Applies To: Cloud-managed Fireboxes
In a firewall policy for a cloud-managed Firebox, you specify the source and destination of the connections the policy applies to. A connection must match both the source and destination for the policy to apply to that traffic. For a Custom policy, you also specify the traffic direction the policy applies to.
You can add these types of addresses as a policy source or destination:
- Aliases — Custom and built-in aliases, including template aliases
- Firebox Networks — The name of a Firebox network, such as Internal or External
- Firebox DB Group — A group in the Firebox database
- Firebox DB User — A user in the Firebox database
- Group — A group in an Authentication Domain
- User — A user in an Authentication Domain
- Host IPv4 — The IPv4 address of a host
- Network IPv4 — The IPv4 address of a network
- Host Range IPv4 — A range of IPv4 addresses
- Host IPv6 — The IPv6 address of a host
- Network IPv6 — The IPv6 address of a network
- Host Range IPv6 — A range of IPv6 addresses
- FQDN — A fully qualified domain name, such as *.example.com
- SAML Group — A group in a SAML Authentication Domain
- SAML User — A user in a SAML Authentication Domain
For an inbound policy, you can also add a static NAT action as a policy destination. Static NAT (SNAT), also known as port forwarding, is a port-to-host NAT. You must add the static NAT action before you can add it as a policy destination. For more information, see Configure Firebox Static NAT Actions.
For more information about custom and built-in aliases, see Configure Firebox Aliases.
A custom alias can be inherited from a template. When an alias is inherited from a template, it displays a TEMPLATE label beside the alias name.
For more information about Firebox DB users and groups, see Configure Firebox Database User Authentication.
Before you can add an authentication domain user or group, you must add the authentication domain to WatchGuard Cloud, and then add it to the Firebox configuration. For more information, see:
- Add or edit a policy. For more information, see Configure Firewall Policies in WatchGuard Cloud.
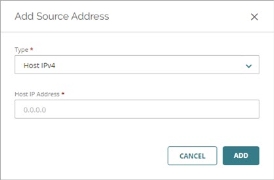
- In the Source and Destination settings of the policy, click Add Source.
The Add Source Address dialog box opens.
- From the Type drop-down list, select the type of address to add.
- Type or select the address.
- Click Add.
- Repeat these steps to add any additional source addresses.
- Add or edit a policy. For more information, see Configure Firewall Policies in WatchGuard Cloud.
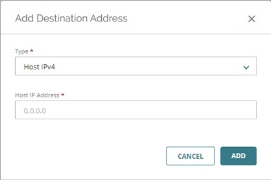
- In the Source and Destination settings of the policy, click Add Destination.
The Add Destination Address dialog box opens.
- From the Type drop-down list, select the type of address to add.
- Type or select the address.
- Click Add.
- Repeat these steps to add any additional destination addresses.
A Custom policy is appropriate for traffic between two private networks. For example, if your Firebox has two internal networks, you could add a Custom policy that applies to connections between hosts on the two networks.
All other firewall policy types apply only to connections from a source to a destination. A Custom policy can also apply to connections from the destination to the source.
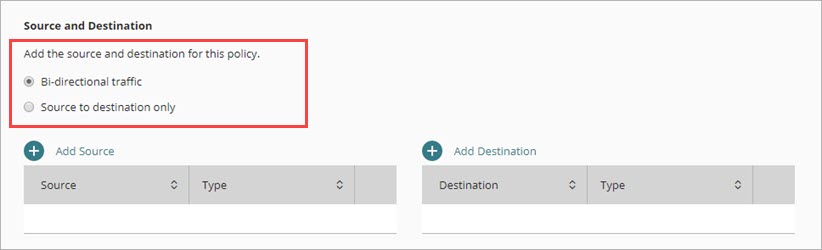
In a Custom policy, select one of these options.
Bi-directional traffic (default)
Select this option if you want the policy to apply to connections between the source and destination regardless of which started the connection.
Source to destination only
Select this option if you want the policy to apply only to connections from a policy source to a policy destination.