Test Your DNSWatch Protection
When you have DNSWatch protection, you should be able to browse to non-malicious sites without a problem. If you attempt to connect to a filtered content or malicious site, you should see a block page instead of the requested domain.
There are two tests to confirm that DNSWatch functions correctly on a protected network, Firebox, or a DNSWatchGO Client:
- Verify you can browse to non-malicious or regular domains, such as https://www.watchguard.com without issues
- Verify DNSWatch blocks malicious or filtered content domains, such as test.strongarm.io
Verify DNSWatch Blocks Malicious or Filtered Content Domains
You can perform this test on a DNSWatch protected network or on a portable device with the DNSWatchGO Client installed.
If you run the test on a portable device to test the DNSWatchGO Client, make sure the device is not behind a Firebox or connected to a DNSWatch protected network for accurate results.
- In your browser, go to test.strongarm.io.
- Confirm the correct block page appears.
If DNSWatch correctly blocks the test domain, you see this block page:
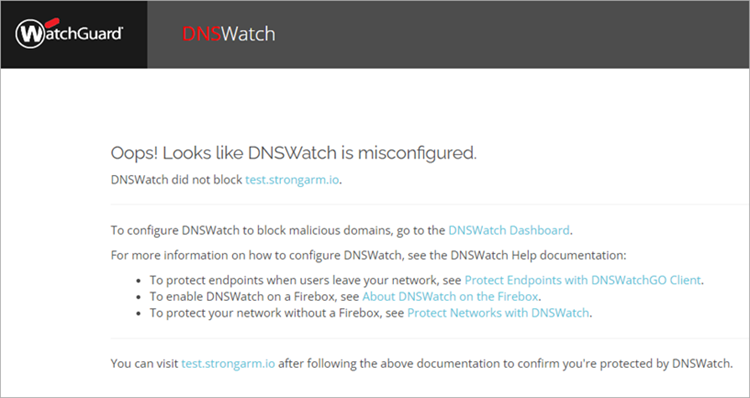
If DNSWatch does not operate correctly, you see this message:
Test DNSWatchGO Client
DNSWatchGO Client protects your devices when they are off your protected network.
To test the DNSWatchGO Client, follow the steps in the Verify DNSWatch Blocks Malicious or Filtered Content Domains section.
To gather the best data for the test, you should repeat the test scenarios on DNSWatchGO Client devices in a variety of locations. Some suggested locations:
- Home
- Active Directory controlled network
- Coffee shops
- Mobile hotspot
- On a network behind a firewall while connected with VPN
- Airport
- Airplane
- Hotels
It is important to test the client on networks that are not protected by DNSWatch on your Firebox or other DNSWatch enabled network.