Configure Automatic Intrusion Prevention
To review Automatic Intrusion Prevention settings:
- Open Discover.
- From the Navigator, select the top-level location folder. WatchGuard recommends you set the Intrusion Prevention policy settings at the top-level folder so that the settings are inherited by all subfolder locations.
- Select Configure > WIPS > Automatic Intrusion Prevention.

- The default Current Intrusion Prevention Level is set to Disrupt.
WatchGuard recommends you use the default value to disrupt unwanted communications on any two channels on the 2.4 GHz radio and any two channels on the 5 GHz radio. You can customize the level based on your deployment, but there are trade-offs between the number of channels that you can scan and the blocking effectiveness. The more channels across which simultaneous prevention is applied, the less effective prevention will be.
How Intrusion Prevention Stops the Six Known Wi-Fi Threat Categories
As part of your Trusted Wireless Environment, the Intrusion Prevention default settings automatically protect you from these known wireless threats, prevent your users from connecting to unauthorized Wi-Fi access points, and allow legitimate external access points to operate in the same airspace.
Rogue Access Point Protection
Rogue access points are unauthorized APs that are physically connected to the authorized network, usually with an open SSID that enables attackers to bypass perimeter security. Rogue access points can be a physical access point (AP), or a hotspot created in software on a computer and bridged to the authorized network.
By default, the Intrusion Prevention policy is already configured to prevent connections to Rogue APs.

Rogue Client Protection
Rogue clients are clients that connected to a rogue AP or other malicious AP within the range of the private wireless network. This client could have been victimized by man-in-the-middle attacks, ransomware, viruses and malware, or backdoor software installation.
By default, Rogue Clients are not permitted to connect to Authorized APs. You can also enable these Intrusion Prevention settings for Rogue Clients:
- Prevent Rogue Client connection to Guest APs
- Prevent Rogue Client in Bridging/ICS configuration or part of an Ad Hoc network


Neighbor AP Protection
A Neighbor access point is an External AP that is not managed or under the control of your network. These neighbor APs are located in close proximity to your authorized wireless network but are not connected to your network.
Company-managed Wi-Fi clients must never be allowed to connect to nearby third-party or neighbor SSIDs. This enables clients to bypass important network security controls.
By default, authorized client connections to External (Neighbor) APs are not permitted.

Ad-Hoc Connection Protection
An Ad-hoc Connection is a peer-to-peer Wi-Fi connection between clients that can circumvent perimeter security and allow clients to evade firewalls, content controls, and security policies.
By default, Authorized Clients cannot participate in an ad-hoc network.
In addition, you can optionally enable these settings for greater security:
- Guest Clients participating in any ad-hoc network
- Rogue Clients participating in any ad-hoc network

Evil Twin AP Protection
An Evil Twin access point mimics a legitimate AP by spoofing its SSID and unique MAC address. This can be a physical access point, or attackers can use software that uses Wi-Fi network adapters in laptops and mobile devices to create a hotspot.
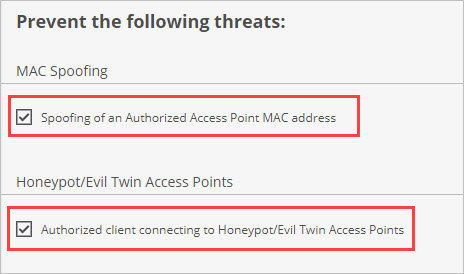
By default, Threat Prevention blocks Authorized Client connections to Honeypot/Evil Twin APs.
In addition, you can optionally enable MAC Spoofing protection to prevent spoofing of any Authorized AP’s MAC address.
Misconfigured AP Protection
Misconfigured access points are APs connected to your private network with a configuration that does not conform to your Authorized WiFi Policy and allows insecure connections. For example, if your security policy is configured to only allow SSIDs to broadcast on your authorized APs with WPA2 encryption, and an administrator accidentally misconfigures an authorized AP to broadcast an open, unencrypted SSID, that AP would be considered misconfigured.
By default, connections to Misconfigured Authorized APs are blocked.
