Applies To: ThreatSync
As you monitor threats detected by ThreatSync and review the details of an incident or endpoint, you might decide to take action to remediate it, or to reverse an action taken automatically by a WatchGuard product or service.
To send data to ThreatSync and receive actions, Fireboxes must run Fireware v12.9 or higher and be added to WatchGuard Cloud for logging and reporting or cloud management.
ThreatSync currently only detects and reports on wireless threats. ThreatSync does not remediate wireless threat incidents to prevent connections to the malicious access point or disconnect wireless clients that have already associated to a malicious access point.
You can perform these actions manually from the ThreatSync UI:
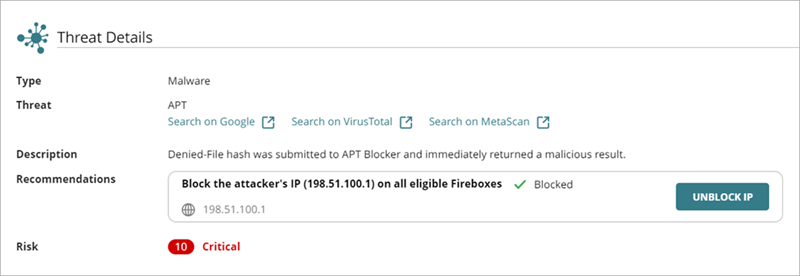
- Block IP/Unblock IP — Blocks or unblocks the external IP address associated with the incident. When you select this action, all Fireboxes in the WatchGuard Cloud account block or unblock connections to and from the IP address.
IP addresses blocked by ThreatSync do not appear on the Firebox Blocked Sites list in Fireware or WatchGuard Cloud. For more information, go to Manage IP Addresses Blocked by ThreatSync.
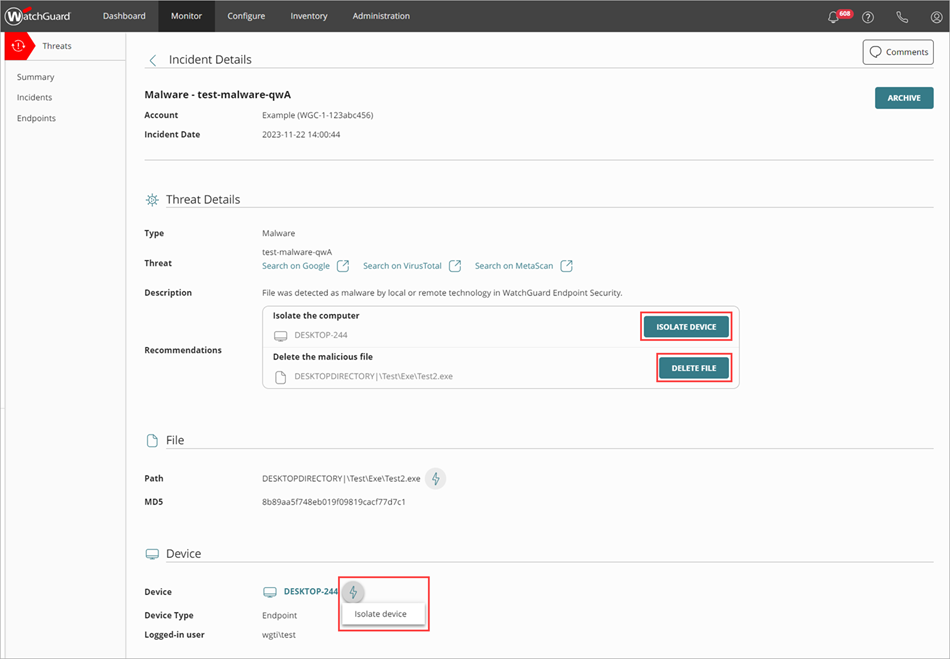
- Delete File/Restore File — Deletes the flagged file associated with the incident, or restores a previously deleted file.
- Isolate Device/Stop Isolating Device — Isolates the computer from the network to prevent the spread of the threat, and to block the exfiltration of confidential data, or stops isolating a previously isolated computer.
- Kill Process — Terminates a process that exhibited malicious behavior associated with the incident.
- Remote Control — Remotely connects to the selected Windows computer on your network to enable you to investigate and remediate a potential attack. The remote control tool requires Advanced EPDR. For more information, go to About the Remote Control Tool.
- Block/Unblock User — Blocks or unblocks the user associated with a Credential Access incident in AuthPoint. For more information on how to block users or activate blocked users in AuthPoint, go to Block a User or Token.
Not all actions apply to all incident types.
When you change the status of or perform an action on an incident, a dialog box opens with a text box to add an optional comment. These comments appear in the Comments pane on the Incident Details page. For more information, go to Review Incident Details.
Perform an Action
You can perform actions from the Incidents page, Incident Details page, and the Endpoints page.
To perform an action for one or more incidents, from the Incidents page:
- Select Monitor > Threats > Incidents.
The Incidents page opens. - Select the check box next to one or more incidents.
The Change Status and Actions menus appear. - From the Actions drop-down list, select the action to perform.
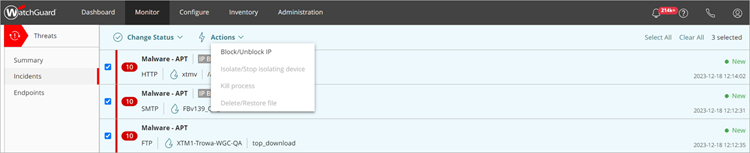
Recommendations for an incident on the Incident Details page determine what actions are available in the Actions drop-down list on the Incidents page. For example, if the recommended action for an incident is to isolate a device, the Isolate/Stop isolating device option is enabled in the Actions drop-down list.
To perform an action for an incident, from the Incident Details page:
- Select Monitor > Threats > Incidents.
The Incidents page opens. - Click an incident in the incident list.
The Incident Details page opens. - To perform an action:
- In the Threat Details section, click an action.
- In other sections, click the lightning bolt icon
 to open the action menu, then select an action.
to open the action menu, then select an action.
To perform an action for one or more endpoints, from the Endpoints page:
- Select Monitor > Threats > Endpoints.
The Endpoints page opens. - Select the check box next to one or more endpoints.
The Actions menu appears. - From the Actions drop-down list, select the action to perform.

If an error occurs and ThreatSync cannot perform an action, a red exclamation point icon or error message appears. For more information, go to Troubleshoot Incident Errors.
You can set up notifications to generate alerts when actions are performed. For more information, go to Configure ThreatSync Notification Rules.
Stop or Reverse an Action
If required, you can stop or reverse a previously performed action. For example, if you performed an action to block an IP address, you can unblock the IP address.
To stop or reverse an action, from the Incidents page:
- Select Monitor > Threats > Incidents.
The Incidents page opens. - In the left column, select the check box for one or more incidents.
The Change Status and Actions menus appear. - From the Actions drop-down list, select the action to stop or reverse.
To stop or reverse an action, from the Incident Details page:
- Select Monitor > Threats > Incidents.
The Incidents page opens. - Click an incident in the incident list.
The Incident Details page opens. - In the Threat Details section, select the action to stop or reverse.
To stop isolating an endpoint, from the Endpoints page:
- Select Monitor > Threats > Endpoints.
The Endpoints page opens. - Select the check box next to one or more endpoints.
The Actions menu appears. - From the Actions drop-down list, select Stop Isolating.
To unblock an IP address, from the IPs Blocked by ThreatSync page:
- Select Configure > ThreatSync > IPs Blocked by ThreatSync.
The IPs Blocked by ThreatSync page opens. - Select one or more blocked IP addresses.
- Click Unblock.
All eligible Fireboxes no longer block traffic to and from the selected IP addresses.
Close or Change the Status of Incidents
Manage IP Addresses Blocked by ThreatSync