Add, Change, or Delete Rules
When you add rules, you select the action for each rule, and you can edit, clone (use an existing rule definition to create a new rule), delete, or reset rules.
In Policy Manager, you can use either the simple or advanced view of the ruleset to add rules. Use the simple view to configure wildcard pattern matching with simple regular expressions. Use the advanced view to configure exact match and Perl-compatible regular expressions. In the advanced view you can also review the action for each rule and edit, clone (use an existing rule definition to create a new rule), delete, or reset rules.
For pattern matching, the wildcard characters for zero or more of any alphanumeric characters is *. The wildcard for one character is ?. These are the only wildcard characters currently used for pattern matching. For more information about regular expressions, go to About Regular Expressions.
For more information, go to About Rules and Rulesets.
When you configure a rule, you select the actions the proxy takes for each packet. Different actions appear for different proxies or for different features of a particular proxy. This list includes all possible actions:
Allow
Allows the connection.
Deny
Denies a specific request but keeps the connection if possible. Sends a response to the client.
Drop
Denies the specific request, drops the connection, and sends a response to the client.
Block
Denies the request, drops the connection, blocks the site, and sends a response to the client.
For more information on blocked sites, go to About Blocked Sites.
All traffic from this site's IP address is denied for the amount of time you specify in the Blocked Sites configuration.
Inspect
Inspects traffic content when content inspection is enabled on the HTTPS Proxy.
Replace
Replaces the address in the To field with an address you specify.
For example, you can send all email that is addressed to [email protected] to [email protected].
For an outbound proxy action, you can also use this rule to standardize a domain name.
For example, you can send all email addressed to the success-co.net domain to the successfulcompany.com domain. So, email sent to [email protected] is instead sent to [email protected].
For SMTP masquerading, you can create a rule for the Mail From or Rcpt To to replace olddomain.com with newdomain.com.
Strip
Removes an attachment from a packet and discards it. The other parts of the packet are sent through the Firebox to the intended destination.
Lock
Locks an attachment, and wraps it so that it cannot be opened by the user. Only the administrator can unlock the file.
AV Scan
Scans the attachment for viruses. If you select this option, Gateway AntiVirus is enabled for the policy.
Add Rules in Fireware Web UI
To add rules, from Fireware Web UI:
- On a Proxy Actions / Edit subcategory page, in the list of rules for a ruleset, click Add.
The Add Rule dialog box appears.

- In the Rule Name text box, type the name of the rule.
This text box is blank when you add a rule, and cannot be changed when you edit a rule. - For the Match Type drop-down list, select an option:
- Exact Match — Select when the contents of the packet must match the rule text exactly.
- Pattern Match — Select when the contents of the packet must match a pattern of text, can include wildcard characters.
- Regular Expression — Select when the contents of the packet must match a pattern of text with a regular expression.
- In the pattern text box, type the text of the rule.
If you selected Pattern Match as the rule setting, use an asterisk (*) or a question mark (?) as wildcard characters. - In the Rule Actions section, in the Action drop-down list, select the action the proxy takes for this rule.
- To create an alarm for this event, select the Alarm check box. An alarm tells users when a proxy rule applies to network traffic.
- To create a message for this event in the traffic log, select the Log check box.
Add Rules in Policy Manager (Simple View)
To add a new rule in simple view:
- In the Pattern text box, type a pattern that uses simple pattern matching syntax.
- Click Add.
The new rule appears in the Rules box. - Select the Actions to take:
- From the If matched drop-down list, set the action to take if the contents of a packet match one of the rules in the list.
- From the None matched drop-down list, set the action to take if the contents of a packet do not match a rule in the list.
- To configure an alarm for this event, select the Alarm check box.
An alarm notifies users when a proxy rule applies to network traffic. - To set the options for the alarm, from the Categories tree, select Proxy Alarm.
You can send an SNMP trap or an email, or open a pop-up window. - To create a message for this event in the traffic log, select the Log check box.
Add Rules in Policy Manager (Advanced View)
You use the advanced view to configure exact match and Perl-compatible regular expressions. For information on how to work with regular expressions, go to About Regular Expressions.
- In the Proxy Action Configuration dialog box, click Add.
The New Rule dialog box appears.
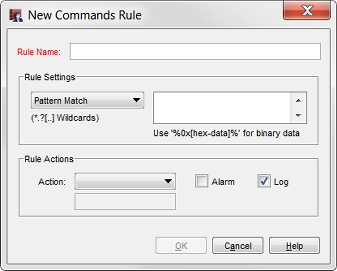
- In the Rule Name text box, type the name of the rule.
This text box is blank when you add a rule, and cannot be changed when you edit a rule. - For the Match Type drop-down list, select an option:
- Exact Match — Select when the contents of the packet must match the rule text exactly.
- Pattern Match — Select when the contents of the packet must match a pattern of text, can include wildcard characters.
- Regular Expression — Select when the contents of the packet must match a pattern of text with a regular expression.
- In the pattern text box, type the text of the rule.
If you selected Pattern Match as the rule setting, use an asterisk (*) or a question mark (?) as wildcard characters. - In the Rule Actions section, in the Action drop-down list, select the action the proxy takes for this rule.
- To create an alarm for this event, select the Alarm check box. An alarm tells users when a proxy rule applies to network traffic.
- To create a message for this event in the traffic log, select the Log check box.