Applies To: Cloud-managed Fireboxes
To help prevent brute force attacks against the login pages of a cloud-managed Firebox, you can enable the Block IP Addresses with Consecutive Failed Logins feature. When this feature is enabled, the Firebox temporarily blocks an IP address after a specified number of consecutive failed authentication attempts to these Firebox login pages within the specified time period:
- Fireware Web UI
- Mobile VPN with SSL client download page
- Authentication Portal
The number of consecutive failed authentication attempts you enter is used for the total number of failed attempts to all login pages on the Firebox. For example, if you allow 5 failed authentication attempts and there are 2 failed authentication attempts to the Web UI and 3 failed authentication attempts to the Authentication Portal from the same IP address, the Firebox blocks the IP address.
This feature does not block failed login attempts for:
- The Fireware Web UI login page when the account user name is not admin or status
- AuthPoint authentication
The Firebox automatically adds the blocked IP address to a temporary blocked sites list. You cannot manage this list, but you can add a Blocked Site exception to allow a blocked IP address. For information about how to add an exception, go to Add Exceptions in WatchGuard Cloud.
This feature is supported in Fireware v12.10.4 and higher and is disabled by default.
To block consecutive failed login attempts, from WatchGuard Cloud:
- Select Configure > Devices.
- Select the cloud-managed Firebox.
- Click Device Configuration.
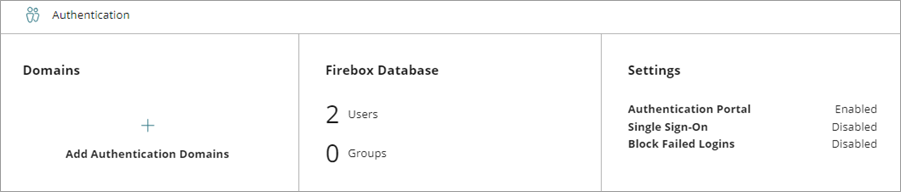
- From the Authentication section, click the Settings widget.
The Settings page opens.
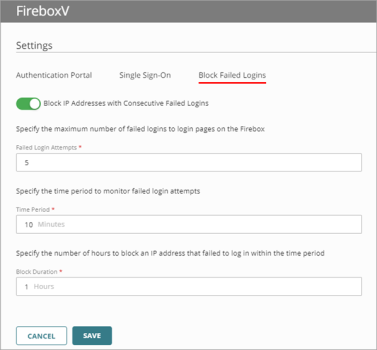
- Select the Block Failed Logins tab.
- Enable Block IP Addresses with Consecutive Failed Logins.
The Block IP Addresses with Consecutive Failed Logins settings appear.
- In the Failed Login Attempts text box, enter the number of consecutive failed login attempts that can occur before the Firebox temporarily blocks the source IP address.
The number that you enter is the total number of failed login attempts to all login pages on the Firebox. - In the Time Period text box, enter the number of minutes that the consecutive failed login attempts must occur in for the Firebox to block the IP address.
- In the Block Duration text box, enter the number of hours to block the IP address.
- Click Save.
- Deploy the configuration.
When the feature blocks a source IP address, Live Status > Traffic Monitor > Live Logs shows the IP address as blocked with reason = block failed logins.
About Firebox Authentication Settings
About Fireware Web UI for a Cloud-Managed Firebox
Download, Install, and Connect the Mobile VPN with SSL Client
Connect to the Firebox Authentication Portal