebox, the Android device sends its default transform set to the Firebox. You must configure the Firebox with transforms supported by Android for the VPN connection to establish. We recommend that you specify the default Android transform set in your Mobile VPN with IPSec settings on the Firebox.
If you specify Firebox transforms different from the default Android transform set, the Android device sends the next transform set on its list. This process repeats until the Android device finds a transform set on its list that match the Firebox settings, or until the Android device reaches a retry limit or has no additional transforms to test.
To troubleshoot connection issues, go to Troubleshoot Mobile VPN with IPSec and Traffic Monitor.
Configure the Firebox
Before you can connect with the native Android VPN client, you must configure the Mobile VPN with IPSec settings on your Firebox.
- (Fireware v12.3 or higher) Select VPN > Mobile VPN.
- In the IPSec section, select Configure.
The Mobile VPN with IPSec page appears. - (Fireware v12.2.1 or lower) Select VPN > Mobile VPN with IPSec.
The Mobile VPN with IPSec page appears. - Click Add.
The Mobile VPN with IPSec Settings page appears.

- In the Name text box, type the name of the authentication group your Android VPN users belong to.
You can type the name of an existing group or the name for a new Mobile VPN group. Make sure the name is unique among VPN group names, as well as all interface and VPN tunnel names.
- From the Authentication Server drop-down list, select an authentication server.
Make sure that this method of authentication is enabled.
If you create a Mobile VPN user group that authenticates to an external authentication server, make sure you create a group on the server with the same name you specified in the wizard for the Mobile VPN group. If you use Active Directory as your authentication server, the users must belong to an Active Directory security group with the same name as the group name you configure for Mobile VPN with IPSec. For more information, go to Configure the External Authentication Server.
- Type and confirm the Passphrase to use for this tunnel.
- In the Firebox IP Addresses section, type the primary external IP address or domain name to which Mobile VPN users in this group can connect.
- Select the IPSec Tunnel tab.
The IPSec Tunnel settings appear.
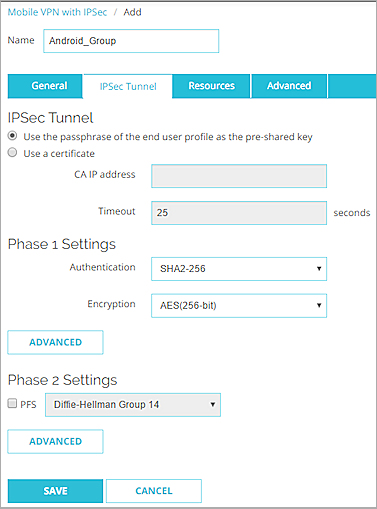
- Select Use the passphrase of the end user profile as the pre-shared key.
This is the default setting. - From the Authentication drop-down list, select SHA-2. Select SHA-1 if your Android device does not support SHA-2.
- From the Encryption drop-down list, select AES (256-bit). This is the default encryption setting for Android devices.
- In the Phase 1 Settings section, click Advanced.
The Phase 1 Advanced Settings dialog box appears.
- Set the SA Life to 1 hour.
The Android VPN client is configured to rekey after 1 hour. If this profile is only used for connections by the Android VPN, set the SA Life to 1 hour to match the client setting.
If you plan to use this VPN profile for all supported VPN clients, set the SA Life to 8 hours. The Android VPN client still uses the smaller rekey value of 1 hour.
- From the Key Group drop-down list, select Diffie-Hellman Group 2. This is the default key group for Android devices.
- Do not change any of the other Phase 1 advanced settings.

- Click OK.
- In the Phase 2 Settings section, clear the PFS check box.

- In the Phase 2 Settings section, click Advanced.
The Phase 2 Advanced Settings dialog box appears.

- From the Authentication drop-down list, select SHA-2. Select SHA-1 if your Android device does not support SHA-2.
- From the Encryption drop-down list, select AES (256-bit), which is the default encryption setting for Android devices.
- In the Force Key Expiration settings, set the expiration Time to 1 hours and clear the Traffic check box.
- Click OK.
- Select the Resources tab.
- Select the Allow All Traffic Through Tunnel check box.
This configures the tunnel for default-route VPN. The Android VPN client does not support split tunneling. - In the Virtual IP Address Pool list, add the internal IP addresses that are used by Mobile VPN users over the tunnel.
To add an IP address or a network IP address to the virtual IP address pool, select Host IP or Network IP, type the address, and click Add.
Mobile VPN users are assigned an IP address from the virtual IP address pool when they connect to your network. The number of IP addresses in the virtual IP address pool should be the same as the number of Mobile VPN users.
WARNING: The virtual IP addresses must be on a different subnet than the local networks. The virtual IP addresses cannot be used for anything else on your network.
- Click OK.
- Click the Advanced tab.

- Configure the DNS settings:
Assign the network DNS/WINS settings to mobile clients
If you select this option, mobile clients receive the DNS and WINS settings you specify at Network > Interfaces > DNS/WINS. For example, if you specify the DNS server 10.0.2.53in the Network DNS/WINS settings, mobile VPN clients use 10.0.2.53as a DNS server.
By default, the Assign the Network DNS/WINS Server settings to mobile clients setting is selected for new mobile VPN configurations.
Do not assign DNS or WINS settings to mobile clients
If you select this option, clients do not receive DNS or WINS settings from the Firebox.
Assign these settings to mobile clients
If you select this option, mobile clients receive the domain name, DNS server, and WINS server settings you specify in this section. For example, if you specify example.com as the domain name and 10.0.2.53 as the DNS server, mobile clients use example.com for unqualified domain names and 10.0.2.53 as the DNS server.
You can specify one domain name, up to two DNS server IP addresses, and up to two WINS server IP addresses.
For more information about DNS and WINS server settings for Mobile VPN with IPSec users, go to Configure DNS and WINS Servers for Mobile VPN with IPSec.
- Click Save.
First, use the Mobile VPN with IPSec Wizard to configure the basic settings:
- Select VPN > Mobile VPN > IPSec.
The Mobile VPN with IPSec Configuration dialog box appears. - Click Add.
The Add Mobile VPN with IPSec Wizard appears. - Click Next.
The Select a user authentication server page appears.

- From the Authentication Server drop-down list, select an authentication server.
You can authenticate users to the Firebox (Firebox-DB) or to an Active Directory or RADIUS server. Make sure the authentication method you choose is enabled.
- In the Group Name text box, type the name of the authentication group your Android users belong to.
You can type the name of a Mobile VPN group you have already created or type a group name for a new Mobile VPN group. Make sure the name is unique among VPN group names, as well as all interface and tunnel names.
If you create a Mobile VPN user group that authenticates to an external authentication server, make sure you create a group on the server with the same name you specified in the wizard for the Mobile VPN group. If you use Active Directory as your authentication server, the users must belong to an Active Directory security group with the same name as the group name you configure for Mobile VPN with IPSec. For more information, go to Configure the External Authentication Server.
- Click Next.
The Select a tunnel authentication method page appears.

- Select Use this passphrase. Type and confirm the passphrase.
- Click Next.
The Direct the flow of Internet traffic page appears.

- Select Yes, force all Internet traffic to flow through the tunnel..
This configures the tunnel for default-route VPN. The Android VPN client does not support split tunneling. - Click Next.
The Create the virtual IP address pool page appears.

- Click Next and Finish.
- For a default-route VPN configuration, the configuration automatically allows access to all network IP addresses and the Any-External alias.
Mobile VPN users are assigned an IP address from the virtual IP address pool when they connect to your network. The number of IP addresses in the virtual IP address pool should be the same as the number of Mobile VPN users.
WARNING: The virtual IP addresses must be on a different subnet than the local networks. The virtual IP addresses cannot be used for anything else on your network.
- Click Next.
- To add users to the new Mobile VPN with IPSec group, select the Add users check box.
- Click Finish.
The Mobile VPN configuration you created appears in the Mobile VPN with IPSec Configuration dialog box.

Next, you must edit the VPN Phase 1 and Phase 2 settings to match the settings for the Android VPN client.
- In the Mobile VPN with IPSec Configuration dialog box, select the configuration you just added.
- Click Edit.
The Edit Mobile VPN with IPSec dialog box appears. - Select the IPSec Tunnel tab.

- From the Authentication drop-down list, select SHA2-256. Select SHA-1 if your Android device does not support SHA-2.
- From the Encryption drop-down list, select AES (256-bit), which is the default encryption setting for Android devices.
- Click Advanced.
The Phase 1 Advanced Settings dialog box appears.

- Set the SA Life to 1 hour.
The Android VPN client is configured to rekey after 1 hour. If this profile is only used for connections by the Android VPN , set the SA Life to 1 hour to match the client setting.
If you want to use this VPN profile for all supported VPN clients, set the SA Life to 8 hours. The Android VPN client still uses the smaller rekey value of 1 hour.
- From the Key Group drop-down list, select Diffie-Hellman Group 2.
- Do not change any of the other Phase 1 Advanced Settings.
- Click OK.
- In the Edit Mobile VPN with IPSec dialog box, click Proposal.

- From the Authentication drop-down list, select SHA2-256. Select SHA-1 if your Android device does not support SHA-2.
- From the Encryption drop-down list, select AES (256-bit), which is the default encryption setting for Android devices.
- In the Force Key Expiration settings, set the expiration Time to 1 hour, and clear the Traffic check box.
- Click OK.
- In the Edit Mobile VPN with IPSec dialog box, clear the PFS check box.
Perfect Forward Secrecy is not supported by the Android VPN client.

Finally, configure the DNS settings.
- Click the Advanced tab.
- Configure the DNS settings:
Assign the network DNS/WINS settings to mobile clients
If you select this option, mobile clients receive the DNS and WINS settings you specify at Network > Interfaces > DNS/WINS. For example, if you specify the DNS server 10.0.2.53in the Network DNS/WINS settings, mobile VPN clients use 10.0.2.53as a DNS server.
By default, the Assign the Network DNS/WINS Server settings to mobile clients setting is selected for new mobile VPN configurations.
Do not assign DNS or WINS settings to mobile clients
If you select this option, clients do not receive DNS or WINS settings from the Firebox.
Assign these settings to mobile clients
If you select this option, mobile clients receive the domain name, DNS server, and WINS server settings you specify in this section. For example, if you specify example.com as the domain name and 10.0.2.53 as the DNS server, mobile clients use example.com for unqualified domain names and 10.0.2.53 as the DNS server.
You can specify one domain name, up to two DNS server IP addresses, and up to two WINS server IP addresses.
For more information about DNS and WINS server settings for Mobile VPN with IPSec users, go to Configure DNS and WINS Servers for Mobile VPN with IPSec.
- Click OK.
- Save the configuration file to your Firebox.
To authenticate from the Android VPN client, Android VPN users must be members of the authentication group you specified in the Add Mobile VPN with IPSec Wizard.
- For information about how to add users to a Firebox user group, go to Define a New User for Firebox Authentication.
- If you use a third-party authentication server, use the instructions provided in your vendor documentation.
Configure the Native Android VPN Client
After you configure the Firebox, users in the authentication group you specified in the Mobile VPN with IPSec profile on the Firebox can use the native Android VPN client to connect. To use the native Android VPN client, the user must manually configure the VPN client settings to match the settings configured on the Firebox.
WatchGuard provides interoperability instructions to help our customers configure WatchGuard products to work with products created by other organizations. If you need more information or technical support about configuring a non-WatchGuard product, see the documentation and support resources for that product.
For Android devices with Android version 12 or higher, we recommend you configure a mobile VPN with IKEv2 connection with the free StrongSwan app. For more information, go to Configure Android Devices for Mobile VPN with IKEv2.
To manually configure the native VPN client on the Android device, in Android 8.0 (Oreo):
- Tap Settings > Network & Internet > VPN.
- Tap the + button.
The Edit VPN profile dialog box appears. - In the Name text box, type a descriptive name for the VPN connection.
- From the Type drop-down list, select IPSec Xauth PSK.
- In the Server address text box, type the external IP address of the Firebox.
- In the IPSec identifier text box, type the group name you specified in the Mobile VPN with IPSec configuration on the Firebox.
- Drag the slider down to see more settings.
- In the IPSec pre-shared key text box, type the tunnel passphrase you specified in the Mobile VPN with IPSec configuration on the Firebox.
- In the Username text box, type the username for a user in the specified authentication group.
Specify the user name only. Do not preface the user name with a domain name and do not specify an email address. - In the Password text box, type the password for a user in the specified authentication group.

- Click Save.
The VPN connection you created is saved to the VPN list.

- To connect, click the VPN connection you created.
The Connect To dialog box appears.

- Click Connect.
To verify your connection was successful and that the VPN tunnel is active, browse to a website that shows your IP address such as www.whatismyip.com. If your Android device is connected through the VPN, your IP address is the external IP address of the Firebox.
If your device has a later version of Android, the steps you must follow to configure the native VPN client might be different. For instructions that apply to your Android version, see the documentation from your device manufacturer.
You can configure the native VPN client for Android versions 8.0 (Oreo) to Android 11. For Android versions 12 and higher, we recommend you configure a mobile VPN with IKEv2 connection. For more information, go to Configure Android Devices for Mobile VPN with IKEv2.