Transport Layer Security (TLS) provides additional data security for IMAP. The TLS protocol provides communications security over the Internet and allows client and server applications to communicate in a way that is designed to prevent eavesdropping, tampering, or message forgery. The TLS protocol is based on the SSLv3 protocol but provides improved data security.
For more information about TLS, go to About Transport Layer Security (TLS).
The IMAP Proxy supports both implicit and explicit TLS. In the IMAP proxy action, the TLS settings are for implicit TLS and the STARTTLS settings are for explicit TLS. For information about how to configure explicit TLS in the IMAP proxy, go to IMAP-Proxy: STARTTLS.
You can enable both implicit and explicit TLS encryption in the same IMAP proxy action, but each connection uses only one encryption method. Connections on port 993 use implicit TLS encryption (IMAPS) and connections on port 143 use explicit TLS encryption (STARTTLS).
TLS for the IMAP-proxy is supported in Fireware v12.1 and higher.
To enable TLS support in the IMAP-proxy policy, you must enable content inspection in the proxy action.
About Certificates for TLS Encryption
When content inspection is enabled, the proxy action uses a certificate when it re-encrypts the traffic after inspection.
- For inbound traffic, the proxy action uses the default Proxy Server certificate.
- For outbound traffic, the proxy action uses the Proxy Authority certificate.
For more information about these certificates, go to About Certificates.
Change the TLS Support Option in the IMAP Proxy Policy
To enable content inspection in the IMAP proxy action, TLS Support must also be Enabled or Required in the IMAP-proxy policy.
In the IMAP proxy policy, you can set TLS Support to one of these options:
- Disabled — IMAP proxy listens on port 143 only
- Enabled — IMAP proxy listens on ports 143 and 993 (default)
- Required — IMAP proxy listens on port 993 only
- Edit the IMAP-proxy policy.

- In the Settings tab, from the TLS Support drop-down list, select Enabled or Required.
The IMAP and IMAPS ports in the policy are updated based on the option you choose.
- Edit the IMAP-proxy policy.

- On the Policy tab, from the TLS Support drop-down list, select Enabled or Required.Tip!
The IMAP and IMAPS ports in the policy Properties tab are updated based on the option you choose.
Enable Content Inspection in the IMAP Proxy Action
To enable content inspection in the IMAP-proxy, you must select the Inspect action in the TLS settings for the proxy action used by your IMAP-proxy policy. When you select the Inspect action, the proxy uses the settings in the TLS profile for content inspection. You can edit the TLS profile settings in the proxy action, or from the TLS Profiles page.
- Edit the IMAP-Proxy action used by your IMAP-proxy policy.
- Select the TLS tab.
The Content Inspection settings appear.

- From the TLS Profile drop-down list, select the TLS profile to use.
The settings for the selected profile appear in the Content Inspection Summary.
- Minimum Protocol Version — Shows the minimum protocol version allowed
- OCSP — Shows whether OCSP is set to Disabled, Lenient, or Strict (for TLS-Client profiles only)
- PFS Ciphers — Shows whether Perfect Forward Secrecy Ciphers is set to Allowed, Required, or None
- TLS Compliance — Shows whether the TLS profile enforces compliance with the TLS protocol standards
- To enable content inspection, from the Action drop-down list, select Inspect.
- To edit the TLS profile in Fireware Web UI, click Edit. To edit the TLS profile in Policy Manager, click
 . Predefined TLS profiles are not editable. To change the predefined TLS settings, click Clone to make an editable copy of the TLS profile.
. Predefined TLS profiles are not editable. To change the predefined TLS settings, click Clone to make an editable copy of the TLS profile. - Configure the TLS Profile settings as required for your network. For more information, go to Configure TLS Profiles.
- Edit the IMAP-Proxy action used by your IMAP-proxy policy.
- In the Categories list, select TLS.
The Content Inspection settings appear.
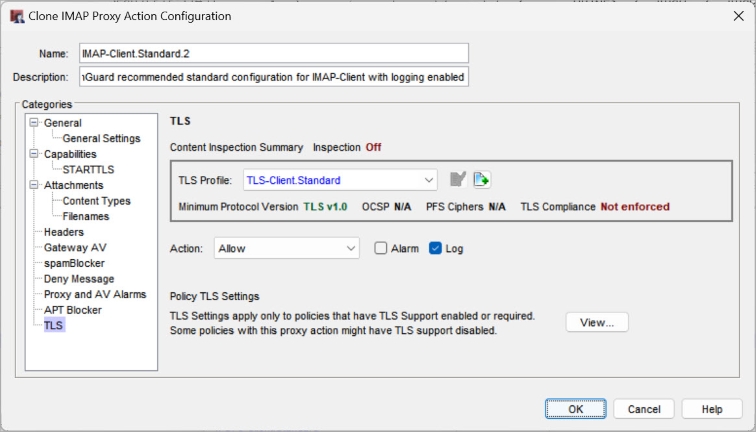
- From the TLS Profile drop-down list, select the TLS profile to use.
The settings for the selected profile appear in the Content Inspection Summary.
- Minimum Protocol Version — Shows the minimum protocol version allowed
- OCSP — Shows whether OCSP is set to Disabled, Lenient, or Strict (for TLS-Client profiles only)
- PFS Ciphers — Shows whether Perfect Forward Secrecy Ciphers is set to Allowed, Required, or None
- TLS Compliance — Shows whether the TLS profile enforces compliance with the TLS protocol standards
- To enable content inspection, from the Action drop-down list, select Inspect.
- To edit the TLS profile in Fireware Web UI, click Edit. To edit the TLS profile in Policy Manager, click
 . Predefined TLS profiles are not editable. To change the predefined TLS settings, click Clone to make an editable copy of the TLS profile.
. Predefined TLS profiles are not editable. To change the predefined TLS settings, click Clone to make an editable copy of the TLS profile. - Configure the TLS Profile settings as required for your network. For more information, go to Configure TLS Profiles.
See Policy TLS Settings
For a proxy policy to perform content inspection, the TLS Support option in the proxy policy must be set to Enabled or Required. If you edit the TLS settings in a proxy action from the Proxy Actions list, the proxy action could apply to more than one policy. After you enable content inspection, make sure that TLS Support is set to Enabled or Required in all policies that use the proxy action.
To see the TLS Support setting for all policies that use the proxy action:
- Edit the proxy action from the Proxy Actions list.
- In the proxy action TLS settings, click View.
A list of policies that use the proxy action appears, with the TLS Support setting for each policy.