WatchGuard recommends you enable Application Control for policies that handle outbound traffic from your network. You do not need to enable Application Control on policies for Branch Office VPNs to trusted sites, or for traffic between trusted hosts on your internal network.
When you configure the Application Control action, be very specific about which applications you choose to block. If you block by category, you may unintentionally block applications that you need for your network.
Application Control and WebBlocker
If you configure an HTTP or HTTPS-proxy policy with both WebBlocker and Application Control enabled, both services will apply to each connection. If WebBlocker allows a site but Application Control denies it, the site will be denied.
Application Control may not correctly identify HTTPS applications unless you enable content inspection in the HTTPS-proxy action.
Common Application Control Problems
These are common types of problems you might encounter with Application Control, and the solutions that most often resolve these problems.
When you configure Application Control on your Firebox device, you will see all applications which are in the signature set your device currently uses. If you do not see the application you want to block, you can confirm whether WatchGuard has a signature with the Application Control Portal.
If your device does not list an application which appears on the Application Control Portal, confirm that your device is configured to automatically download signature updates. For more information on this, go to Configure the Application Control Update Server.
There are several possible reasons users may still be able to access an application:
- The traffic uses a policy which is not configured for Application Control. Confirm that there is no policy for outbound traffic which does not have Application Control enabled.
- The user accessed the application over HTTPS. Make sure that you use the HTTPS or a TCP-UDP Proxy to handle HTTPS traffic, and the HTTPS proxy action has content inspection enabled.
- The Firebox device has an outdated version of the Application Control signature set. Confirm that your device is configured to automatically download signature updates. For more information, go to Configure the Application Control Update Server.
Application Control Log Messages
If a user cannot use an application, you can review the log messages in Traffic Monitor to troubleshoot. You can use the log messages to identify the policy and Application Control action that blocked the application.
For information about how to view log messages in Fireware Web UI, go to Traffic Monitor Web. For more information about how to view log messages in WatchGuard Cloud, go to Monitor Traffic on Fireboxes and FireClusters.
In a log message, you can view these details to troubleshoot:
- Event Time: The time the user tried to use the application.
- Action: The Deny or Allow action taken by the Firebox.
- Source IP: The IP address of the source that tried to connect to the application.
- Destination IP: The IP address of the application the user tried to connect to.
- Application Name: The name of the application the user tried to connect to.
- Firewall Policy: The name of the Firewall policy that handled the traffic.
- Application Category Name: The category of the application the user tried to connect to.
- Application Control Action: The name of the Application Control action that applied to the traffic.
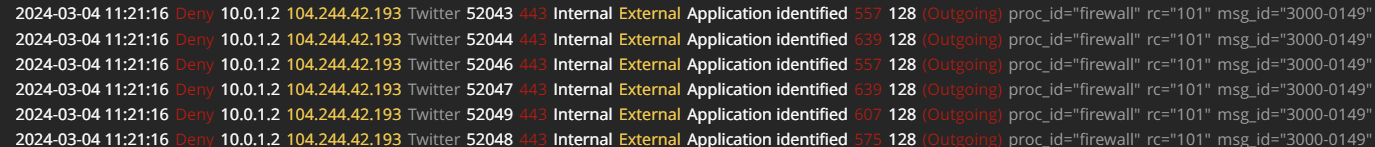
Example:
2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52043443 Internal External Application identified 557128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 3436610192 win 516"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303" 2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52044443 Internal External Application identified 639128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 3929390091 win 516"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303" 2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52046443 Internal External Application identified 557128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 2339242078 win 516"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303" 2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52047443 Internal External Application identified 639128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 4191371602 win 516"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303" 2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52049443 Internal External Application identified 607128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 2500534288 win 800"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303" 2024-03-04 11:21:16 Deny 10.0.1.2 104.244.42.193 Twitter 52048443 Internal External Application identified 575128(Outgoing)proc_id="firewall"rc="101"msg_id="3000-0149"src_ip_nat="10.0.3.0"tcp_info="offset 5 A 2765614535 win 800"app_name="Twitter"app_cat_name="Social networks"app_id="10"app_cat_id="25"app_beh_name="Access"app_beh_id="6"action="App Control Test"geo_dst="USA"sig_vers="18.303"
In this example:
- Event Time: 2024-03-04 11:21:1
- Action: Deny
- Source IP: 10.0.1.2
- Destination IP: 104.244.42.193
- Application Name: Twitter
- Firewall Policy: Outgoing
- Application Category Name: Social networks
- Application Control Action: App Control Test
About Security Services Precedence (Total Security Suite)
Configure Application Control Actions
Get Information About Applications