Applies To: ThreatSync+ NDR, ThreatSync+ SaaS
ThreatSync+ policies detect vulnerabilities and threats in your network and generate policy alerts if unauthorized activity is detected. We recommend you tune your policies to reduce the number of alerts you receive for activity that does not violate your organizational policies. This makes sure that you have a smaller number of alerts to review that reflect real concerns and that might require action.
To minimize your response time and maximize your protection, it is important to configure and tune your policies to:
- Reflect the security policies of your organization.
- Apply policies only to parts of your network that your organizational policies govern.
- Reflect the appropriate severity for your organization.
Ransomware Prevention Policies
We recommend you start with the subset of 33 policies that are included in the Ransomware Prevention Defense Goal Report. These policies protect against very common threats.
We recommend you enable these Ransomware Prevention Defense Goal policies:
| Policy Name | Recommendations |
|---|---|
|
Unsecured Outbound Telnet Traffic |
Replace outbound Telnet with SSH or other secure service. Exclude sites that cannot convert to a secure protocol from the destination zone. |
|
Unsecured Outbound FTP/TFTP Traffic |
Replace outbound FTP/TFTP with SFTP or other secure service. Exclude sites that cannot convert to a secure protocol from the destination zone. |
|
Unsecured Outbound IRC Traffic |
If users are authorized to use IRC to external sites, we recommend you deactivate this policy. If limited sites are authorized, exclude those sites from the destination zone. |
|
Active Directory to External |
Limit outbound traffic from Domain Controllers to authorized protocols. If there are additional protocols that are authorized, add these to the policy Activity Triggers. |
|
Activity to Blocked Countries |
If your firewall blocks activity to specific countries, use this policy to confirm that this protection is in place. Align the country list in the destination zone with your firewall rules. |
|
Outbound SMB Traffic |
Do not allow SMB traffic to exit the enterprise. If there are Windows servers external to the network, encrypt traffic to the servers through a secure tunnel. If these secured destinations have public addresses, apply the Internal label to the IP addresses. If other applications use the Microsoft SMB ports, you can exclude those authorized sites from the destination zone. |
|
Unauthorized Outbound SSH |
If users are authorized to use SSH to external sites, we recommend you deactivate this policy. If limited sites are authorized, exclude those sites from the destination zone. |
|
Outbound NetBIOS Traffic |
Do not allow NetBIOS traffic to exit the enterprise. If there are Windows servers external to the network, encrypt the traffic to the servers through a secure tunnel. If these secured destinations have public addresses, apply the Internal label to the IP addresses. If other applications use the Microsoft NetBIOS ports, you can exclude those authorized sites from the destination zone. |
|
Suspected Data Exfiltration through DNS |
Data can be exfiltrated through DNS tunnels. This policy detects large amounts of traffic over DNS. Exclude internal DNS servers from this policy because they can query or synchronize larger amounts of data to the Internet. Verify that DNS servers are correctly labeled with the DNS role. If other applications are involved in authorized DNS activity, excluded them from the source zone. |
|
Beaconing Through Web API |
Periodic activity to popular websites might indicate automated tunneling of data through those sites. Hackers might use sites like WhatsApp to exfiltrate data. If authorized applications move data in a similar way, exclude them from the source zone. |
|
WUDO Traffic Crossing Network Boundary |
WUDO is the protocol used by Microsoft to update the Windows operating system from peer computers. We do not recommend the use of WUDO because it does not provide centralized control over what updates are authorized to be installed. WUDO access to devices on the Internet can be very dangerous and is not recommended. This can be configured through group policies in your Windows Domain. If you allow WUDO access to microsoft.com, you can exclude it from your destination zone. Only deactivate this policy if you have no control over how your devices are updated. |
|
Anomalous Activity to Blocked Countries |
If your firewall blocks activity to specific countries, use this policy to confirm that this protection is in place. Align the country list in the destination zone with your firewall rules. |
|
NetBIOS-NS Traffic Crossing Network Boundary |
Do not allow NetBIOS-NS traffic to exit the enterprise. Encrypt traffic to Windows servers external to the network through a secure tunnel. If these secured destinations have public addresses, apply the Internal label to the IP addresses. If other applications use the Microsoft NetBIOS-NS ports, you can exclude those authorized sites from the destination zone. |
|
LLMNR Traffic Crossing Network Boundary |
Do not allow LLMNR traffic to exit the enterprise. If other applications use the LLMNR ports, you can exclude those authorized sites from the destination zone. |
|
Unexpected DNS Resolution Server |
DNS requesters should query local DNS servers. Devices that access DNS servers external to the enterprise might be misconfigured or run unauthorized software. The policy excludes local DNS servers that connect to public DNS servers. If alerts include local DNS servers that connect to the Internet, they might not be correctly labeled with the DNS role. If devices use public DNS servers, they might not be configured correctly. Exclude devices that are authorized to use public DNS servers from the source zone. |
|
Unsecured Inbound Telnet Traffic |
Limit inbound services like Telnet to communication with specific servers within the DMZ. Exclude authorized internal or DMZ resident sites from the destination zone. Replace inbound Telnet with SSH or other secure service. |
|
Unsecured Inbound IRC Traffic |
Limit inbound services like IRC to communication with specific servers within the DMZ. Exclude authorized internal or DMZ resident sites from the destination zone. |
|
Unsecured Inbound FTP/TFTP Traffic |
Limit inbound services like FTP or TFTP from communication with specific servers within the DMZ. Exclude authorized internal or DMZ resident sites from the destination zone. Replace inbound Telnet with SFTP or other secure service. |
|
Activity from Blocked Countries |
If your firewall blocks inbound activity from specific countries, use this policy to confirm that this protection is in place. Align the country list in the source zone with your firewall rules. |
|
RDP Connection from New External Host |
Investigate or secure incoming RDP connections. Employees that connect to the enterprise must use a VPN. If an authorized RDP server is in place and it cannot be placed behind a VPN, consider excluding the server from the destination zone, or excluding the authorized requesters from the source zone. |
|
RDP Attempts from External to Internal |
Investigate or secure incoming RDP connections. Employees that connect to the enterprise should use a VPN. If an authorized RDP server is in place and it cannot be placed behind a VPN, consider excluding the server from the destination zone, or excluding the authorized requesters from the source zone. |
|
SSH Attempts from External to Internal |
Investigate or secure incoming SSH connections. Employees that connect to the enterprise should use a VPN. If an authorized SSH server is in place and it cannot be placed behind a VPN, consider excluding the server from the destination zone, or excluding the authorized requesters from the source zone. |
|
Connection From New External Domain to Internal |
Incoming connections to the enterprise must be expected. An incoming session from a new domain generates this alert. If authorized servers are in place that accept connections from new requesters, consider excluding the server from the destination zone. |
|
Unexpected Inbound Connection |
This broad policy generates alerts the first time any session is initiated from an external device. If you have servers that allow incoming connections from any location, exclude those servers from the destination zone. If you want to generate alerts only for specific countries or domains, configure that in the source zone. |
|
Unsecured Inbound Web Server Activity |
Web Servers exposed to the Internet must be secure and only receive traffic on secured ports such as HTTPS 443. If you must have an HTTP 80 server open on the Internet, you can exclude it from the destination zone so this policy only generates alerts for other devices. |
|
Anomalous Activity from Blocked Countries |
If your firewall blocks inbound activity from specific countries, use this policy to confirm that this protection is in place. Align the country list in the source zone with your firewall rules. |
|
Unsecured Internal Telnet Traffic |
Telnet is not a secure protocol because it transmits all user content in plain text. Reconfigure servers within the enterprise that allow Telnet connections to require a secure protocol, such as SSH or STelnet. If this is not a concern, you can deactivate this policy. We recommend that you exclude devices that are authorized to accept Telnet connections from the destination zone. |
|
Internal NetBIOS-NS Traffic |
NetBIOS-NS is a legacy protocol that is no longer necessary, unless older Windows servers still run in your network and you cannot upgrade them. We recommend you upgrade old Windows servers and configure clients to not use NetBIOS-NS. Exclude authorized servers that you cannot upgrade from the destination zone. |
|
Internal LLMNR Traffic |
LLMNR is a legacy protocol that should no longer be in use. If you require this protocol on your network, deactivate the policy. |
|
Unsecured Internal FTP/TFTP Traffic |
FTP and TFTP are not secure protocols. Reconfigure servers that allow FTP connections to require a secure protocol such as SFTP. If this is not a concern, consider deactivation of the policy. We recommend that you exclude devices that are authorized to accept FTP connections from the destination zone. |
|
Unsecured Internal Web Server Activity |
HTTP is not a secure protocol. Reconfigure servers that allow HTTP connections to require a secure protocol such as HTTPS. If this is not a concern, we recommend that you deactivate the policy. We recommend that you exclude devices that are authorized to accept HTTP connections from the destination zone. If your network has considerable unauthorized activity on other HTTP ports, such as 8080, that you want to identify and stop, we recommend you add those to the Activity Trigger filters. |
|
Internal WUDO Traffic |
WUDO is the protocol used by Microsoft to update the Windows operating system from peer computers. WUDO is not recommended because it does not provide centralized control over what updates are authorized to be installed. WUDO access to rogue devices within your network could result in the installation of malware. If you do allow the use of WUDO inside your network, you can limit the source and destination zones to only those the trusted servers and workstations, and exclude subnets like guest Wi-Fi. Only deactivate this policy if you have no control over how your devices are updated. |
|
Unsecured Internal IRC Traffic |
IRC is a chat protocol that is not commonly used. If you have authorized IRC servers in your network, you can exclude them from the destination zone. If this is not a concern, we recommend that you deactivate this policy. |
After you activate these policies, we recommend you review the controls in the Ransomware Prevention Defense Goal Report and disable controls that do not have activated policies. For more information, go to Ransomware Prevention Defense Goal Report.
Tuning Steps
We recommend you tune policies to reduce the number of alerts you receive for activity that does not violate your organizational policies.
To tune your policies, review and perform these tasks:
- Deactivate a Policy
- Exclude Devices
- Customize Zones Based on Roles or Tags
- Filter Policies by Traffic Properties
- Filter Policies by Anomalous Events
Deactivate a Policy
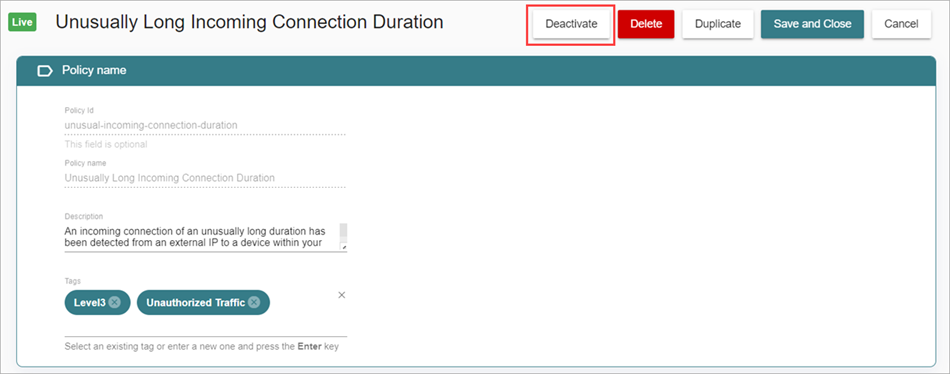
When a ThreatSync+ NDR policy is not relevant to your organization, you can deactivate it. We recommend you deactivate policies that generate alerts for activity that is authorized in your organization.
You can deactivate a policy from these pages:
- Manage Policies
- Policy Details
- Policy Alerts
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Policies.
- Next to the policy you want to deactivate, click Live.
The policy status changes to Not Active.

- Log in to your WatchGuard Cloud account.
- Select Monitor > ThreatSync+ > Policy Alerts.
- Click the policy name of the policy you want to deactivate.
The Policy Details page opens. - On the Policy Details page, click Deactivate.
Exclude Devices
Most networks have a limited number of devices that are authorized to perform specific types of activity.
For example, you might not allow external file sharing for the majority of your users and devices, but authorize specific users to connect to a specific service, such as Dropbox. In this example, you might want to generate alerts when any user connects to a file sharing service other than Dropbox, but do not want to generate alerts when authorized users connect to Dropbox.
To prevent policy alerts for authorized activity, you can exclude a device from the source or destination zone.
- Log in to your WatchGuard Cloud account.
- Select Monitor > ThreatSync+ > Policy Alerts.
- Click the policy you want to update.
The Policy Details page opens. - On the Policy Charts tab, in the Distribution of Policy Alerts by Source chart, or the Distribution of Policy Alerts by Destination chart, click the chart and select Exclude From Policy.
The Add Policy Exception dialog box opens.
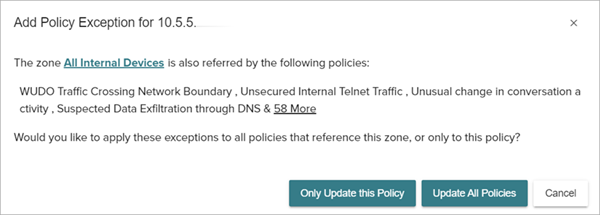
- To only apply the policy exception to the selected policy, click Only Update this Policy.
- To apply the policy exception to all policies, click Update All Policies.
- Select Monitor > ThreatSync+ > Policy Alerts.
- Click the policy you want to update.
The Policy Details page opens. - On the Alerts tab, click
 next to the zone you want to exclude from your policy.
next to the zone you want to exclude from your policy.
The Add Policy Exception dialog box opens. - To only apply the policy exception to the selected policy, click Only Update this Policy.
- To apply the policy exception to all policies, click Update All Policies.
On the Alerts tab, you can exclude only the type of zone object that the policy is configured to show. For example, if the policy shows devices, the exclusion is saved as the device name. If the policy shows domains, the exclusion excludes all devices that are in that domain.
To change the zone object that the policy is configure to show, edit the Display Alerts By zone object. For more information, go to Manage ThreatSync+ Zones.
Customize Zones Based on Roles or Tags
You can set up your policies to exclude an entire class of devices, rather than specific, static device names or addresses. This can be all the devices on a specific subnet or within a specific IP address range, or all devices with a specific role.
ThreatSync+ NDR enables you to assign roles to devices and assign tags to devices and subnets, so that when these groups of devices change, you do not have to update your policies.
To modify zone rules to include or exclude sets of devices based on roles or tags:
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Zones.
The Manage Zones page opens. - On the Manage Zones page, click
 next to the zone you want to edit.
next to the zone you want to edit.
The Edit Zone page opens with the Manage tab selected by default. - In the Zone Definition section, click Add Rule.
The Create Rule dialog box opens. - From the drop-down list, select Devices.
- Select Include or Exclude.
- If you select the Device by Role tab, select one or more roles.
- If you select the Device by Tag tab, enter one or more tags.
- Click Add.
Filter Policies by Traffic Properties
You can tune policy filters to limit the alerts that are generated. When a policy alert is based on network traffic, you can update the policy so that it only applies to traffic with specific properties.
To filter policies by traffic properties:
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Policies.
The Manage Policies page opens. - To tune an existing policy, select
 next to the policy you want to tune.
next to the policy you want to tune.
The Policy Details page opens. - Click Activity triggers to expand the section.
- In the Activity Triggers section, select Traffic.
- Select Alert on specific traffic.
- Next to Alert when, from the drop-down list, select All or Any to set the alert properties.
- Select Conversation, Port, or Volume to filter your traffic.
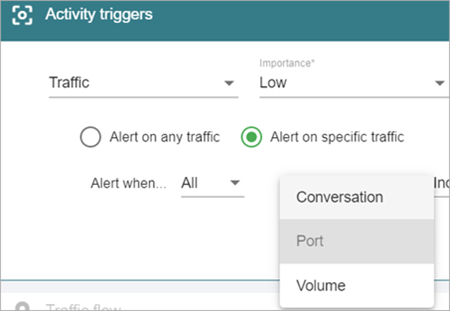
- To add another traffic filter, click Add Filter.
Conversation
Conversation describes the type of traffic. Possible values are:
-
ICMP Normal — ICMP Ping traffic with responses
-
ICMP Scanning — ICMP Ping traffic without responses
-
ICMP Unknown — ICMP Ping traffic that does not conform to a valid request or request/respond pair
-
TCP Normal — Fully formed TCP sessions with data
-
TCP Scanning — The start of TCP session that is never set up
-
TCP Malformed — TCP session fragments that are not well-formed
-
UDP One-Way — Well-formed UDP traffic that is not responded to
-
UDP Two-Way — UDP Request or Response traffic
-
UDP Malformed — UDP fragments that are not well-formed
-
UDP — Any type of UDP traffic
Traffic flows that are labeled with the selected conversation classes generate alerts.
Port
Port filters enable you to filter on the application port of a conversation. This is the destination port in the request traffic flows and the source port in the response traffic flows.
Valid values are 1 to 65535 for TCP ports. A port value of 0 represents ICMP.
Traffic flows on the selected ports generate alerts.
Volume
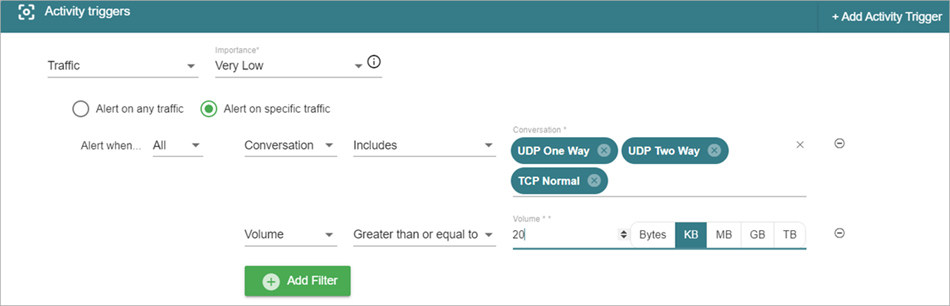
Volume represents the amount of bytes of traffic seen in a 30 minute period. To reduce the number of generated alerts, you can increase the volume threshold for specific types of authorized activity.
For example, you might have a social media sites policy that generates policy alerts if the volume of traffic is over 1 KB of data in a 30 minute period. The 1 KB threshold ignores very small amounts of activity.
However, if your employees use other websites that include ads from an unauthorized website, these ads might send and receive more than 1 KB of data in a 30 minute period. Users cannot avoid the ads because the authorized page loads them. In this scenario, you can increase the volume threshold to 10 or 20 KB to reduce the number of policy alerts generated. When a policy alert is generated with this increased volume threshold, it indicates that a user has connected to a website for an unauthorized purpose and is a legitimate policy alert to review.
Filter Policies by Anomalous Events
Anomalous events generated by ThreatSync+ NDR might trigger policies. Four types of anomalous events are supported:
- High Ratio of Incoming Bytes to Incoming Packets
- High Ratio of Outgoing Bytes to Outgoing Packets
- Unusual Rate of Incoming Bytes per Flow
- Unusual Rate of Outgoing Bytes per Flow
Each of these anomaly types contains a set of events used by many default ThreatSync+ NDR policies. Some policies include a list of anomalous events that can generate an alert, such as Unusual Change in Traffic Mix.
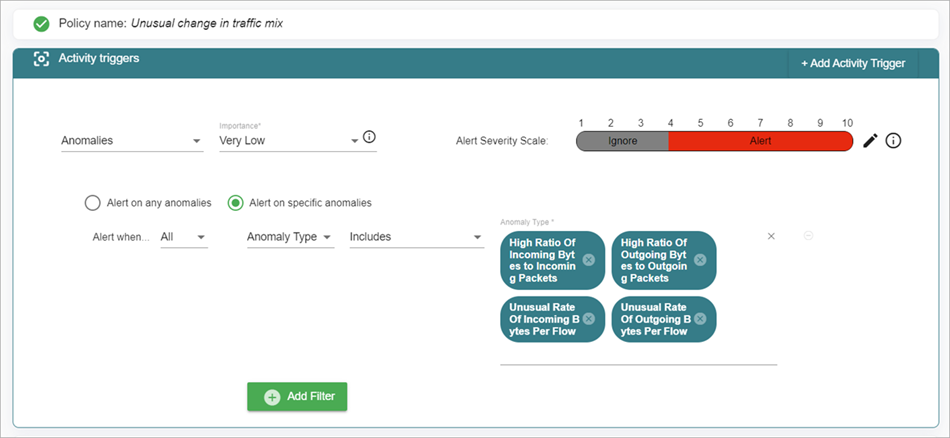
You can modify a policy to add additional events or remove events. This enables you to tune the policy to generate alerts only for the types of anomalies that are relevant to your organization.
To modify a policy to add additional events or remove events:
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Policies.
The Manage Policies page opens. - Click
 next to the policy you want to modify.
next to the policy you want to modify.
The Policy Details page opens. - Click Activity triggers to expand the section.
- In the Activity Triggers section, select Anomalies.
- From the Anomaly Type drop-down list, add or remove specific anomaly types.
Configure ThreatSync+ Policies
About ThreatSync+ Policies and Zones