Applies To: Cloud-managed Fireboxes
For firewall policies on a cloud-managed Firebox, the Web Traffic and Traffic Types settings specify the types of traffic the policy applies to. When you add traffic types to a policy, you can select from a list or add a custom traffic type. Each traffic type specifies the protocols and ports the policy applies to.

Configure Web Traffic Settings
In Outbound policies, two settings specify how the policy applies to web traffic:
Web Traffic
This setting configures the policy to apply to HTTP and HTTPS traffic on specified ports. By default, this check box is selected, and the policy applies to HTTP and HTTPS traffic on ports 80 and 443. To change the ports for HTTP and HTTPS traffic, you can edit the ports list.
When Web Traffic is selected, the policy applies to HTTP and HTTPS traffic but the HTTP and HTTPS protocols do not show in the Traffic Types list.
HTTP and HTTPS traffic are strictly enforced when Web Traffic is selected. To avoid denials, you must create a First Run policy to allow other traffic sent over ports 80 and 443.
Decrypt HTTPS Traffic
This setting configures the policy to decrypt HTTPS traffic. When you select Decrypt HTTPS Traffic, the Firebox decrypts HTTPS connections and scans the content with enabled security services. If the policy allows the content, the Firebox then re-encrypts the HTTPS connections with a different certificate.
Before you enable Decrypt HTTPS Traffic, make sure that network clients trust the certificate the Firebox uses to re-encrypt the content. To avoid browser errors for network clients, download the Firebox certificate and import it to all network clients. For more information, go to Download the Certificate for TLS Decryption.
To avoid certificate warnings for network users, Decrypt HTTPS Traffic is disabled by default.
When you select Decrypt HTTPS Traffic on a web traffic policy, you can enable and configure these features:
- SafeSearch Enforcement — Use the SafeSearch feature of web browser search engines to specify the level of potentially inappropriate content a search engine can return. For more information, go to SafeSearch Enforcement in WatchGuard Cloud.
- Google Apps Allowed Domains — Specify which domains are allowed for Google services. For more information, go to Google Apps Allowed Domains in WatchGuard Cloud.
- Fastvue — Use Fastvue to gain visibility into your network traffic, web usage, and user activity. For more information, go to Fastvue in WatchGuard Cloud.
- URL Path Keyword Filtering — Block websites with URL paths that contain the text you specify. For more information, go to URL Path Keyword Filtering in WatchGuard Cloud.
- Add or edit a policy. For more information, go to Configure Firewall Policies in WatchGuard Cloud.
- To apply a policy to web traffic, select the Web Traffic check box.
When selected, the policy applies to HTTP and HTTPS web traffic on ports 80 and 443 by default.
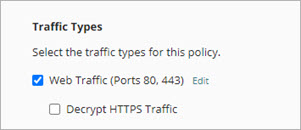
- To change the ports where web traffic is allowed for this policy, click Edit.
The Edit Web Traffic Ports page opens.
- To add a port for HTTP and HTTPS web traffic:
- Click Add Another Port.
A new text box appears in the ports list. - In the text box, type the port number to add.
- Click Add Another Port.
- To remove a port for web traffic, click
 .
. - Click Update.
- To decrypt HTTPS traffic, select the Decrypt HTTPS Traffic check box. For security services to scan HTTPS traffic, you must select this check box.
- To enforce SafeSearch in web browser search engines, enable SafeSearch Enforcement. For more information, go to SafeSearch Enforcement in WatchGuard Cloud.
- To restrict Google apps to allowed domains, enable Google Apps Allowed Domains. For more information, go to Google Apps Allowed Domains in WatchGuard Cloud.
- To integrate with Fastvue for monitoring and reporting, enable Fastvue. For more information, go to Fastvue in WatchGuard Cloud.
- To allow or deny traffic to websites that have specific keywords in the URL path, enable URL Path Keyword Filtering. For more information, go to URL Path Keyword Filtering in WatchGuard Cloud.
To configure a First Run, Last Run, Inbound, or Custom policy to apply to web traffic, add the HTTP and HTTPS traffic types to the Traffic Types list.
Select Traffic Types in a Policy
In the Traffic Types list for a firewall policy you can add predefined and custom traffic types.
In a firewall policy for a cloud-managed Firebox, you can select multiple traffic types in the same policy. This is different from firewall policies for a locally-managed Firebox.
- Add or edit a policy. For more information, go to Configure Firewall Policies in WatchGuard Cloud.
- In the policy configuration, click Add Traffic Types.
The Add Traffic Types page opens.
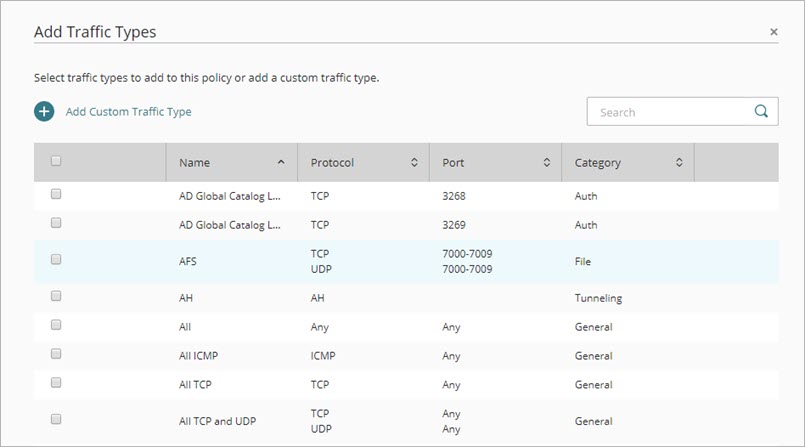
- Select the check box for each traffic type to add.
- Click Add.
The traffic types you selected are added to the policy.
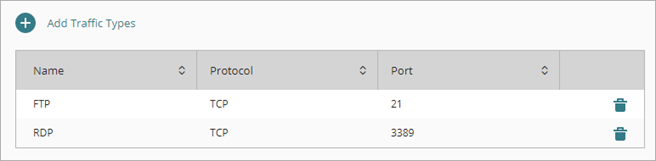
To apply a policy to a traffic type that is not on the list, you can add a new custom traffic type. When you add a custom traffic type, you select one or more protocols. For each protocol, you specify ports or other parameters that define traffic for the protocol. After you add a custom traffic type to one policy, the custom traffic type is available to select in other policies.
- In the policy configuration, click Add Traffic Types.
The Add Traffic Types page opens. - Click Add Custom Traffic Type.
The Add Custom Traffic Type page opens.
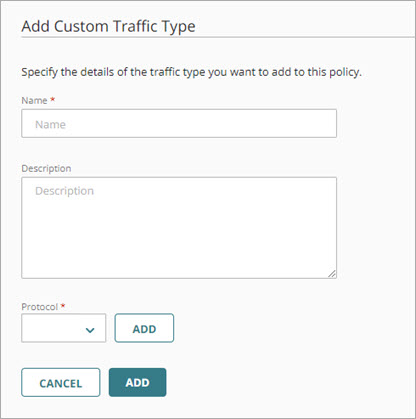
- In the Name text box, type a name for the custom traffic type.
- In the Description text box, type a description for the custom traffic type.
- To add a protocol:
- From the Protocol drop-down list, select the protocol to add.
The Type settings change based on the protocol you select. - If required for the selected protocol, select the Type and specify other settings.
- Click Add.
The protocol is added to the custom traffic type.
- From the Protocol drop-down list, select the protocol to add.
- To add another protocol, repeat the previous step.
- To remove a protocol from the custom traffic type, click
 .
. - To save the custom traffic type, click Add.
The traffic type is added to the current policy and to the global Traffic Types list.
If you edit a custom traffic type, the change affects all policies that reference it. You cannot delete a custom traffic type if the current policy or any other policy reference it.
To edit a custom traffic type:
- In the policy configuration, click Add Traffic Types.
The Add Traffic Types page shows all predefined and custom traffic types. - To filter the list to view only custom traffic types, in the search box, type Custom.
- To edit the custom traffic type, click the Name.
The custom traffic type settings page opens. - Edit the traffic type settings.
- To save the changes, click Update.
To delete a custom traffic type:
- In the policy configuration, click Add Traffic Types.
The Add Traffic Types page shows all predefined and custom traffic types. - To filter the list to view only custom traffic types, in the search box, type Custom.
- To delete a custom traffic type, click
 .
.
The Delete a Traffic Type dialog box opens. - Click Delete.
Configure Firewall Policies in WatchGuard Cloud
SafeSearch Enforcement in WatchGuard Cloud
