Applies To: Locally-managed Fireboxes
You can enable network access enforcement for a mobile VPN connection to a locally-managed Firebox. Network access enforcement adds integrity checks that limit mobile VPN connections to devices that follow corporate policy.
When you enable network access enforcement, endpoint devices that try to connect to a Firebox mobile VPN must have WatchGuard Advanced EPDR, EPDR, EDR, EDR Core, or EPP installed.
Before an endpoint device can connect to the network, they must have these security settings:
- Devices with WatchGuard Advanced EPDR, EPDR, EDR, or EPP installed must have Advanced Protection enabled in hardening or lock mode, or antivirus enabled and running.
- Devices with WatchGuard EDR Core installed must have Advanced Protection enabled.
The WatchGuard Agent installed on the device collects and sends the information that the Firebox requires to verify that the device meets the necessary requirements. The WatchGuard Agent and Firebox verify that the device is associated with an account UUID specified in the Firebox network access enforcement settings and in the Network Services settings (Network Access Enforcement tab) of the Endpoint Security management UI. If the endpoint device does not meet these requirements, the Firebox rejects the connection.
How it Works
- An endpoint device tries to connect to the mobile VPN on the locally-managed Firebox.
- The Firebox allows the VPN connection, but initially allows only one-way VPN communication from the Firebox to the device.
- The Firebox connects to the device through the VPN over TCP port 33000.
- The Firebox verifies that the endpoint is associated with the account UUID specified in the Firebox network access enforcement settings and in the Network Services settings of the Endpoint Security management UI.
- The Firebox verifies that the endpoint device meets the operating system requirement (if specified).
Before You Begin
Before you configure network access enforcement:
- Verify operating system compatibility — Network access enforcement supports Windows, macOS, and Android operating systems. For information about mobile VPN operating system compatibility, go to the Operating System Compatibility Matrix section of the Fireware Release Notes. For information about WatchGuard Endpoint Security operating system compatibility, got to the Installation Requirements section of the WatchGuard Endpoint Security Release Notes.
- Configure at least one mobile VPN — The Firebox supports network access enforcement for all mobile VPN types. For more information, go to Select a Mobile VPN Type.
- Configure mobile VPN user groups — To enable network access enforcement, create mobile VPN user groups.
Network access enforcement requires a Firebox with a Total Security Suite license.
Configure Network Access Enforcement on the Locally-Managed Firebox
This step to configure network access enforcement on Fireboxes that run Fireware v12.9 and higher is required for the WatchGuard Agent to access the network.
In Fireware v12.5.4 to v12.8.2, Network Access Enforcement is called Endpoint Enforcement in the user interface.
- Select Subscription Services > Network Access Enforcement.

- Select the Enable Network Access Enforcement check box.
- Generate a random UUID for the account UUID.
Use a random UUID. UUID is an open format, with free tools available from vendors such as Microsoft or https://www.uuidgenerator.net/. We recommend you record this information before you proceed with the Network Access Enforcement configuration in Endpoint Security. - Add the Account UUID and an Authentication Key for the account:
- Click Add.
- Type the Account UUID.
- Type the TDR Authentication Key.
Use a long authentication key that includes uppercase, numeric, and special characters. We recommend you record this information before you proceed with the Network Access Enforcement configuration in Endpoint Security. - Click OK.
- Repeat this step to add up to 5 accounts.
- (Optional) From the Minimum Operating System Versions section, select requirements for Windows, macOS, or both.
- From the Windows drop-down list, select Windows 8.1, Windows 10, Windows 11, Any, or Custom.
- From the macOS drop-down list, select Catalina 10.15, BigSur 11.0, Monterey 12.0, Ventura 13.0, Any, or Custom.
If you select Any, endpoints can run any Windows or macOS operating system supported by WatchGuard. Endpoints can also run Android 6 or higher. For a list of supported operating systems, go to the Installation Requirements in the Endpoint Security Release Notes. Endpoints can also run Android 6 or higher. If you select Custom, enter a specific OS version number. You can enter up to three segments, separated by periods (for example, 13.3.1). You cannot enter letters.
- From the Windows drop-down list, select Windows 8.1, Windows 10, Windows 11, Any, or Custom.
- Click Save.
- When prompted to apply network access enforcement to groups, click OK.
- Select Subscription Services > Network Access Enforcement.

- Select the Enable Network Access Enforcement check box.
- Generate a random UUID for the account UUID.
You can use a random UUID. UUID is an open format, with free tools available from vendors such as Microsoft or https://www.uuidgenerator.net/. - Add an Account UUID and an Authentication Key.
- Click Add.
- Type the Account UUID.
- Type the TDR Authentication Key.
Use a long authentication key that includes uppercase, numeric, and special characters. - Click OK.
- (Optional) From the Minimum Operating System Versions drop-down list, select requirements for Windows, macOS, or both.
- From the Windows drop-down list, select Windows 8.1, Windows 10, or Any.
- From the macOS drop-down list, select High Sierra 10.13, Mojave 10.14, Catalina 10.15, or Any.
If you select Any, endpoints can run any Windows or macOS operating system supported by WatchGuard. Endpoints can also run Android 6 or higher. For a list of supported operating systems, go to the Installation Requirements in the Endpoint Security Release Notes.
- Click OK.
- When prompted to apply enforcement to groups, click OK.
Configure Network Access Enforcement for a Mobile VPN Group
You must now enable network access enforcement for a mobile VPN group. Users that are members of the mobile VPN group must meet the requirements from Before You Begin in this section.
For a user who belongs to multiple mobile VPN groups, enforcement applies to that user if:
- The mobile VPN groups are all part of the same mobile VPN configuration, and
- You enable network access enforcement for only some of those groups.
For example, if a user belongs to two mobile VPN with IKEv2 groups, but you enable enforcement for only one of those groups, enforcement applies to that user.
For a user who belongs to multiple groups that are part of different mobile VPN configurations, if network access enforcement is enabled for only some of the groups, enforcement applies to that user for only some types of mobile VPN connections. For example:
- If a user is part of the IKEv2-Users and SSLVPN-Users groups, and you enable enforcement only for IKEv2-Users, enforcement applies to that user only for mobile VPN with IKEv2 connections.
- Enforcement does not apply to that user for mobile VPN with SSL connections.
You cannot enable network access enforcement for individual mobile VPN users.
Mobile VPN with IKEv2
- Select VPN > Mobile VPN.
- In the IKEv2 section, click Configure.
- Select Authentication.
- From Users and Groups, select the check box next to a group.
- In the Network Access Enforcement column, select Yes.
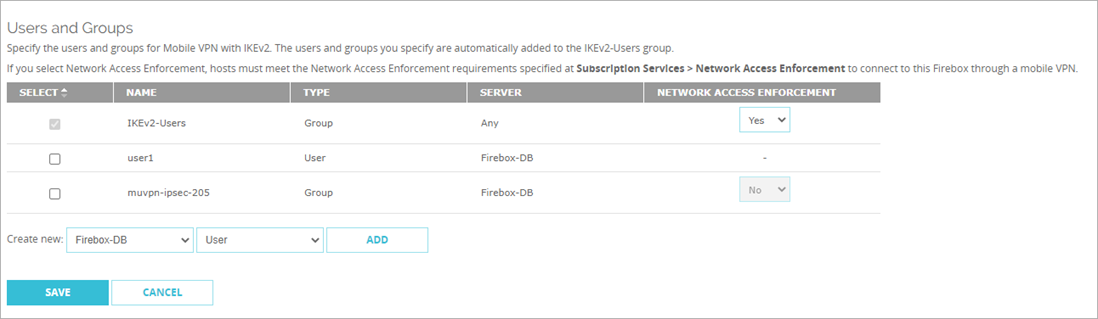
- Click Save.
- Select VPN > Mobile VPN > IKEv2.
- Select Authentication.
- From the left column, select the check box next to the group.
You can now change the Network Access Enforcement setting. - In the Network Access Enforcement column, select the check box for the group.
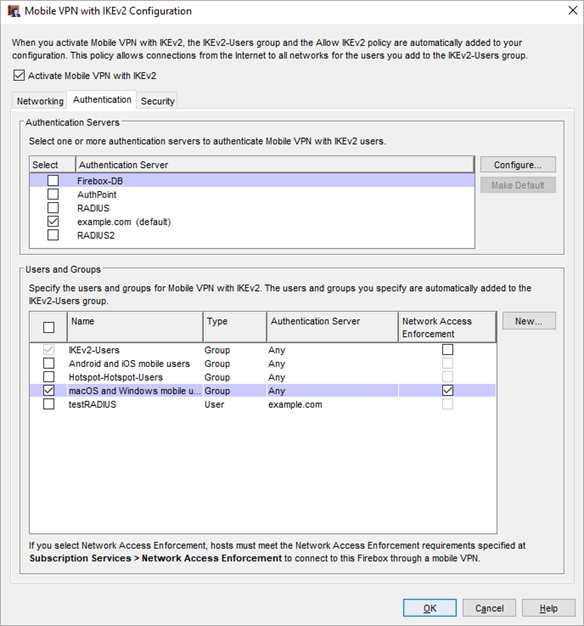
- Click OK.
Mobile VPN with L2TP
- Select VPN > Mobile VPN.
- In the L2TP section, click Manually Configure.
- Select Authentication.
- From Users and Groups, select the check box next to a group.
- In the Network Access Enforcement column, select Yes.

- Click Save.
- Select VPN > Mobile VPN > L2TP.
- Select Authentication.
- From the left column, select the check box next to the group.
You can now change the Network Access Enforcement setting. - In the Network Access Enforcement column, select the check box for the group.

- Click OK.
Mobile VPN with SSL:
- Select VPN > Mobile VPN.
- In the SSL section, click Configure.
- Select Authentication.
- From Users and Groups, select the check box next to a group.
- In the Network Access Enforcement column, select Yes.

- Click Save.
- Select VPN > Mobile VPN > SSL.
- Select Authentication.
- From the left column, select the check box next to the group.
You can now change the Network Access Enforcement setting. - In the Network Access Enforcement column, select the check box for the group.

- Click OK.
Mobile VPN with IPSec:
- To enable network access enforcement for Firebox-DB users, select Authentication > Servers > Firebox-DB.
Or, to enable network access enforcement for users on third-party authentication servers, select Authentication > Users and Groups. - Select a group and click Edit.
For Firebox-DB users, the Firebox Group authentication settings dialog box opens. For users on third-party authentication servers, the Edit User or Group dialog box opens. - Select the Enable Network Access Enforcement check box.

- Click OK.
- To enable network access enforcement for Firebox-DB users, select Setup > Authentication > Authentication Servers > Firebox-DB.
Or, to enable network access enforcement for users on third-party authentication servers, select Authentication > Users and Groups. - Select a group and click Edit.
For Firebox-DB users, the Firebox Group authentication settings dialog box opens. For users on third-party authentication servers, the Edit User or Group dialog box opens. - Select the Enable Network Access Enforcement check box.

- Click OK.
Enable Network Access Enforcement in Endpoint Security
After you enable and configure network access enforcement on the Firebox, you must configure network access enforcement settings in WatchGuard Endpoint Security.
- In WatchGuard Cloud, select Configure > Endpoints.
- Select Settings.
- From the left pane, select Network Services.

- Click Network Access Enforcement.
- Enable the Enable Network Access Enforcement toggle.

- In the Account UUID text box, type the UUID for the Firebox.
This UUID must be the same as the UUID you specify in the Firebox configuration. - In the Authentication Key text box, type the authentication key.
This must be the same as the authentication key you specify in the Firebox configuration. - Click Save Changes.