Some of the features described in this topic are only available to participants in the WatchGuard Cloud Beta program. If a feature described in this topic is not available in your version of WatchGuard Cloud, it is a beta-only feature.
For a cloud-managed Firebox or FireCluster, system settings include:
- Firebox Name
- Time Zone
- NTP Servers
- Device Feedback
- FireCluster Settings (Identification, Interface, and Communication Settings) (FireClusters only)
- TCP MTU Probing
- SNMP Settings
- NetFlow Settings
On the Device Configuration page for a cloud-managed Firebox or FireCluster, the Settings tile shows a summary of configured system settings.

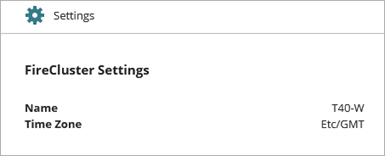
When you add a Firebox to WatchGuard Cloud as a cloud-managed device, you configure the Firebox name and time zone. Three NTP servers are automatically added to the configuration. You can use the three default NTP servers, or you can remove them and specify different NTP servers, but you must have at least one NTP server.
You can optionally enable your Firebox as an NTP server. When you enable the Firebox as an NTP server, client devices on your private networks can contact the Firebox to synchronize the time. When you enable the Firebox as an NTP server, the NTP Server policy is automatically created, if an NTP policy does not already exist. This policy allows NTP traffic from client devices on your trusted and optional networks to the Firebox.
For client devices to use your Firebox as an NTP server, you must configure them to get the time from the Firebox. On Windows and macOS, you configure this in the date and time settings. In the date and time settings, configure the client devices to get the date and time from the IP address of an internal network on your Firebox, or from a domain name that resolves to the IP address of the internal network.
Firebox devices also return detailed device feedback by default. For information on how to configure device feedback settings, go to Configure Device Feedback Settings (WatchGuard Cloud).
To view and update FireCluster settings for a cloud-managed FireCluster, go to Edit the FireCluster Settings.
To see and update the device settings for a Firebox:
- In WatchGuard Cloud, select Configure > Devices.
- Select the cloud-managed Firebox.
- Click Device Configuration.
- In the Settings tile, click the Device Settings widget.
The Settings page opens.
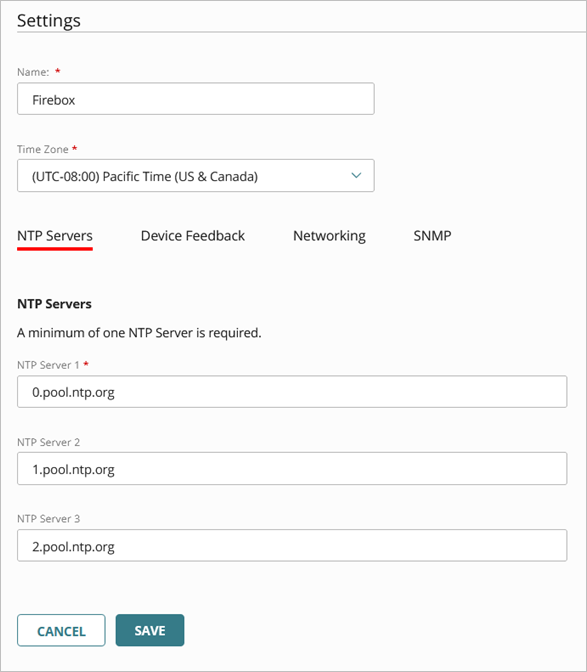
- In the Name text box, edit the Firebox name.
- From the Time Zone drop-down list, select the time zone at the location where the Firebox is installed.
- If you want to change NTP servers, on the NTP Servers tab, remove one or more of the default servers and enter the addresses of the NTP servers you want to use.
- If you want to use this Firebox as an NTP server for your private network, select the Enable This Device as an NTP Server check box.
WatchGuard Cloud automatically creates the NTP Server policy, if an NTP policy does not already exist.If you want client devices on your private network to use the Firebox as an NTP server, you must also configure the client devices to get the time from the Firebox.
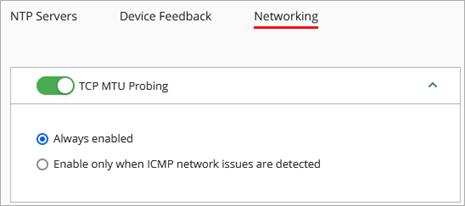
- If you want the Firebox to automatically change the size of its data packets as necessary, on the Networking tab, enable TCP MTU Probing.
When you enable this global option, the Firebox can automatically change the size of its data packets to make sure that PMTU discovery succeeds and to avoid reduced performance caused by fragmentation. For example, you might enable TCP MTU Probing in these cases:
- You have a slow PPPoE connection and require smaller packets to optimize performance.
- You want to make sure that client devices on your network can access the Internet through a zero-route BOVPN tunnel on this Firebox even if the Path Maximum Transmission Unit (PMTU) discovery process cannot complete. For example, if a remote router drops a packet but does not send an ICMP Destination Unreachable or ICMP Fragmentation Needed response to the Firebox, an ICMP black hole occurs and the PMTU process cannot complete. If you enable TCP MTU probing, an ICMP black hole does not affect traffic through the zero-route BOVPN.
When you enable TCP MTU Probing, select one of these options:
- Always Enabled
- Enable Only When ICMP Network Issues are Detected — Automatically enable TCP MTU Probing only when an ICMP error message is dropped and the PMTU discovery process cannot complete. After the problem resolves, TCP MTU Probing remains enabled.
- On the SNMP tab, configure your settings for SNMP polling and SNMP traps and notifications. For more information, go to Configure SNMP Settings for a Cloud-Managed Firebox.
- On the NetFlow tab, configure the settings to send flow records to your NetFlow collector for analysis. For more information, go to Configure NetFlow Settings for a Cloud-Managed Firebox.
- To save configuration updates to the cloud, click Save.
Add a Cloud-Managed Firebox to WatchGuard Cloud
Add a Cloud-Managed FireCluster
Configure Device Feedback Settings (WatchGuard Cloud)
Configure Log Server Settings for Cloud-Managed Fireboxes