Applies To: WatchGuard Advanced EPDR, WatchGuard EPDR, WatchGuard EDR
You can assign Endpoint Access Enforcement settings only to Windows servers or workstations.
Endpoint Access Enforcement monitors connections to computers on your network to reduce threats from unprotected devices (Windows, Mac, and Linux). In an Endpoint Access Enforcement settings profile, you configure settings to specify the conditions that identify a computer at risk and an action to take for inbound connections from computers at risk. By default, Endpoint Access Enforcement monitors inbound connections for SMB and RDP traffic. You can specify additional protocols to monitor for inbound connections.
With Advanced EPDR, EPDR, and EDR, you can monitor inbound connections from computers at risk in the Endpoint Access Enforcement dashboard. You can use the information from the dashboard to take action on the at-risk devices. For more information, go to Endpoint Access Enforcement Dashboard.
With Advanced EPDR, you can also block connections from computers at risk.
System Requirements
To use Endpoint Access Enforcement, make sure that your computer meets these system requirements:
-
WatchGuard Agent: To monitor inbound connections from computers at risk, the computer must have Advanced EPDR, EPDR, or EDR v 4.40 or higher installed. To block connections from computers at risk, it must have Advanced EPDR v4.40 or higher installed.
-
Operating System: Endpoint Access Enforcement is compatible with Windows computers.
Computers with a macOS or Linux operating system and Advanced EPDR v4.40 or higher report the status of the security software to Windows computers that evaluate their risk level.
-
Open Ports on the Computer: The WatchGuard Agent installed on the computer must be able to communicate with other computers over TCP port 33000.
Add Allowed IP Addresses to Service Provider Settings
By default, you cannot edit or delete the Endpoint Access Enforcement settings assigned by your Service Provider. If your Service Provider configures the allowed IP addresses for a protocol to be editable, then the settings profile shows the label, Editable Protocols, and you can add allowed IP addresses. You cannot delete or edit the list defined by the Service Provider. This could be useful for internal servers or servers with frequent connections to workstations, such as backup servers and Active Directory servers, that you do not want WatchGuard Endpoint Security to audit or block (Advanced EPDR only).
If your Service Provider changes the status of the settings from editable to non-editable, any allowed IP addresses you added no longer apply, and only the allowed IP addresses from the Service Provider apply. If the Service Provider changes the configuration again to be editable, then the allowed IP addresses you added are restored and applied.
Configure Endpoint Access Enforcement Settings
To configure Endpoint Access Enforcement settings:
- In WatchGuard Cloud, select Configure > Endpoints.
- Select Settings.
- From the left pane, select Endpoint Access Enforcement.
- Select an existing security settings profile to edit, copy an existing profile, or in the upper-right corner of the window, click Add to create a new profile.
The Add Settings or Edit Settings page opens.
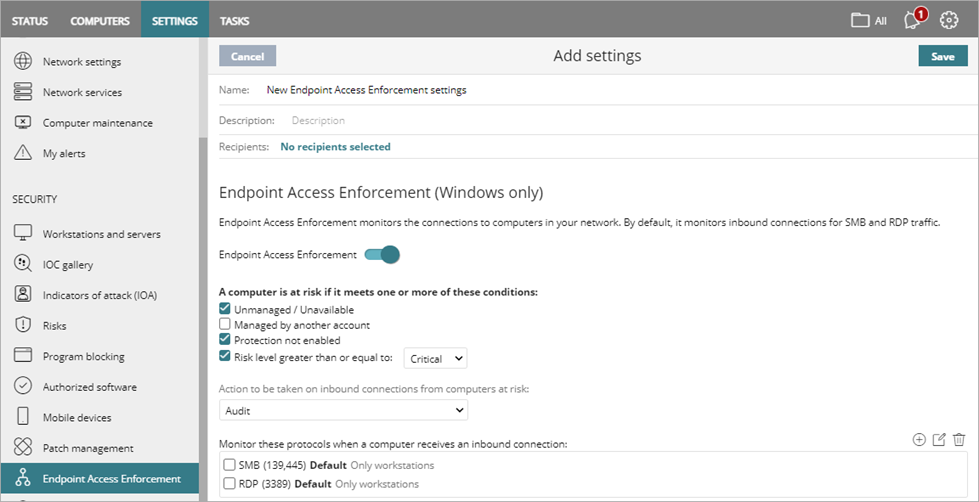
- Enter a Name and Description for the profile, if required.
- Select the conditions that identify a computer at risk:
- Unmanaged/Unavailable — Detected computer does not have Advanced EPDR, EPDR, or EDR installed or is unavailable for connection. Make sure the protection meets the minimum requirements. For more information, go to System Requirements.
- Manged by Another Account — Detected computer has Advanced EPDR, EPDR, or EDR installed but is managed by another account.
- Protection Not Enabled — Detected computer has Advanced EPDR, EPDR, or EDR installed but the protection software is disabled.
- Risk Level Greater than or Equal to: — Detected computer risk level is greater than or equal to the severity you select:
- Medium — Indicates that additional risk factors were found that you should address.
- High — Indicates that latent malware was found that could execute at any time or indicates that there is an urgent need to reduce the attack surface.
- Critical — Indicates that confirmed malware was executed or indicates that there is a dangerous level of exposure to a cyberattack.
- Select the action to take when Endpoint Access Enforcement detects a connection from a computer at risk:
- Audit — Reports detected inbound connections, but does not block the connection. This is the default action. Detected connections show in the Endpoint Access Enforcement dashboard. For more information, go to Endpoint Access Enforcement Dashboard.
- Block — Reports and blocks detected inbound connections. (Advanced EPDR only)
- (Optional) To change the default protocols you want to monitor, from the Monitor These Protocols When a Computer Receives an Inbound Connection section, add, edit, or delete an existing protocol.
Endpoint Access Enforcement monitors only the standard TCP/UDP ports associated with the selected protocol.
- To add a new protocol, click
 . To edit an existing protocol, select the protocol and click
. To edit an existing protocol, select the protocol and click  .
.
The Configure Protocol dialog box opens.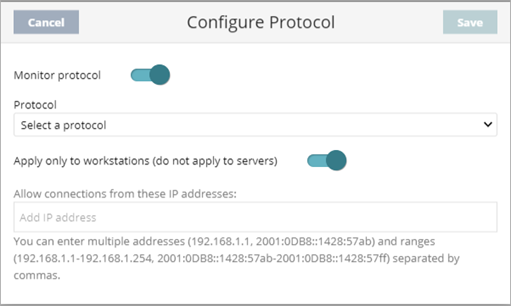
- From the Protocol drop-down list, select the traffic protocol for the port numbers you want to monitor.
The standard TCP/UDP ports associated with the selected protocol show in the Ports text box.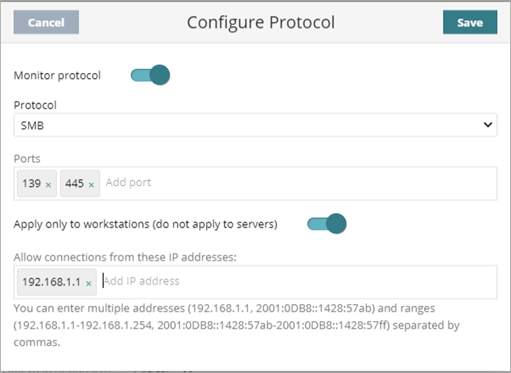
- If required, in the Ports text box, add or remove ports.
- To monitor connections to servers, disable Apply Only to Workstations (Do Not Apply to Servers).
- To always allow connections from specific IP addresses, enter the IPv4 or IPv6 addresses or ranges in the text box.
- Click Save.
The protocol shows in the list. To delete a protocol, select the protocol and click .
.
- To add a new protocol, click
- (Advanced EPDR) If you selected the Block action, you can show local alerts on the endpoint device.
- To show local alerts on the endpoint device when Endpoint Access Enforcement detects a connection from a computer at risk, enable Show an Alert When Endpoint Access Enforcement Detects a Connection.
The custom alerts text box appears.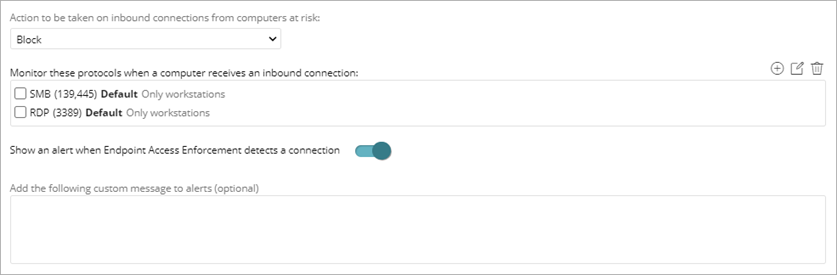
- To add a custom message for the alert, in the text box, type a message.
- To show local alerts on the endpoint device when Endpoint Access Enforcement detects a connection from a computer at risk, enable Show an Alert When Endpoint Access Enforcement Detects a Connection.
- Click Save.
- Select the profile and assign recipients, if required.
For more information, go to Assign a Settings Profile.