BlueSky is yet another Conti v2 derivative. However, this variant isn't a direct clone. The threat actors behind the BlueSky ransomware appear to have taken some inspiration from other big-named ransomware. For example, researchers state that much of the codebase is shared with Conti v2, but some researchers speculate that the encryption routine is similar to Babuk. Additionally, other researchers highlight the similarities with the TargetCompany ransomware. The WatchGuard Threat Lab performed its own technical analysis to get to the bottom of it. We determined that the code base most resembles Conti v2, so we designated the official Lineage as just that. It's certainly possible that the threat actors drew inspiration from Babuk and TargetCompany.
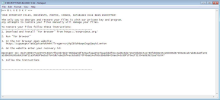
Through open-source research, we were able to locate 9 samples of BlueSky, all with similar features and ransom notes. Interestingly, BlueSky drops 2 ransom notes - "# DECRYPT FILES BLUESKY #.html" and "# DECRYPT FILES BLUESKY #.txt." Both ransom notes display the same information but in different formats. In addition to dropping the ransom notes, BlueSky encrypts files using ChaCha20 and RSA-4096 to perform file encryption. However, it also uses Curve25519 for key generation, which is where the Babuk similarities lie. After encryption, it renames files to include bluesky at the end (<file name>.bluesky).
The threat actors created a dark web domain for extortion negotiations where they also blackmailed victims into paying quickly, or prices would increase. However, we found no evidence that they posted these extortions publicly, and thus they never performed double extortions. This ransomware was active from late June 2022 until early 2023. We noticed the last instance of a BlueSky ransomware attack in January 2023.