Applies To: Cloud-managed Fireboxes
You can configure a Branch Office VPN (BOVPN) from a cloud-managed Firebox to any Firebox or any third-party VPN endpoint that supports route-based IKEv2 VPNs with compatible settings. You can configure a BOVPN virtual interface to a third-party VPN endpoint or cloud-based endpoint. Supported endpoints include cloud-based virtual networks, such as Microsoft Azure, Amazon AWS, and Cisco VTI endpoints.
To configure a BOVPN between two cloud-managed Fireboxes in the same WatchGuard Cloud account, go to Configure a BOVPN Between Cloud-Managed Fireboxes.
When you configure the BOVPN, WatchGuard Cloud deploys the configuration to the cloud-managed Firebox. You must then configure the remote endpoint with the same settings.
When you add a BOVPN to a cloud-managed Firebox, you configure:
- VPN Gateways — The external networks the two devices use to connect.
- Credential method — Select one of two options:
- Pre-shared Key — A shared secret used to encrypt and decrypt data that goes through the tunnel. Use a key length of 20 or more characters.
- Certificate — An IPSec Firebox certificate used for tunnel authentication. For more information, go to Certificates for Branch Office VPN (BOVPN) Tunnel Authentication in Fireware Help.
- NAT — (Optional) When you create a Branch Office VPN (BOVPN) tunnel between two networks that use the same private IP address range, an IP address conflict occurs. To create a tunnel without this conflict, you can add NAT to the VPN. NAT creates a map from one or more IP addresses in one range to a second IP address range of the same size. Each IP address in the first range corresponds to an IP address in the second range.
- Network Resources — The networks that can send and receive traffic through the tunnel.
- Virtual IP Address — (Recommended) Required if you want to:
- Add the BOVPN to an SD-WAN action.
- Configure a zero-route BOVPN.
- Reply to Firebox-generated traffic through the tunnel. For example, DNS and DHCP traffic, Dimension, syslog, SNMP, NTP, authentication (Active Directory, LDAP, and RADIUS), and other connections established by the Firebox to resources through the tunnel.
- Enable Don't Fragment (DF) Bit Settings — (Optional) Control whether the Firebox uses the original DF bit setting in the header of a packet.
- Configure Tunnel MTU — (Optional) Use a custom maximum transmission unit (MTU).
- Security Settings — Authentication and encryption settings for VPN negotiation.
BOVPNs and Routing
In the BOVPN configuration, you specify what network resources are accessible through the BOVPN tunnel. The resources you select for one endpoint become static routes on the other endpoint, with the BOVPN as the gateway. The distance (metric) you specify for each resource appears in the routing table. The Firebox uses the routing table to determine whether to send traffic through the BOVPN tunnel.
If you want to specify network resources for both endpoints in the same subnet, you must use NAT. If you do not use NAT, you cannot route traffic through a BOVPN tunnel between private networks that use the same IP address range.
For a VPN between a Firebox and a locally-managed or third-party VPN endpoint:
- The network resources you specify for the remote endpoint specify what traffic the Firebox routes through the tunnel. These become static routes on the cloud-managed Firebox, with the BOVPN as the gateway.
- The network resources you specify for the Firebox are the resources that you want the remote endpoint to route through the VPN tunnel to the Firebox. The resources you specify here do not limit what traffic the Firebox accepts through the VPN tunnel. For the Firebox to receive VPN traffic to these resources, the remote endpoint must be configured to route traffic to these IP addresses through the tunnel.
Virtual IP Addresses
A virtual IP address is an IP address that is not tied to a physical interface. For a BOVPN in WatchGuard Cloud, which is a BOVPN virtual interface, a virtual IP address functions as the gateway (next hop). The virtual IP address is used for Firebox-generated traffic and response traffic sent directly to the BOVPN virtual interface.
While a virtual IP address is required only in certain scenarios, we recommend that you always configure a virtual IP address for a BOVPN. This configuration makes sure that traffic is routed through the tunnel as expected.
You must configure virtual IP address in these cases:
SD-WAN
Before you can add a BOVPN to an SD-WAN action, you must configure the BOVPN with /32 virtual IP addresses for both endpoints. BOVPN link monitoring is implicitly enabled when you configure /32 host IP addresses as the virtual IP address of both endpoints. A BOVPN that does not have link monitoring enabled (does not have valid /32 virtual IP addresses for both endpoints) is not available to select in an SD-WAN action.
For more information about SD-WAN, go to Configure SD-WAN.
Zero Routing
If you add a zero route BOVPN network resource (0.0.0.0/0), this creates a default route that sends all network traffic (including the traffic to WatchGuard Cloud) through the VPN tunnel. For a cloud-managed Firebox, you must enter virtual IP addresses in the BOVPN configuration so that return traffic uses the VPN tunnel.
Caution: If you add a zero route BOVPN network resource, and the remote VPN endpoint cannot route traffic from the cloud-managed Firebox to WatchGuard Cloud, you lose the ability to manage or monitor the Firebox.
Firebox-Generated Traffic
The Firebox itself generates traffic through the tunnel. Firebox-generated traffic is also known as self-generated traffic or self-originated traffic.
You must enter a /32 virtual IP address for each endpoint so that replies to Firebox-generated traffic use the VPN tunnel. Do not use the IP address elsewhere on the Firebox. You do not have to use an IP address from within the tunnel routes. Examples of Firebox-generated traffic include DNS and DHCP traffic, Dimension, syslog, SNMP, NTP, authentication (Active Directory, LDAP, and RADIUS), and other connections established by the Firebox to resources through the tunnel.
BOVPNs and Automatic Deployment
When you add, edit, or remove a BOVPN, the BOVPN configuration is automatically deployed for the cloud-managed Firebox to download. To make sure that the automatic deployment contains only BOVPN configuration changes, you cannot save BOVPN changes if the Firebox has other undeployed configuration changes.
Before you add, edit, or remove a BOVPN, make sure that the Firebox does not have undeployed changes.
Add a BOVPN Between a Cloud-Managed Firebox and a Locally-Managed Firebox or Third-Party VPN Endpoint
You can add a BOVPN from the BOVPN page for a specific Firebox, or you can add it from the VPNs page, which is a shared configuration page. For more information, go to Manage BOVPNs for Cloud-Managed Fireboxes.
To add a BOVPN to the cloud-managed Firebox, from WatchGuard Cloud:
- To open the BOVPN page, use one of these methods:
- To manage BOVPNs for all Fireboxes in the currently selected account, select Configure > VPNs.
- To manage BOVPNs for a specific Firebox, on the Device Configuration page, click the Branch Office VPN tile.
- From either BOVPN page, click the Branch Office VPN tile.
The BOVPN page shows currently configured BOVPNs.

- Click Add BOVPN.
The Add BOVPN page opens. - In the Name text box, type a name for this BOVPN.
- From the VPN Connection Type drop-down list, select Route-Based IPSec to Locally-Managed Firebox / Third-Party.
The content of the Endpoint B section changes from a list of Fireboxes to an Endpoint Name text box.
The Route-Based IPSec to Locally-Managed Firebox / Third-Party option was previously named Locally-Managed Firebox or Third-Party VPN Endpoint.
- From the Address Family drop-down list, select IPv4 Addresses or IPv6 Addresses.
If you select IPv6 Addresses, the other BOVPN endpoint must be configured to support IPv6.
You can also select Route-Based IPSec to Locally-Managed Firebox / Third-Party to create a BOVPN between Fireboxes in different WatchGuard Cloud accounts.
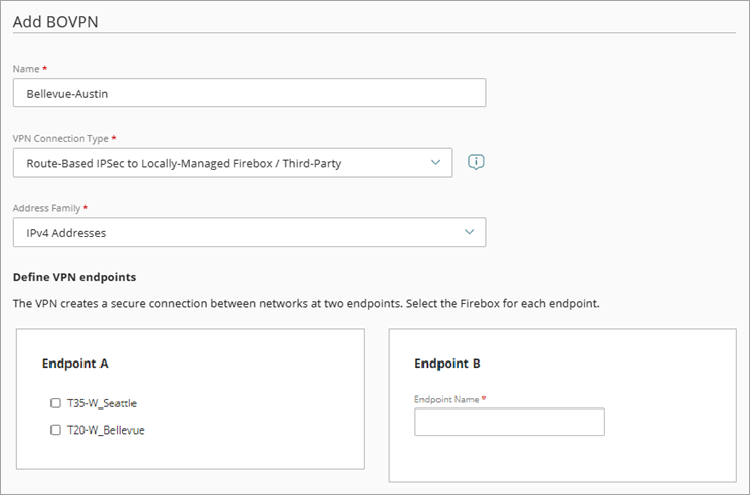
- In the Endpoint A section, select a cloud-managed Firebox in your account.
If you added the BOVPN from a Device Configuration page, the Endpoint A list contains only one Firebox. - In the Endpoint B section, in the Endpoint Name text box, type a name to identify the remote VPN endpoint.
The BOVPN configuration uses this name to refer to Endpoint B.

- Click Next.
The VPN Gateways settings page opens.

- To use an IPSec Firebox certificate for this VPN connection, select Use IPSec Firebox Certificate. To use a pre-shared key instead, go to Step 11.
A certificate list appears.

- Select a certificate.
- For the cloud-managed Firebox, select one external network.
- For this external network, specify the IP address in the drop-down list. Select the x500 name, domain name, or IP address. Available options depend on the certificate configuration.
For networks with an IP address configuration of DHCP or PPPoE, the default IP address is Any (Dynamic). - For the remote endpoint:
- In the IP Address drop-down list, select or enter an IP address.
- In the Endpoint ID text box, enter a x500 name, domain name, or IP address that resolves to the IP address of the remote endpoint.
- Click Next.
- To use a pre-shared key for this connection, for the cloud-managed Firebox, select one external network.
- Specify the IP address or a domain name that resolves to the Firebox external network IP address.
- For the remote endpoint, in the IP or Domain Name text box, type an IP address or a domain name that resolves to the IP address of the remote endpoint.
- In the Pre-shared key text box, type a pre-shared key to secure this VPN tunnel.
- Click Next.

- Select the Firebox internal and guest networks that you want to be accessible through the VPN tunnel.
- (Optional) To avoid conflicts when both networks use the same private IP address range, add NAT to an endpoint:
- Next to the cloud-managed endpoint you want to add NAT to, click Add NAT.
The Add NAT dialog box opens. - In the NAT text box, type an IP address and netmask for the NAT.

- Click Add.
The NAT information shows next to the network endpoint entry.
To remove a NAT IP address, edit the NAT text box to be empty and click Save.
- Next to the cloud-managed endpoint you want to add NAT to, click Add NAT.
- To add a network resource other than internal or guest networks:
- In the section for the Firebox resources, click Add Network Resource.
The Add Network Resource dialog box opens.
- In the Network Resource text box, type the network IP address and netmask.Tip!
- In the Distance text box, enter a value between 1 and 254. Routes with lower metrics have higher priority. The default is 1. In Fireware v12.9 or higher, the Distance setting replaces the Metric setting.
- (Optional) To add NAT to a network resource:
- Click Add NAT.
- In the NAT text box, type an IP address and netmask for the NAT.
The netmask used in the NAT text box must match the netmask of the network resource.
- Click Add NAT.
- Click Add.
The network resource is added to the Traffic settings for the endpoint.
- In the section for the Firebox resources, click Add Network Resource.
- Add a network resource for the remote endpoint:
- In the section for the second endpoint, click Add Network Resource.
- In the Network Resource text box, type the network IP address and netmask.
- In the Distance text box, enter a value between 1 and 254. Routes with lower metrics have higher priority. The default is 1. In Fireware v12.9 or higher, the Distance setting replaces the Metric setting.
- Click Add.
The network resource is added to the Traffic settings for the endpoint.
- Repeat the previous step to add other network resources.
- (Recommended) For each endpoint, in the Virtual IP Address text box, type an IP address. A virtual IP address is an IP address that is not tied to a physical interface. For a BOVPN in WatchGuard Cloud, which is a BOVPN virtual interface, a virtual IP address functions as the gateway (next hop). The virtual IP address is used for response traffic sent directly to the BOVPN virtual interface.
Virtual IP addresses are required in some cases:
- Before you can add this BOVPN to an SD-WAN action, you must specify virtual IP addresses with a /32 netmask.
- If you configure a zero-route BOVPN, you must enter virtual IP addresses so that return traffic uses the VPN tunnel. If you add a zero route BOVPN network resource, and the remote VPN endpoint cannot route traffic from the cloud-managed Firebox to WatchGuard Cloud, you lose the ability to manage or monitor the Firebox.
- For Firebox-generated traffic, virtual IP addresses are required so those response traffic uses the VPN tunnel. Examples of Firebox-generated traffic include DNS and DHCP traffic, Dimension, syslog, SNMP, NTP, authentication (Active Directory, LDAP, and RADIUS), and other connections established by the Firebox to resources through the tunnel.

- (Optional) For the cloud-managed endpoint, you can select Enable Don't Fragment (DF) Bit Settings. The DF bit is a flag in the header of a packet. This setting controls whether the Firebox uses the original DF bit setting in the header of a packet.

From the Enable Don't Fragment (DF) Bit Settings drop-down list, select one of these options:
Copy
Copies the original DF bit setting of the IPSec packet to the encapsulating header.
If a frame does not have the DF bits set, the Firebox does not set the DF bits and fragments the packet as it needs to. If a frame is set to not be fragmented, the Firebox encapsulates the entire frame and sets the DF bits of the encrypted packet to be the same as the original frame.
Set
The Firebox cannot fragment IPSec packets, regardless of the original bit setting.
If you must make IPSec connections to a Firebox from behind a different Firebox, do not select this option if you want to enable the IPSec pass-through feature.
Clear
The Firebox can fragment IPSec packets, regardless of the original bit setting.
This option breaks the frame into pieces that can fit in an IPSec packet, regardless of the original bit setting.
If you do not specify a DF bit setting for the endpoint, the endpoint uses the DF bit setting that the external interface settings specify.
- (Optional) For the cloud-managed Firebox, type a custom maximum transmission unit (MTU) in the Configure Tunnel MTU text box. The default MTU value of the option is 1400 bytes. The MTU specifies the largest data packet, measured in bytes, that a network can transmit. You might want to specify a custom MTU if the endpoint connects to a third-party VPN endpoint that drops packets that exceed a certain size.

- Click Next.
The Security settings page opens.

- Accept the default security settings, or edit them to match settings supported by the remote VPN endpoint. For information, go to Configure BOVPN Security Settings. For information about BOVPN throughput, go to Optimize BOVPN Throughput.
- Click Add.
The BOVPN deployment is added, and the BOVPN Guide page opens.

- To open the BOVPN Guide in a new browser tab, click View Guide.
The BOVPN Guide with opens in a new browser tab. You can print this page or save it to a PDF. - To return to the BOVPN list, click Finish.
View the BOVPN Guide
For each BOVPN, WatchGuard Cloud generates a VPN Guide that summarizes the VPN configuration settings required on the remote VPN endpoint. You can view the BOVPN Guide from the Edit BOVPN page. For more information, go to View the BOVPN Guide.
Configure the Remote VPN Endpoint
On the remote VPN endpoint, add a route-based IKEv2 VPN with settings that match the VPN settings on the cloud-managed Firebox. For more information, go to Configure Remote VPN Endpoint Settings on a Locally-Managed Firebox or Third-Party VPN Endpoint.
Edit or Delete a BOVPN
You can edit or delete a BOVPN from the BOVPN page. For information, go to Manage BOVPNs for Cloud-Managed Fireboxes.
Manage Device Configuration Deployment