A network security device, such as a firewall, separates your internal networks from external network connections to decrease the risk of an external attack. This diagram shows how a firewall protects the computers on a trusted network from the Internet.
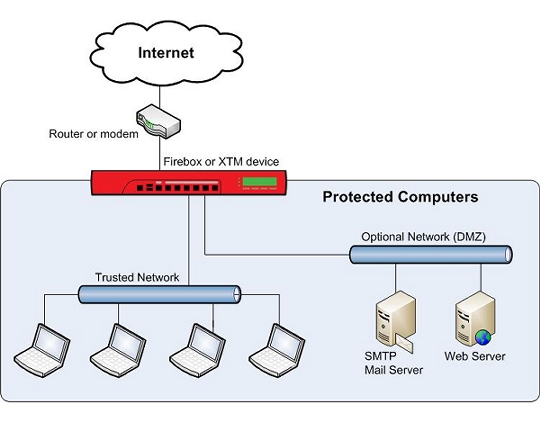
Firewalls use access policies to identify and filter different types of information. They can also control which policies or ports the protected computers can use on the Internet (outbound access). For example, many firewalls have sample security policies that allow only specified traffic types. Users can select the policy that is best for them. Other firewalls, such as Fireboxes, allow the user to customize these policies.
For more information, go to About Services and Policies and About Ports.
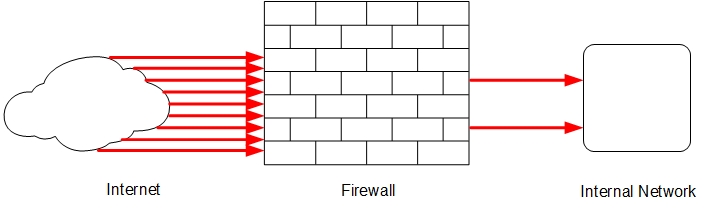
Firewalls can be either hardware or software. A firewall protects private networks from unauthorized users on the Internet. Traffic that enters or leaves the protected networks is examined by the firewall. The firewall denies network traffic that does not match the security criteria or policies.
In some closed, or default-deny firewalls, all network connections are denied unless there is a specific rule to allow the connection. To deploy this type of firewall, you must have detailed information about the network applications required to meet the needs of your organization. Other firewalls allow all network connections that have not been explicitly denied. This type of open firewall is easier to deploy, but it is not as secure.