Applies To: Cloud-managed Fireboxes
For a cloud-managed Firebox, default Core policies allow outbound connections from internal and guest networks to external networks.
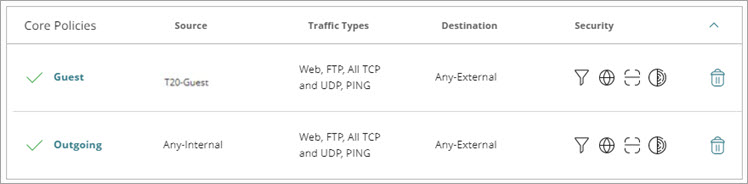
When you add a cloud-managed Firebox to WatchGuard Cloud, two default Core policies are automatically added to the configuration.
Outgoing
This Outbound policy allows connections from internal networks to external networks and also enables all security services.
Default policy settings:
- Source — Any-Internal (a built-in alias for all internal networks)
- Traffic Types — Web, FTP, All TCP and UDP, Ping
- Decrypt HTTPS Traffic — Disabled
- Destination — Any-External (a built-in alias for all external networks)
- Security Services — All security services are enabled
Guest
This Outbound policy allows connections from the guest network to external networks and also enables all security services. The Guest policy does not allow users on the guest network to connect to internal networks.
Default policy settings:
- Source — Guest network
- Traffic Types — Web, FTP, All TCP and UDP, Ping
- Decrypt HTTPS Traffic — Disabled
- Destination — Any-External (a built-in alias for all external networks)
- Security Services — All security services are enabled
You can edit these policies or create your own. For best practices, see Firewall Policies Best Practices.
The Firebox also has System policies, which are not editable, and are hidden by default. For more information, see System Firewall Policies.