Use Certificates for Mobile VPN with IPSec Tunnel Authentication
When you configure Mobile VPN with IPSec, you can configure the tunnel to use a certificate for tunnel authentication instead of a pre-shared key. The certificate, generated by a WatchGuard Management Server, is used to authenticate the tunnel before the client sends the user name and password for user authentication.
The IPSec certificate generated by the WatchGuard Management Server is valid for one year. When the Firebox requires a new IPSec certificate, it will automatically notify the Management Server to renew the certificate. You do not need to manually renew the certificate when you see expiry warnings. If you still want to manually renew the certificate, you can generate a new certificate from the CA manager on the Management Server. For more information, go to Manage Certificates on the Management Server.
To use a certificate for Mobile VPN with IPSec tunnel authentication:
- The Firebox must be managed by a WatchGuard Management Server.
- You must use Policy Manager to generate the configuration profile and certificate files to distribute to users
- Your mobile users must use the WatchGuard IPSec Mobile VPN client for Windows or macOS
Configure Mobile VPN with IPSec on the Firebox to use a Certificate
Before you enable Mobile VPN with IPSec to use a certificate for tunnel authentication, you must connect to the Management Server with WatchGuard System Manager at least once to automatically install the Management Server root certificate on your management computer.
In Policy Manager, you can configure a new Mobile VPN with IPSec group to use a certificate, or you can edit an existing tunnel to enable it.
- Select VPN > Mobile VPN > IPSec.
- Click Add to start the Add Mobile VPN with IPSec Wizard.
- Configure the authentication server and group as described in Configure the Firebox for Mobile VPN with IPSec.
- On the Select a tunnel authentication method step, select Use an RSA certificate issued by your WatchGuard Management Server.
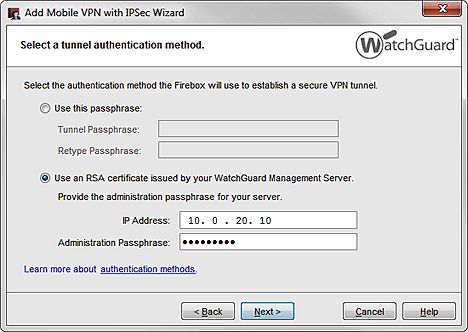
- In the IP Address text box, type the IP address of your WatchGuard Management Server.
- In the Passphrase text box, type the passphrase for the admin user on your Management Server.
- Click Next. Tip!
The wizard connects to the management server to generate the certificate for the mobile user configuration. - Complete the rest of the wizard settings as described in Configure the Firebox for Mobile VPN with IPSec.
- Select VPN > Mobile VPN > IPSec.
- Select an existing Mobile VPN configuration and click Edit.
- Select the IPSec Tunnel tab.
- Select Use a Certificate.
- In the CA IP Address text box, type the IP address of your Management Server.
- In the Passphrase text box, type the passphrase for the Admin user on your Management Server.
- In the Timeout text box type the time in seconds before the Firebox stops an attempt to authenticate a Mobile VPN with IPSec tunnel if there is no response from the certificate authority. We recommend you keep the default value.
- Click OK.
The Management Server Configuration dialog box appears.
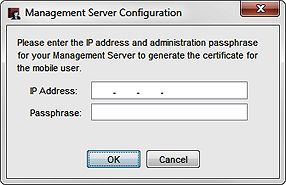
- In the IP Address text box, type the IP address to connect to your Management Server.
- In the Passphrase text box, type the passphrase for the admin user account on your Management Server.
- Click OK. Tip!
Policy Manager connects to the Management Server to generate the certificate for the mobile user configuration.
- (Fireware v12.3 or higher) Select VPN > Mobile VPN.
- In the IPSec section, select Configure.
The Mobile VPN with IPSec page appears. - (Fireware v12.2.1 or lower) Select VPN > Mobile VPN with IPSec.
The Mobile VPN with IPSec page appears. - Click Add to add a new VPN group configuration or select an existing group and click Edit.
- Select the IPSec Tunnel tab.
- Select Use a certificate.
- In the CA IP address text box, type the IP address of your Management Server.
- In the Timeout text box type the time in seconds before the Firebox stops an attempt to authenticate a Mobile VPN with IPSec tunnel if there is no response from the certificate authority. We recommend you keep the default value.
- Configure the settings on the General and Resource tabs as described in Configure the Firebox for Mobile VPN with IPSec.
If you change the tunnel authentication for existing users, you must generate and distribute the new profile and certificate to the mobile users.
Generate the Certificate and End-User Profile
After you configure a mobile VPN with IPSec profile to use a certificate for tunnel authentication, you must use Policy Manager to generate the .wgx configuration profile and certificate file to send to the mobile users.
To generate an end user profile file for a group, from Policy Manager:
- Select VPN > Mobile VPN > IPSec.
- Select the Mobile VPN group.
- Click Generate.
The Management Server Configuration dialog box appears.

- In the IP Address text box, type the IP address to connect to your Management Server. The IP address you specify here must be an address that your management computer can use to connect to the Management Server. It might be different from the address in the configuration that the Firebox uses to connect to the Management Server.
- In the Passphrase text box, type the passphrase for the admin user account on your Management Server.
- Click OK. Tip!
Policy Manager generates the configuration files and certificate file and shows the location where you can find the generated files..
Use a secure method to distribute the encrypted end-user profile (.wgx file) and the PKCS12 certificate (.p12 file) to mobile users who use the WatchGuard IPSec Mobile VPN client.
Configure the VPN Client
Each user must import the profile and certificate to the IPSec Mobile VPN client. For more information about how to do this, go to:
Manage Certificates on the Management Server
You can use the WatchGuard WebCenter tool, CA Manager to see and manage certificates on the management server. The common name of the certificate is the name of the Mobile VPN with IPSec profile.
For more information, go to Manage Certificates on the Management Server.